SecurityBug
Latest
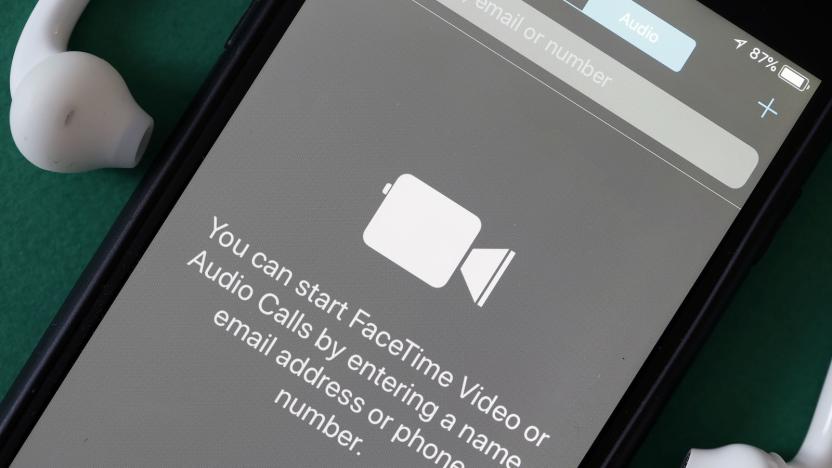
A 14-year-old tried to warn Apple about the group FaceTime bug
Before the FaceTime bug that lets people listen in to others before the call starts blew up yesterday, a 14-year-old Arizona high schooler tried to warn Apple of the issue. According to the Wall Street Journal, Grant Thompson and his mother Michele spent more than a week trying to contact Apple but didn't make much progress with the company while trying to report the bug.

Twitter bug exposed private tweets of some Android users for five years
A bug that has plagued Twitter since 2014 exposed the tweets of some Android users that were intended to be private. Twitter first disclosed the issue on its Help Center today after apparently fixing the issue on January 14th. The bug didn't affect people using Twitter on iOS or desktop.

Google triples max bounty for Chrome bugs to make the browser safer for users
Google has long been rewarding anyone who can dig up Chrome browser bugs with a nice amount of cash, but the longer the reward program runs, the harder it is to find vulnerabilities. Thus, Mountain View's upping the max reward a dedicated bounty hunter can get to $15,000 for each high-quality report -- not as big as the $110,000 reward it offered for Chrome OS security bugs in January, but still 10 grand more than the previous $5,000 max. Also, recipients can now prove to their doubtful friends that they've indeed made Chrome a safer browser for them, as they'll now be listed in the program's new Hall of Fame page.

iOS 7 bug lets you call any number from a locked homescreen (video)
You can expect three things every time a new iOS version comes along: fresh aesthetics, features and, by the looks of it, ways to bypass a locked screen. In iOS 7's case, this is the second security flaw unearthed since it's launched: An iPhone user named Karam Daoud recently discovered that you can dial any number on the Emergency call page from a locked homescreen. If you press the green phone button repeatedly after keying in a number, the screen turns black with an Apple logo, and the call goes through. We've tested it out on different devices, and while it doesn't work all the time, the point is that it sometimes does. There's no apparent way to disable Emergency calls, but Apple reportedly told Daoud it'll issue a patch later. We've reached out to Cupertino for a statement, and we'll inform you once we hear back. Meanwhile, if you've been hearing about another supposed iOS 7 exploit that allows Siri to make calls, send text messages and post to social networks from a locked screen, don't worry too much. It's not actually a bug -- just go to Settings > General > Passcode Lock > Allow access when locked, then switch Siri off. After you do that, no mischievous sibling should be able to post embarrassing status updates on your Facebook account. That is, unless you do it yourself after a night of drunken revelry.

Facebook security bug exposed 6 million users' personal information (update)
Today, Facebook announced a security bug that compromised the personal account information of six million users. In a post on the Facebook Security page, the site's White Hat team explained that some of the information the site uses to deliver friend recommendations was "inadvertently stored with people's contact information as part of their account on Facebook." When users downloaded an archive of their account via the DYI (download your information) tool, some were apparently given access to additional contact info for friends and even friends of friends. The post continues: We've concluded that approximately 6 million Facebook users had email addresses or telephone numbers shared. There were other email addresses or telephone numbers included in the downloads, but they were not connected to any Facebook users or even names of individuals. For almost all of the email addresses or telephone numbers impacted, each individual email address or telephone number was only included in a download once or twice. This means, in almost all cases, an email address or telephone number was only exposed to one person. Additionally, no other types of personal or financial information were included and only people on Facebook – not developers or advertisers – have access to the DYI tool. Facebook says it's temporarily disabled the DYI tool to fix the breach. We've reached out to the site for further comment; for now, read the official statement via the source link below. Update: Facebook has responded to our inquiries and stated that while the bug was discovered earlier this month, "it had been live since last year." They immediately disabled the tool, fixed the bug and reenabled it within 24 hours of the bug's discovery. The bug was reported to them through a White Hat program for external security researchers.


