Trojan
Latest

BloodyStealer trojan targets Steam, GOG and Epic accounts
A new trojan called BloodyStealer is targeting gamer's accounts on EA Origin, Steam, Epic Games, GOG and other services, according to Kaspersky.
Google removes popular Android apps that stole Facebook passwords
Google has pulled nine Android apps that stole Facebook passwords, but only after they'd racked up 5.8 million downloads.

Russian hackers target governments in Europe and South America
Russia's Fancy Bear hacking team (aka APT28) isn't just focused on meddling with elections and retaliating against anti-doping agencies. Symantec has observed Fancy Bear conducting intelligence gathering hacks in Europe and South America, including governments, military targets, an embassy and a "well-known international organization." The group has been using a common set of tools to conduct the campaign, although it also recently expanded its repertoire to include hacks that are considerably harder to stop.

'Major scale' malware targets your Mac through email scams
Mac users are increasingly being targeted by malware after years of being relatively safe, and that means they're facing attacks that other users have unfortunately come to expect for a while. Check Point researchers have discovered Dok, the first "major scale" trojan that targets macOS through an email phishing campaign. The bogus messages (usually aimed at European users) are meant to trick you into downloading a ZIP file that, if you launch it, gives the malware control over your system and lets attackers intercept your internet traffic to spy on your activity or impersonate websites. It'll even delete itself when the intruders are done.

Trojan uses a key internet feature to receive marching orders
If malware uses a remote command-and-control server to function, it's relatively easy to cripple it by blocking the internet addresses it uses. It's not always that easy, however, and researchers at Cisco's Talos group have found a textbook example of this in action. A recently discovered Windows PowerShell trojan, DNSMessenger, uses the Domain Name Service for communication -- you know, one of the cornerstones of the internet. Few computer users are equipped to block DNS without causing other problems, and they might not notice unusual data traffic even if they're looking for it. While using DNS isn't completely unheard of, DNSMessenger uses an "extremely uncommon" two-way approach that both sends commands to victim machines and sends results back to the attacker.

Advertising's hottest surveillance software is surprisingly legal
You may have heard that the FTC this week sent out a dozen strongly worded letters to apps using the SilverPush framework. The FTC politely told 12 app developers that they needed to let users know that SilverPush was collecting data and selling it to third parties. SilverPush responded two days ago by issuing a statement claiming it no longer uses the "Unique Audio Beacons" (UAB), and has "no active partnership with any US-based developers." Well, if this is true, then perhaps SilverPush should remove UAB as a core product from its website -- and from the heart of its business model, as well.

iOS malware uses copy protection to infect 'pure' devices
Ne'er-do-wells have so far exploited holes in Apple's FairPlay copy protection primarily to distribute pirated iOS apps, but it now looks like they're turning their energy toward hurting users. Palo Alto Networks says it has discovered AceDeceiver, the first malware that uses FairPlay to infect its targets. Install a bogus iOS management utility for Windows (Aisi Helper) and the software will launch a man-in-the middle attack that grabs app authorization codes and uses those to install infected apps on any iOS device you connect to the system. Unlike many iOS attacks, this doesn't require that the target use a jailbroken device -- the apps are allowed to run as if they were completely legitimate.

New strain of Android malware is 'virtually impossible' to remove
Do you remember the bad old days of computer viruses so invasive that it was easier to nuke your software and start over than fix the problem? They're back... in mobile form. Lookout has noticed a trend toward Android malware that masquerades as a popular app, but quietly gets root-level access to your phone and buries itself deep in the operating system. If that happens, you're in serious trouble. Unless you can walk through loading a fresh ROM or carefully modify system files over ADB, it may be easier to just replace the device, or have your phone company reflash it -- a simple factory reset won't get the job done. Some of the bogus apps are little more than shells for ads, but others will work properly while they compromise your device.

Security firm discovers Linux botnet that hits with 150 Gbps DDoS attacks
Akamai announced on Tuesday that its Security Intelligence Response Team has discovered a massive Linux-based botnet that's reportedly capable of downing websites under a torrent of DDoS traffic exceeding 150 Gbps. The botnet spreads via a Trojan variant dubbed XOR DDoS. This malware infects Linux systems via embedded devices like network routers then brute forces SSH access. Once the malware has Secure Shell credentials, it secretly downloads and installs the necessary botnet software, then connects the newly-infected computer to the rest of the hive.

