cyberwar
Latest

The only way to stop another WannaCry is with regulations
It's been one week since the newest (and therefore scariest) cyberattack, which caused pandemonium across Ukraine and Russia before spreading to other countries. But that came only a few weeks after the WannaCry ransomware targeted Windows XP machines worldwide, which infamously held data from the UK's National Health Service hostage. You might think we've entered a new era of cyberattacks, one that could threaten all of the machines in your home and every internet-connected service you rely on.

The looming specter of cyberwar with Russia
In the world of cyber (as in security), the question of the week seems to be, "Are we going to cyberwar with Russia?" White House Press Secretary Josh Earnest thinks so. A week after President Obama singled out Russia as being responsible for cyberattacks on targets including the Democratic National Committee, Earnest said in a briefing that the administration would be serving a "proportional" response to Putin and the gang.

Alex Gibney on Stuxnet and why we need to talk about cyberwar
It's been six years since we discovered Stuxnet, the worm that infected Windows PCs worldwide and was eventually traced to the United States and Israel as a way to attack Iran's nuclear program. It was the first time a cyberweapon was used to attack a physical location (it disabled uranium enriching centrifuges by causing them to spin out of control), and it sparked the use of cyberattacks from governments all over the world, including Russia, Iran and North Korea. Alex Gibney, the acclaimed documentarian behind films like Taxi to the Dark Side, Enron: The Smartest Guys in the Room, and the recent Steve Jobs: The Man in the Machine, decided to dive into Stuxnet's legacy with his latest film, Zero Days. I sat down to chat with him about the film, together with Symantec researchers Eric Chien and Liam O'Murchu.
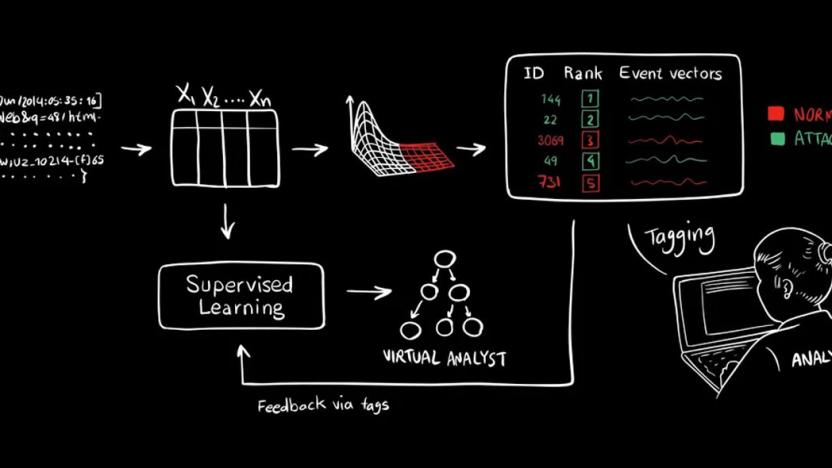
MIT's digital lookout in the crows nest of cyber warfare
"Think about the system as a virtual analyst," says Kaylan Veermachaneni, co-creator of MIT's latest artificial intelligence. He's a research scientist at the university's Computer Science and Artificial Intelligence lab that, along with Ignacio Arnaldo, built an AI that acts as a lookout for the age of cyber warfare. AI2 (Short for Artificial Intelligence Squared) is a system designed to spot a hacking attack better than humans and existing software. They claim that the program can detect 85 percent of malicious attacks, although that figure is set to rise the more it learns. We can already imagine Sony's IT gurus beating a path to Massachusetts with a suitcase stuffed full of unmarked bills.

Report: ISIS's Twitter propaganda efforts have stalled
The Islamic State isn't having much luck recruiting new members online these days. Twitter suspended 125,000 accounts sympathetic to the jihadist organization between June and October of last year and it appears to be making an impact, according to a study being released Thursday by George Washington University's Program on Extremism.

The White House officially launches its new cyber warfare agency
One of the reasons that the US has been slow to respond to attacks is because its security agencies don't talk to each other. This lack of communication may make the FBI, CIA etc look very butch, but it's pretty terrible when lives, businesses and second-tier studio comedies are on the line. This is why the White House has sanctioned the creation of a new agency that's designed to remedy the problem. The US Cyber Threat Intelligence Integration Center has been given the official go-ahead, and will sit between the FBI, NSA and CIA, amongst others, collating that data and offering a cohesive policy to fight off digital attacks. Another thing the CTIIC will be responsible for is informing both lawmakers and US businesses of impending threats and advise upon solutions, maybe starting with "don't make movies about North Korea without making sure your network is full of holes."

