DenialOfService
Latest

Arizona man gets 20 months in prison for emergency system DDoS attacks
Denial of service attacks are serious by themselves, but doubly so when they target vital systems... and one perpetrator is finding that out first-hand. A court has sentenced Arizona resident Randall Charles Tucker (who nicknamed himself the "Bitcoin Baron") to 20 months in prison for launching distributed denial of service attacks against city websites, including damaging attacks against Madison, Wisconsin. He not only took down the city's website, but "crippled" its emergency communication system to the point where first responders had trouble reaching the 911 center. It also 'degraded' the automatic dispatching for emergency crews.

'World of Warcraft' cyberattacker sentenced to year in prison
One World of Warcraft player is paying the price for taking a virtual rivalry too far. A US federal court has sentenced Romanian man Calin Mateias to spend a year in federal prison after he pleaded guilty to launching a distributed denial of service attack against WoW's servers in response to being "angered" by one player. The 2010 traffic flood knocked thousands of players offline and cost Blizzard $30,000 (which Mateias repaid in April) in recovery expenses.
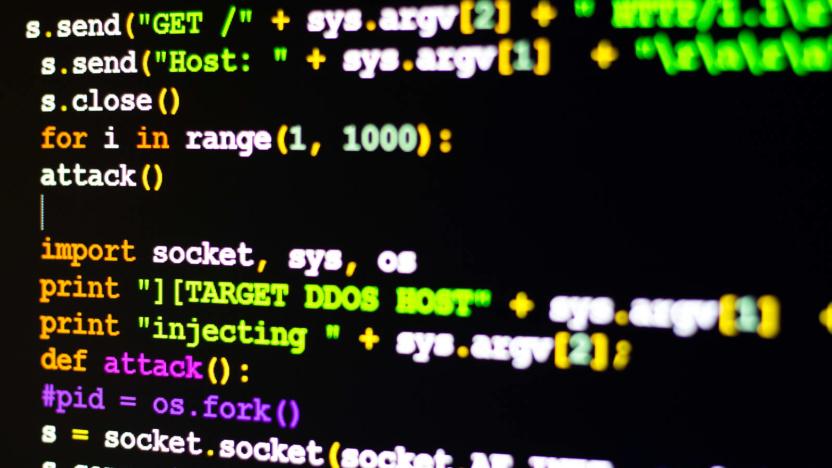
Police take down the world's largest DDoS-for-hire service
The internet might be slightly safer against distributed denial of service attacks in the near future... slightly. Police in twelve countries have taken down WebStresser, believed to be the world's largest service for paid DDoS attacks. The joint campaign (Operation Power Off) seized WebStresser's infrastructure in the US, UK and the Netherlands, and busted site administrators ranging as far as Australia and Hong Kong.

US pressured North Korea by overwhelming hackers with data traffic
The US is no stranger to hacking North Korea, but it's usually in a bid to directly thwart the country's military ambitions. Now, however, those attacks are being used as a diplomatic strategy. The Washington Post has learned that President Trump ordered a broad pressure campaign against North Korea that led to the US conducting a denial of service attack against North Korea's spying office, the Reconnaissance General Bureau. The move flooded the RGB's servers with traffic that effectively strangled their internet access, including the Bureau 121 group responsible for the North's hacking campaigns. And while it clearly didn't change Kim Jong Un's mind, it does appear to have had a practical effect.

Senators ask FBI to investigate FCC's alleged cyberattack
The FCC isn't exactly forthcoming with evidence of the alleged denial of service attack on its servers, and that's leaving some worried. Is it protecting privacy (as it claims), or stifling attempts to post comments supporting net neutrality? A slew of Senators want to find out -- and they're going above the FCC's head to make sure they get answers. Senators Al Franken, Patrick Leahy, Edward Markey, Brian Schatz and Ron Wyden have sent a letter to FBI Acting Director Andrew McCabe asking his bureau to conduct a high-priority investigation of the FCC's cyberattack claims. While they don't directly accuse the FCC of dishonesty, it's clear from the wording that they aren't just taking the Commission's word at face value.

FCC stonewalls demands for evidence of cyberattack
The FCC swears that a denial of service attack hit its servers hours after Last Week Tonight's John Oliver rallied support for net neutrality, but where's the evidence? Well, don't expect it any time soon. In an interview with ZDNet, the regulator's David Bray says the FCC won't release the logs that might show who was responsible for the incident. The logs contain private info like IP addresses, he says. Bray does note that there wasn't a botnet involved, though -- instead, the traffic came from commercial cloud services using the FCC's public programming interface. But if it wasn't a botnet, then who was involved? Some critics are concerned that the FCC isn't exactly being forthright.