Darkode cybercrime forum seized as police arrest 28 members
In a coordinated takedown, law enforcement agents around the world have teamed up to shut down the well-known cybercrime forum Darkode, pursuing 70 of its members and associates resulting in 28 arrests so far. In the US, the Department of Justice and the FBI have announced criminal charges against 12 individuals including the site's alleged admin, Johan Anders Gudmunds, aka Mafi aka Crim aka Synthet!c, and the seizure of the site's servers. Dubbed Operation Shrouded Horizon, the effort by police in 20 countries took on a forum known as a place for cyber criminals to swap tips and tools (botnets, spamming services, you name it) of the trade. Brian Krebs has been reporting on Darkode's community for quite some time, including a profile published after its administrators tricked him into publishing details on a fake Java exploit.

Cops gave a malware-laden drive to a lawyer for whistleblowers
Arkansas' Fort Smith Police Department may be responsible for some particularly sinister digital tricks, if you ask one lawyer. An attorney representing whistleblowers in a police corruption scandal says that the Department sent him a hard drive laden with trojans when he requested documents. Given that the rogue files were found in a folder specific to the court order (that is, they were added after the court order was issued), it looks as if someone in the FSPD wanted to hijack the lawyer's computer and sabotage his case. And that's not the only suspicious behavior, either -- the city reportedly deleted email accounts and messages that it knew it was supposed to keep.

Sophisticated malware has been spying on computers since 2008 (updated)
Highly sophisticated malware isn't limited to relatively high-profile sabotage code like Stuxnet -- sometimes, it's designed to fly well under the radar. Symantec has discovered Regin, a very complex trojan that has been spying on everyone from governments to individuals since at least 2008. The malware is highly modular, letting its users customize their attacks depending on whether they need to remote control a system, get screenshots or watch network traffic. More importantly, it's uncannily good at covering its tracks. Regin is encrypted in multiple stages, making it hard to know what's happening unless you capture every stage; it even has tools to fight forensics, and it can use alternative encryption in a pinch. Researchers at Symantec suspect that the trojan is a government-created surveillance tool, since it likely took "months, if not years" to create.
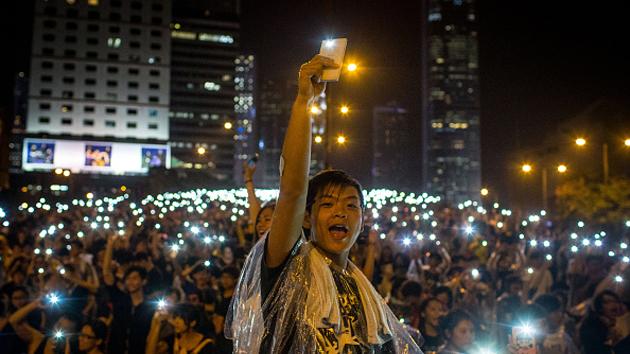
New spyware targets Hong Kong protesters' phones
Hong Kong's pro-democracy protesters have more to worry about than they thought -- someone is gunning after their phones, too. Lacoon Mobile Security says it has detected new spyware, Xsser, that tries to trick WhatsApp users on Android and iOS by posing as a coordination tool for the Occupy Central movement. Anyone who falls for the ploy grants access to virtually all of their sensitive info, including contacts, call logs and instant messaging archives. The code is unusually sophisticated, to boot; it's a rare instance of a cross-platform mobile attack, and it updates itself over time.

Spying malware leaves countries' energy grids open to attack
Cyberwarfare campaigns against Western energy grids aren't just the stuff of action movies these days -- they're very, very real. Symantec has discovered a likely state-sponsored hacking group, nicknamed Dragonfly, that has been using phishing sites and trojans to compromise energy suppliers in the US and several other countries. Unlike targeted, destruction-focused malware like Stuxnet, this appears to be a broader spying effort bent on collecting information about national infrastructure. However, it still creates a back door that leaves companies vulnerable to full-fledged attacks if they don't spot the intrusions; it wouldn't take much to create real problems.