The Army may ditch fitness tests for unfit, 'ponytail-wearing' hackers
It's a truth, often forgotten, that no-one can be perfect at everything. We may laud Justin Timberlake's musical, dancing and acting ability, but he's probably a terrible plumber. It's a problem that the Army is beginning to understand, since the sort of people who can successfully fight in a cyber war are more likely to be bad at assault courses, climbing ropes and carrying heavy objects. It's with this in mind that Lt. Gen. Robert Brown, head of the Combined Arms Center at Fort Leavenworth, says that the US Army may relax its fitness requirements for digital soldiers.

NSA Director nominee wants every branch of the military to have a dedicated cyber attack force
It seems like President Obama was pretty serious about that cyber attack list he drew up last year -- his nominee candidate for NSA Director, Admiral Michael Rogers, just told the Senate that the military is building several new cyber combat units. Rogers, who is slated to both take over at the NSA and head the United States Cyber Command, spent several hours answering to the Senate Armed Services Committee this week, explaining his views on national security and his desire to be "as transparent as possible with the broader nation about what we're doing, and why." This included a detailed account of the need to create dedicated cyber attack divisions to supplement traditional ground, naval and air forces, which he says will help act as a deterrent to countries that see the United States as an easy target. "Clearly, Cyber will be an element of almost any crisis we're going to see in the future," he told the Senate. "It increasingly is becoming a norm."

Tallinn Manual defines the legal groundwork for cyberwarfare
The advent of cyberwarfare raises any number of legal quandaries, let alone ethical ones: when it's possible to do serious damage without crossing a border or firing a shot, where do you stop? NATO's Cooperative Cyber Defence Centre of Excellence (CCDCOE) is publishing the finished version of a non-binding guide, the Tallinn Manual, that could settle at least the legal disputes. For the most part, it demands a measured, one-for-one response and attempts to minimize collateral damage. Digital retaliation is appropriate if the state is a victim of a hacking attack, but bombs and guns should only come into play if virtual combat leads to real casualties. Any attacks should likewise steer clear of civilians, and simply having the capacity or desire for a hacking campaign doesn't make someone a target -- there has to be an "imminent" threat to justify a preemptive strike. NATO isn't formally adopting the Tallinn Manual as policy, and it's difficult to know whether the organization's member nations (or any other country) would honor the guidelines when parties on all sides have been pushing the boundaries of cyberwarfare for years. Still, we'll have to start somewhere if we want to draw a line in the silicon. [Image credit: US Army, Flickr]

China claims its defense sites face constant US hacking attacks
China is routinely accused of launching concerted hacking campaigns against the US, many of them reportedly tied directly to the army's Unit 61398 in Shanghai. If you believe the Ministry of Defense's spokesman Geng Yansheng, however, just the opposite is true. Along with claiming that China would never hurt (or rather, hack) a fly, he asserts that the Ministry and China Military Online sites faced an average of 144,000 hacking attempts per month from foreign sources in 2012, 62.9 percent of which allegedly came from the US. The Ministry's man stops short of leveling cyberwarfare charges, although he notes the US' recent plans to expand and formally define its cyberwar strategy. There's some 'splainin to do, he argues. While there isn't a formal US response, we suspect that neither side is an innocent dove here -- China is just the most recent to cry foul.

Kaspersky Labs preps its own OS to guard vital industry against cyberwarfare
Kaspersky Labs' namesake Eugene Kaspersky is worried that widely distributed and potentially state-sponsored malware like Flame and Stuxnet pose dire threats to often lightly protected infrastructure like communication and power plants -- whatever your nationality, it's clearly bad for the civilian population of a given country to suffer even collateral damage from cyberattacks. To minimize future chaos and literally keep the trains running, Kaspersky and his company are expanding their ambitions beyond mere antivirus software to build their own, extra-secure operating system just for large-scale industry. The platform depends on a custom, minimalist core that refuses to run any software that isn't baked in and has no code outside of its main purposes: there'll be no water supply shutdowns after the night watch plays Solitaire from an infected drive. Any information shared from one of these systems should be completely trustworthy, Kaspersky says. He doesn't have details as to when the OS will reach behind-the-scenes hardware, but he stresses that this is definitely not an open-source project: some parts of the OS will always remain confidential to keep ne'er-do-well terrorists (and governments) from undermining the technology we often take for granted.