Nastier version of IoT botnet could brick your smart toaster
Two new versions of a nasty botnet called BrickerBot were spotted in the wild by researcher Pascal Geenens, who reported the latest attack for security firm Radware. Permanent denial-of-service botnets like these can infect poorly-protected IoT devices like smart toasters and web-enabled vibrators to bring down various connected web servers. These new BrickerBot iterations use scripts with even more commands and almost four times as many actual attacks as previous iterations to completely overwhelm their targets.
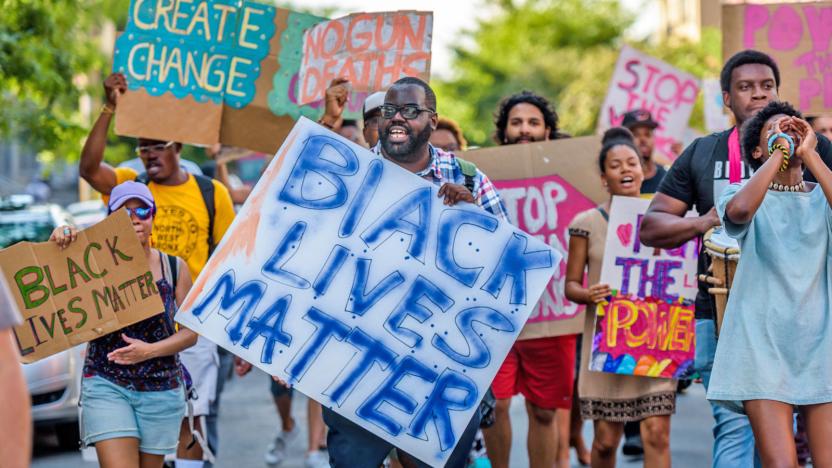
Black Lives Matter site faced over 100 attacks in half a year
When you launch protests in the modern era, you don't just have to worry about aggressive responses on the streets... you have to worry about your online presence, too. Deflect Labs has determined that Black Lives Matter's official website was subject to over 100 botnet-based denial of service attacks between April 29th and October 15th, a large part of it coming from members of a Ghost Squad hacking collective that had vocally denounced BLM's campaign. And it didn't require many people, either. Just two culprits (who may be the same person) launched nearly a fifth of the attacks, one of which tried to flood the site with traffic using nearly 1 million bots.

One laptop can take down major internet servers
You don't need a massive botnet to launch overwhelming denial of service attacks -- in some cases, a personal PC and so-so broadband are all that's required. Researchers at TDC Security Operations Center have revealed a new attack technique, BlackNurse, that can take down large servers using just one computer (in this case, a laptop) and at least 15Mbps of bandwidth. Instead of bombarding a server with traffic, you send specially formed Internet Control Message Protocol packets that overwhelm the processors on server firewalls from Cisco, Palo Alto Networks and others. The firewalls end up dropping so much data that they effectively knock servers out of commission, even if they have tons of network capacity.

Report confirms IoT botnet took down Krebs' security site
Two weeks ago, security researcher Brian Krebs' site KrebsOnSecurity got knocked offline by one of the biggest DDOS attacks ever recorded, which peaked at 620 Gbps. What happened? Akamai, which had been protecting the site for free but ultimately had to unload it as the sustained traffic would have cost them millions of dollars, released a postmortem today. In it, they confirm that the attacker mainly used the Mirai malware to ovewhelm Krebs' site, though there may have been another botnet involved. But the most crucial distinction from a normal DDOS strike: These bots were mostly IoT devices.
Security writer recovers from massive revenge cyberattack
Journalists are no stranger to making enemies bent on retaliation. However, it's becoming increasingly difficult to survive that retaliation in the internet era... just ask security writer Brian Krebs. An unknown party knocked his website offline last week with a massive distributed denial of service attack (620Gbps of non-stop data) as revenge for exposing two major cyberattack sellers who've since been arrested. He's only back online after taking advantage of Alphabet's Project Shield, which protects journalists against censorship-oriented denial of service campaigns. His previous anti-DDoS provider, Akamai, had little choice but to drop him -- the company tells the Boston Globe that a sustained attack on that level would have cost the company "millions."

Major cyberattack seller knocked offline as it faces arrests
One of the more popular cyberattack peddlers just came crashing down. Israeli law enforcement has arrested Yarden Bidani and Itay Huri as part of an FBI investigation into their alleged control of vDOS, one of the most popular paid attack platforms. According to information unearthed by security guru Brian Krebs from a third-party hack targeting vDOS, the two teens raked in at least $618,000 launching "a majority" of the distributed denial of service campaigns you've seen in recent years. The platform itself is also offline, although that's due to one of vDOS' victims (BackConnect Security) using a bogus internet address claim to stem the flood of traffic hitting its servers.