Blizzard update on dangerous Trojan
WoW Insider reported recently on a dangerous Trojan that was, at the time, not removable by any known antivirus program. Vigilance was advised by the Customer Support agents, and logs from anyone who was affected by the Disker trojan were requested. Thanks to the hard work of the Blizzard Support MVPs, a solution has been found. Kaltonis Our pleasure! To summarize for those of you that haven't read the green posts: -The trojan is built into a fake (but working) version of the Curse Client that is downloaded from a fake version of the Curse Website. This site was popping up in searches for "curse client" on major search engines, which is how people were lured into going there. -At this point, it seems the easiest method to remove the trojan is to delete the fake Curse Client and run scans from an updated Malwarebytes. Should you still have issues, there is a more manual method that Ressie posted earlier in the thread. -Thanks to Ressie's efforts, most security programs should be able to identify this threat shortly, if not by the time I type this. -If you were compromised, follow the instructions here and we'll do our best to set everything right (as we always do). -For those of you interested in these MitM style attacks, this is the only confirmed case we've seen in several years outside of the "Configuring/HIMYM" trojan in early 2012 that hit a handful of accounts. These sort of outbreaks are annoying, but an Authenticator still protects your account 99% of the time. Stay safe! source

Blizzard says beware of dangerous Trojan
If you play World of Warcraft, you might want to check for a dangerous new Trojan that is leading to compromised accounts. Blizzard warned customers that this Trojan, apparently brought on by a fake Curse client, can steal both the account information and the authenticator password, making even players who use the authenticator vulnerable. Customer service gave instructions on what to look for so players can see whether or not their machine has been infected. Although no current virus scanners can detect and remove the Trojan, Technical Support posted that a sample of the malware has been sent to anti-malware scanners and offered instructions for removing the malware by hand.

Blizzard Customer Support warns of dangerous Trojan [Updated]
Blizzard Customer Support Agent Jurannok has taken to the forums to warn players of a dangerous Trojan -- a virus that can enter players' accounts even if they have an authenticator. Update -- A solution has been found. Jurannok Hello, We've been receiving reports regarding a dangerous Trojan that is being used to compromise player's accounts even if they are using an authenticator for protection. The Trojan acts in real time to do this by stealing both your account information and the authenticator password at the time you enter them. If your account has been compromised recently, I'd recommend looking for the Trojan. It can be identified by creating an MSInfo file and then looking in the Startup Program section of that file for either "Disker" or "Disker64". It will usually appear like this: Disker rundll32.exe c:\users\name\appdata\local\temp\w_win.dll,dw Name-PC\Name Startup Disker64 rundll32.exe c:\users\name\appdata\local\temp\w_64.dll,dw Name-PC\Name Startup source

Trojan targets Linux desktop users, steals web banking info
Malware certainly exists for Linux, but it's more frequently targeted at servers than everyday PCs. Unfortunately, regular users now have more reason to worry: a rare instance of a Linux desktop trojan, Hand of Thief, has surfaced in the wild. The code swipes banking logins and other web sign-in details, creates a backdoor and prevents access to both antivirus tools and virtual machines. It's known to work with common browsers like Chrome and Firefox as well as 15 Linux distributions, including Debian, Fedora and Ubuntu. Thankfully, Hand of Thief is partly neutered by its limited attack methods; it relies on social engineering to fool victims into installing the software themselves. Even so, the trojan is a reminder that we shouldn't be complacent about security, regardless of which platform we use. [Thanks, Dreyer]

New adware trojan targets OS X users
Adware attacks against OS X are on the rise this year, says a report by anti-virus company Doctor Web. The Russian firm recently discovered another threat, Trojan.Yontoo.1, which has quickly become the most prominent adware trojan attacking Apple desktops and laptops. The trojan worms its way onto your computer through websites that require you to install a plugin to view the content of the site. The most common vector are movie trailer websites that prompt you to install an HD Video player or similar plugin. Instead of a media plugin, unsuspecting users will download the trojan. Trojan.Yontoo.1 then prompts you to install Twit Tube, which is a front for the Yontoo plugin. This plugin is installed as an extension for Firefox, Chrome and Safari browsers. It tracks your browsing and serves up ads on all the websites that you visit. The above image from Doctor Web shows how Apple.com would look when the adware plugin injects its ad into your browser. The best way to avoid this type of infection is to install only known and trusted plugins from reputable sites. If you are not familiar with the plugin, take a few minutes to do a Google search and see what other people have to say about the extension you are prompted to install. If you can't find any details on the plugin, it is best to just avoid it.

Capcom Arcade Cabinet offers 1986 trio this week
The third pack of Capcom Arcade Cabinet releases is a trio of games from 1986: Side Arms, Legendary Wings, and Trojan.The $10 pack is an interesting mix of side-scrolling and vertical shooting, and the post-apocalyptic urban sword-and-shielding of Trojan, a game we remember for being the early Capcom NES game that wasn't Gun.Smoke, Commando or Mega Man.As usual, the arrival of this pack today means that last week's games will be available a la carte for $4 each.