Iran claims to have been hit by 'heavy' cyber attack, pins slowdowns on coordinated hacking campaign
Whatever you think of Iran's politics, it's hard to deny that the country has frequently been the target of internet-based attacks that sometimes go beyond the originator's plans. If you believe High Council of Cyberspace secretary Mehdi Akhavan Behabadi, the pressure is only getting worse. He tells Iranian media that the nation is under "constant" digital bombardment and was just hit with a major assault on Tuesday that bogged down local internet access. Behabadi unsurprisingly contends that the attacks are deliberate efforts to undermine Iran's data, nuclear and oil infrastructures, with a finger implicitly pointed westward. While it's no secret that the country's enemies want to slow down what they see as a rush towards nuclear weapons, it's difficult to know how much of the accusation is serious versus bluster: we've seen individual smartphone users who consume more than the "several gigabytes" of traffic that reportedly caused national chaos in the most recent incident. No matter the exact nature, it's likely that residents stand to lose as Iran fences off the internet to keep outside influences, hostile and otherwise, from getting in. [Image credit: Amir1140, Wikipedia]

Flame malware extinguishes itself, Microsoft protects against future burns
The folks behind that nasty Flame trojan that burned its way through the Middle East aren't the kind to brag -- the malware's manufacturers apparently started dousing their own fire last week. According to Symantec reports, several compromised machines retrieved a file named browse32.ocx from Flame controlled servers, which promptly removed all traces of the malware from the infected systems. Although the attackers seem spooked, Microsoft isn't taking any chances, and has issued a fix to its Windows Server Update Services to block future attacks. The update hopes to protect networked machines from a similar attack by requiring HTTPS inspection servers to funnel Windows update traffic through an exception rule, bypassing its inspection. The attackers? "They're trying to cover their tracks in any way they can," Victor Thakur, principal security response manager at Symantec told the LA Times, "They know they're being watched." Check out the source link below for the Symantec's run down of the trojan's retreat.

Google starts warning affected users about state-sponsored cyber attacks
The fallout from malware like Stuxnet and Flame might soon be rearing its head at a Google Plus page or Gmail inbox near you. A post on its online security blog states that Google will now issue warnings in the form of a strip placed just below the upper menu bar to users being targeted by suspected state-sponsored cyber attacks. Google stressed that such warnings don't mean that its systems have been compromised but it does make it highly likely that the recipient may be the target of state-sponsored phishing or malware. How exactly does Google know this to be the case? The company declined to offer specifics, only saying that data from victim reports and its own analysis strongly point toward the involvement of states or state-sponsored groups. Google also didn't mention how often it sees such malicious activity, though coverage of Stuxnet and Flame certainly has put a spotlight on cyber warfare involving nations. In the meantime, feel free to hit the source link below for Google's tips on how to secure your account.

Stuxnet pinned on US and Israel as an out-of-control creation
Ever since Stuxnet was discovered, most of the accusing fingers have been pointed at the US, Israel or both, whether or not there was any evidence; it was hard to ignore malware that seemed tailor-made for wrecking Iranian centrifuges and slowing down the country's nuclear development. As it turns out, Occam's Razor is in full effect. An exposé from the New York Times matter-of-factly claims that the US and Israel coded Stuxnet as part of a cyberwar op, Olympic Games, and snuck it on to a USB thumb drive that infected computers at the Natanz nuclear facility. The reason we know about the infection at all, insiders say, is that it got out of control: someone modified the code or otherwise got it to spread through an infected PC carried outside, pushing Obama to either double down (which he did) or back off. Despite all its connections, the newspaper couldn't confirm whether or not the new Flame malware attack is another US creation. Tipsters did, however, deny that Flame is part of the Olympic Games push -- raising the possibility that there are other agencies at work. [Image credit: David Holt, Flickr]

