honeypot
Latest

Anonymous deals with its QAnon branding problem
When you're a notorious hacking entity like Anonymous, and a pro-Trump conspiracy cult (QAnon) steals your branding (while claiming you're the impostor), the obvious thing to do is declare cyberwar. That's exactly what Anonymous did this past week in a press announcement, followed by a social media and press offensive. So far Anonymous has managed to take over QAnon's hashtags (while adding #OpQAnon and others) and dox a couple hundred members of Trump's pedophilia-obsessed, "deep state" doomsday cult. QAnon's mouthpieces responded exactly as we'd expect, with taunts and tweets saying: "These people are STUPID!! They have no brains and no skills. Typical 'empty threat' terrorists! But DO NOT click their links!! Virus city baby!!"
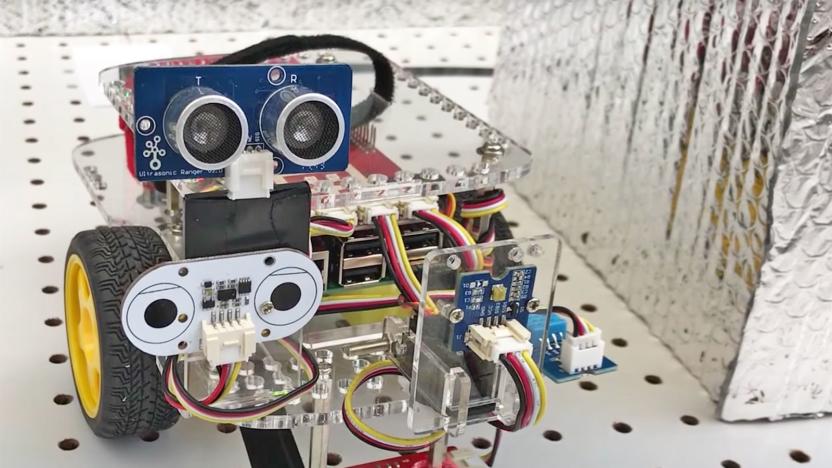
HoneyBot lures hackers to protect its fellow robots
As more and more industrial robots come online, there's an ever greater risk of hackers gaining access to them and taking control of their abilities. In some cases that could mean damage to a product or manufacturing flow, but in other cases, it could result in harm to nearby humans. That's why researchers at the Georgia Institute of Technology are developing a robot that can alert users to an ongoing breach and trick hackers into thinking they have control of their target.

UK spies tracked Middle East activists with a web link shortener
Intelligence agencies don't always rely on hacks to monitor and influence political events. Motherboard has learned that the UK's GCHQ created its own URL shortener, lurl.me, to both disseminate pro-revolution talk during Iranian and Arab Spring protests as well as track activists. Puppet accounts would use lurl.me to help get around government censorship, while GCHQ would send special links to help identify activists who were otherwise hard to follow. The combination also made it easy to understand the effectiveness of revolutionary campaigns online -- if many people clicked a link and behavior changed, GCHQ would know that its efforts made a difference.

FTC offers a $25,000 prize if you can trap robocallers
Yep, the Federal Trade Commission still hates robocalls as much as you do. The agency has launched a contest where you'll get a $25,000 top prize if you develop technology that sends illegal automated telemarketing to a honeypot system, which makes it easier to study calls and catch perpetrators. You have up until the evening of June 15th to qualify your bot trap, and the winner will be decided at a Def Con showdown on August 9th. The payout certainly isn't large, but think of this as doing the country a favor -- you may save millions from listening to Rachel from card services over and over again. [Image credit: SarahNW, Flickr]

Sit back and watch hacks around the world in real time
Want to feel anxious about your internet connection? The security firm Norse is more than happy to oblige. It's running a live hacking map that shows the attacks against a worldwide honeypot (that is, purposefully vulnerable) network as they happen. While this isn't representative of the full internet, it does act like a microcosm to some degree -- the bulk of attacks originate from China or the US, while Americans almost always serve as the punching bag. You'll even see large-scale (and surprisingly pretty-looking) assaults if you tune in at the right time. Now if you'll excuse us, we're going to double-check on our firewalls... this map isn't exactly reassuring.

Mac OS X Lion beta reveals "Restart to Safari" browser-only mode (update: honeypot)
MacRumors was digging through the latest developer beta of Mac OS X Lion when it found a rather intriguing new option -- if you choose "Restart to Safari" on the user lock screen, the computer will reboot into a mode which consists entirely of the web browser. If that sounds familiar, perhaps you've heard of Google's Chrome OS, a partially-fledged operating system that runs within the browser itself... but we haven't heard Apple express a desire for any such thing. Now, certainly we've seen a number of Windows desktops and laptops ship with a secondary, browser-centric OS like Splashtop in order to have an instant-on mode, but if you have to boot and reboot the computer to get to Safari, that doesn't sound like much of an improvement. Perhaps it's a way to let guests (or children) entertain themselves without giving them access to your files? All we know for certain is that it's a most mysterious option. Update: But perhaps not as mysterious as we thought -- 9to5 Mac spotted its genesis earlier this week, and it's a bona fide honeypot. If your Mac gets stolen, the idea goes, it'll need to be connected to the internet for you to be able to track it with Find My Mac or perform a remote wipe, so you'll let the thieves browse this guest account to keep them busy without letting them peruse your personal files. Cue the Admiral Ackbar, we suppose. [Thanks, Jamie]

Univ. of Wisc. Madison Mac OS X Security Challenge Update
If you remember, Mac sysadmin at University of Wisconsin Madison, Dave Schroeder, set up a Mac mini as a type of honeypot to challenge the "hacking" community to see if anyone could compromise a Mac OS X 10.4.5 system. The Mac mini in question was set up as an "out-of-the-box" system with Apple's Security updates applied, and he turned on both SSH and Apache, two common Internet services, but not ones that the average Mac OS X user would ever enable.Initially, the contest was set to end on Friday, March 10th, after which he would publish the details of his experiment. However, checking the site this evening, I see that he's scheduled it to end tonight at midnight (Central Time). Dave Schroeder also says that "the machine is under intermittent DoS attack. Most of the other traffic, aside from casual web visitors, is web exploit scripts, ssh dictionary attacks, and scanning tools such as Nessus."Has the box been compromised? He doesn't say, but he will be publishing the results of the experiment (probably tomorrow). I'm very interested and intrigued to read what the end result will be, even if it the news isn't good (i.e. the machine was actually compromised). Whatever the results, it's sure to be a better analysis of Mac OS X security than the misleading and poorly-designed example making the news rounds yesterday.