'Pokémon Go' expansion marred by a possible cyberattack
Good news! Pokémon Go is available in 26 more countries... if you get a chance to play, that is. Trainers can now grab the mobile game across a wider swath of European nations (such as the Netherlands and Sweden), but temporarily went down amid reports of a possible distributed denial of service attack. The internet collective PoodleCorp claims to have flooded Pokémon Go servers worldwide with enough traffic to effectively render them useless.

Hackers target firm protecting against denial of service attacks
When you dedicate your company to protecting against hacks, you make yourself a bigger target for those hacks... and one firm is learning this the hard way. Staminus, an online hosting service that focuses on protecting against distributed denial of service attacks, was the victim of an apparently giant hack last week. In addition to going offline until Thursday night, the company has confirmed that the intruders took customer data that includes payment card info, user names and (thankfully hashed) passwords. The perpetrators claim to have hijacked and reset the majority of Staminus' routers.

Steam's Christmas privacy issues affected 34,000 users
On Christmas day, up to 34,000 Steam members were able to view other users' private information, including billing and email addresses, following a glitch triggered by a denial-of-service attack, Valve announced today. On the day of the attack, Valve said that the glitch was the result of a caching issue, and that users were able to view strangers' information, though they couldn't take action on other people's accounts. Valve's update today clarifies the caching issue, attributing it to the DoS attack.

Anonymous takes credit for cyberattacks crippling Turkey
Apparently, the hacktivists from Anonymous aren't just targeting ISIS directly -- they're causing chaos for indirectly responsible countries, too. The collective is taking credit for an escalating series of cyberattacks that have disrupted banks, internet backbones and government websites in Turkey. The campaign is meant to punish Turkey for allegedly turning a blind eye to activities that fund ISIS' extremism, such as oil smuggling. According to Radware, the attacks have been so fierce that they took down access to 400,000 sites and left Turkey blocking traffic in an attempt to keep sites online.

Attacker who ruined your holiday gaming gets a slap on the wrist
If you were hoping that all of the Lizard Squad attackers who took down the PlayStation Network and Xbox Live last holiday would get their comeuppance... well, you'll be disappointed. A Finnish court has convicted Julius Kivimäki (aka "Ryan" and "Zeekill") of a whopping 50,700 charges related to various computer crimes, including data breaches, telecommunication-based harassment and swiping credit card data. It sounds good, but his penalty is limited to a suspended 2-year prison sentence and an order to help fight cybercrime -- a trivial penalty in light of his overall damage. Even if you limit Kivimäki's culpability to the gaming network outage, he was still partly responsible for days of downtime at Microsoft and Sony that frustrated millions of players. While he'll theoretically stay on the straight and narrow for at least a while, the verdict isn't exactly going to scare Lizard Squad's other members into becoming model citizens. [Image credit: Jean-Jacques Boujot, Flickr]

Cyberattack takes down Canadian government websites
It's not just the American government that's facing withering internet attacks in recent days. Canadian officials have confirmed that a "cyberattack," likely a denial of service campaign, has taken down government websites on the gc.ca web domain -- which, if you know the country, means that virtually every federal institution is inaccessible online. Many government email accounts are largely out of commission as well. It's not clear whether the assault has compromised any sensitive data, but traffic floods like this are typically focused more on knocking sites out of commission than swiping info.

PlayStation Network is back online following Christmas Day attack
Three days after Lizard Squad's latest denial of service attack knocked the PlayStation Network offline (and Xbox Live, we'd add), the internet gaming service is gradually getting back on its feet. Sony now says that PSN should be up and running for all of its consoles. While the company warns that there might be some "intermittency" as it gets back into the swing of things, you theoretically won't face major interruptions during that big Destiny raid. It's not clear if Sony's infrastructure will be any better at weathering future digital assaults on this scale; given that the attack was supposedly three times larger than the previous record-setter, this probably isn't a permanent fix. However, it's good to know that you can squeak in at least some online gaming on that shiny new PS4 before the holidays are over.

These are the hackers who wrecked your holiday gaming
If you're a console gamer, you're probably all too aware of Lizard Squad, the hacker outlet that allegedly knocked both the PlayStation Network and Xbox Live offline for a good chunk of the Christmas break. But just why and how is this group causing so much grief? Thanks to the Daily Dot, we now have a better (if imperfect) idea of what's going on. It might not shock you to hear that the team is doing this both for laughs, à la LulzSec, and to expose the "incompetence" of the security teams at Microsoft and Sony. However, they also claim to have access to undersea internet cables and other "core routing equipment" that lets them flood networks with massive amounts of data. They supposedly bombarded PSN and XBL at a rate of 1.2 terabits per second, or three times the rate of the previous largest attack on record.