Flame malware snoops on PCs across the Middle East, makes Stuxnet look small-time
Much ado was made when security experts found Stuxnet wreaking havoc, but it's looking as though the malware was just a prelude to a much more elaborate attack that's plaguing the Middle East. Flame, a backdoor Windows trojan, doesn't just sniff and steal nearby network traffic info -- it uses your computer's hardware against you. The rogue code nabs phone data over Bluetooth, spreads over USB drives and records conversations from the PC's microphone. If that isn't enough to set even the slightly paranoid on edge, it's also so complex that it has to infect a PC in stages; Flame may have been attacking computers since 2010 without being spotted, and researchers at Kaspersky think it may be a decade before they know just how much damage the code can wreak. No culprit has been pinpointed yet, but a link to the same printer spool vulnerability used by Stuxnet has led researchers to suspect that it may be another instance of a targeted cyberwar attack given that Iran, Syria and a handful of other countries in the region are almost exclusively marked as targets. Even if you live in a 'safe' region, we'd keep an eye out for any suspicious activity knowing that even a fully updated Windows 7 PC can be compromised.

Robert Morris, man who helped develop Unix, dies at 78
We have some somber news to bring you this morning: Robert Morris, the cryptographer who helped create Unix, has died at the age of 78. Morris began his work on the groundbreaking OS back in 1970 at AT&T's Bell Laboratories, where he played a major role in developing Unix's math library, password structure and encryption functions. His cryptographic exploration continued into the late 1970s, when he began writing a paper on an early encryption tool from Germany. But the paper would never see the light of day, thanks to a request from the NSA, which was concerned about potential security ramifications. Instead, the agency brought Morris on board as a computer security expert in 1986. Much of what he did for Uncle Sam remains classified, though he was involved in internet surveillance projects and cyber warfare -- including what might have been America's first cyberattack in 1991, when the US crippled Saddam Hussein's control capabilities during the first Gulf War. Morris stayed with the NSA until 1994, when he retired to New Hampshire. He's survived by his wife, three children and one, massive digital fingerprint. [Image courtesy of the New York Times]

China Telecom re-routes 15% of the world's Internet traffic for a full 18 minutes, hopes no one noticed
On April 8 of this year there was an approximately eighteen minute long period of time where China Telecom advertised erroneous network traffic routes, causing foreign Internet traffic to travel through Chinese servers. According to a congressional panel, about fifteen percent of the world's Internet traffic was diverted -- including that of the US government and military, and a number of commercial websites. As always seems to be the case when we're talking about The People's Republic, there are few things that can be said for certain, while a ton of questions linger: was this really just a mistake, or was someone flexing their muscles? Could this have been a diversion "intended to conceal one targeted attack," as Arbor Networks Chief Security Officer Danny McPherson suggested? We don't know, but this is the country that brought us both iorgane and buses that drive over cars, so we suppose anything's possible.

Charlie Miller and Kim Jong-Il could pwn the Internet with two years, $100 million
Well there's one thing we can say about Charlie Miller -- he sure is an ambitious rascal. When not busy exposing security holes in OS X, our fave security expert (aside from Angelina Jolie in Hackers, of course) has laid out a shocking expose based on the following premise: if Kim Jong-Il had a budget of $100 million and a timeline of two years could North Korea's de facto leader (and sunglasses model) take down the United States in a cyberwar? It seems that the answer is yes. Using a thousand or so hackers, "ranging from elite computer commandos to basic college trained geeks," according to AFP, the country could target specific elements of a country's infrastructure (including smart grids, banks, and communications) and create "beacheads" by compromising systems up to two years before they pulled the trigger. Speaking at DEFCON this weekend, Miller mentioned that such an attack could be carried out by anyone, although North Korea has a few advantages, including the fact that its infrastructure is so low tech that even destroying the entire Internet would leave it pretty much unscathed. That said, we're not worried in the least bit: if the diminutive despot brings down the entire Internet, how is he ever going to see Twilight: Eclipse?

Defense Department developing portable hacking device for soldiers
It's not exactly news that the Department of Defense is looking at ways to make hacking a more practical weapon, but it looks to really be stepping up its game with its latest project, which promises to make complicated attacks as simple as a few button presses. That would apparently be possible thanks to a slightly mysterious device that'd be small enough to carry around in a backpack, but powerful enough to do everything from breaking into a wireless network to hacking into SCADA (or Supervisory Control and Data Acquisition) systems (used at power plants, nuclear facilities, and the like). While complete details are obviously a bit light, the system would apparently be able to, for instance, map out the nodes in a wireless network, cause them to disconnect, and watch them come back online to identify weak spots. It would then present the "hacker" with various attack attributes that could simply be adjusted using sliders on a touchscreen. No word if the soldiers will also be rewarded with Achievements.[Via Softpedia]








