mds
Latest

Intel is patching its Zombieload CPU security flaw for the third time
For the third time in less than a year, Intel has disclosed a new set of vulnerabilities related to the speculative functionality of its processors. On Monday, the company said it will issue a software update "in the coming weeks" that will fix two more microarchitectural data sampling (MDS) or Zombieload flaws. This latest update comes after the company released two separate patches in May and November of last year.

Intel fixes CPU security flaw it said was patched in May (updated)
It turns out that Intel's CPU security fixes from May didn't address everything the company mentioned. Intel is rolling out another patch that does more to close the speculative execution flaws that could let attackers swipe passwords and other sensitive info. The mitigations in the patch should "substantively reduce" the possibility of an attack, Intel said. This still doesn't fully resolve the problem, but Intel is promising future CPU-level microcode fixes. There's a larger concern over how Intel has handled these vulnerabilities in the first place, however.
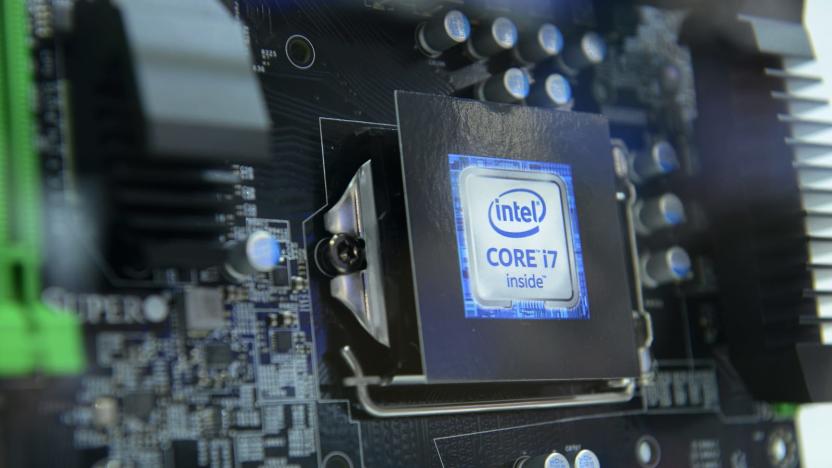
Install updates now to address a vulnerability in most Intel CPUs
In January 2018, a pair of security exploits dubbed Spectre and Meltdown showed how attackers could take advantage of commonly-implemented CPU technology to access data they shouldn't have been able to. They were followed by a similar bug, Foreshadow, late last year, and now researchers have uncovered four different techniques that exploit Intel's speculative execution technology in a similar way. The website CPU.fail has collected information about each vulnerability -- they're collectively referred to as Microarchitectural Data Sampling (MDS) -- including Zombieload, RIDL & Fallout, and Store-to-Leak Forwarding. Example code shows how the attacks could be launched using malicious JavaScript, for example, and researchers state that it would be difficult for antivirus software to detect it, however they have not found evidence of anyone using the tech in attacks so far.

MIT's Nexi bot wants to be your friend
MIT is really taking its robotics program to a whole new level with its "MDS" platform, which stands for Mobile, Dexterous and Social. The flagship bot so far is Nexi, who certainly fits the bill, albeit with an extra dab of creepy. The bot stands on a Segway-esque wheel base, has articulated arms and hands, and can convey a wide range of emotion with that pasty white face. Nexi has a computer on board to manage sensors and instinctual responses, while it offloads the heavy duty AI work to a stationary computer over the network. MIT's eventual goal is to have Nexi and others participate in Socially Situated Robot Learning -- observing and interacting with humans to figure out how best to integrate with them. Don't worry Nexi, we like you for you. Video is after the break.[Via fresh creation]



