social engineering
Latest
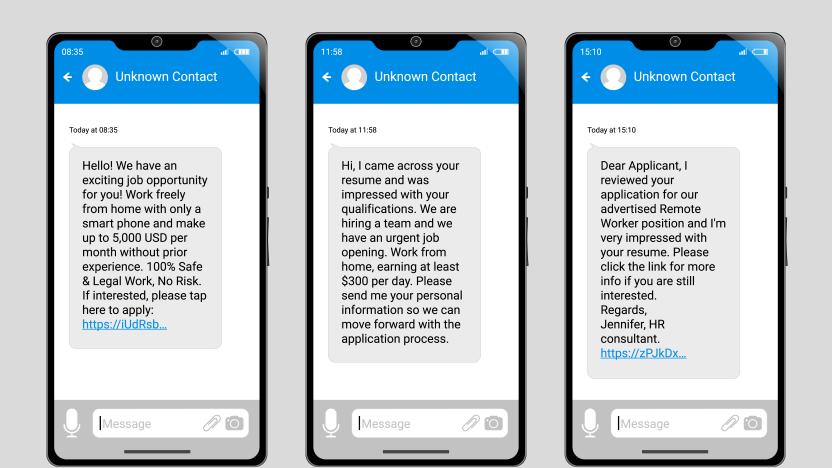
How social engineering takes advantage of your kindness
Social engineering psychologically manipulates a target into doing what the attacker wants, or giving up information that they shouldn’t.

Marriott suffers at least its seventh data breach since 2010
Attackers used social engineering to gain access to an employee's computer and steal around 20GB of files.
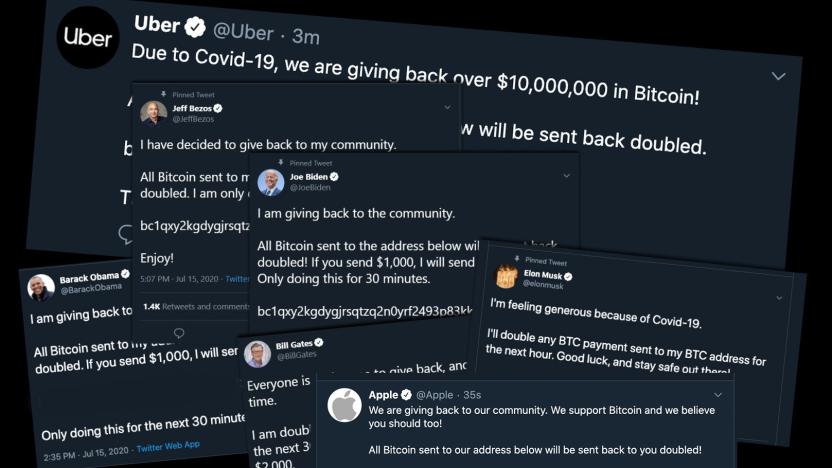
Twitter's Bitcoin hackers had almost limitless access
Imagine getting the keys to the Twitter kingdom -- access to all the account admin panels in the world. What would you do? If you're any kind of seasoned attacker, you wouldn't blow your own cover by tweeting from the world's biggest accounts -- for a bitcoin scam.

'Roblox' worker sold user data access to a hacker
A hacker bribed a 'Roblox' worker to get access to sensitive user data, including account logins.

Verizon vulnerability made it painfully easy to access customer info
On the off chance you've experienced some sketchiness with your Verizon home internet account over the past few weeks, we might just know why now. As first reported by BuzzFeed, a vulnerability in Verizon's customer service systems meant that attackers could have duped their way into the accounts of any of the 9 million households that pay the telecom for internet access. And the worst part? The process was absolutely dead simple. Verizon, for what it's worth, said the issue (now fixed) came about because of a code error in a recent software update, and that they have "no reason to believe that any customers were impacted by this." Now, here's how it worked.

Feel like a real social engineer in Hack RUN
RUN is a big, evil corporation, and they're up to no good -- or at least that's what your new "employer" has told you -- and it's up to you to dig into its digital backyard for information. And with that very basic plot, the text puzzler Hack RUN sends you into command-prompt hell in search of some answers. It's a bit hard to explain exactly how you play Hack RUN; you quite literally fiddle around with a command-prompt interface and a few other digital tools in an attempt to find the truth behind a company's shady business practices. Clues are everywhere, and you'll use social engineering and outright snooping to find your way into various virtual realms where you should not be. Things start slowly, with access to a single employee's email account being your first test. After trying a few commonly used passwords, you'll crack the simple code and begin your journey. Soon you'll be browsing various "websites" for password clues, picking up info on a whole slew of RUN's workers, and piecing together a picture of what the company is really up to. All along the way, your employer updates you on your progress, offers vague clues as to his true motives and ramps up the mystery. If you ever get stuck, you can always ask for a hint, and depending on how good you are at trial and error, you may find yourself begging for help before too long. The game is remarkably well done and the fake world that you're poking around in really does begin to feel real. This makes every successful password guess and subroutine achievement all the more gratifying. Hack RUN is available on both iOS and OS X, and at the moment it's free. I'd honestly recommend the desktop version available through the Mac App Store as the best version, simply because tapping away at your keyboard while performing fake hacks seems much more appropriate than doing it on the iPhone or iPad screen. If you're looking for a unique puzzle game, it's an easy recommendation.

'High profile' Microsoft employees' XBL accounts hacked through social engineering
Certain unnamed Microsoft employees have been targeted by Xbox Live hackers, The Verge reports. The exact methodology is unclear (for good reason!) but it involves obtaining the targets' Social Security numbers – which are not used by Xbox Live – and using that information to get information out of another company, which is then used to gain access to the XBL account."We are actively working with law enforcement and other affected companies to disable this current method of attack and prevent its further use," a Microsoft rep told The Verge. "Security is of critical importance to us and we are working every day to bring new forms of protection to our members." Especially the members who work there.Xbox Live hacking of employees is not a new phenomenon. Former XBL director of policy and enforcement Stephen Toulouse found his account hacked in 2011, followed by a number of insulting calls and voicemails from the hacker. [Image: David Evison via Shutterstock]

Amazon, Apple stop taking key account changes over the phone after identity breach
By now, you may have heard the story of the identity 'hack' perpetrated against Wired journalist Mat Honan. Using easily obtained data, an anonymous duo bluffed its way into changing his Amazon account, then his Apple iCloud account, then his Google account and ultimately the real target, Twitter. Both Amazon and Apple were docked for how easy it was to modify an account over the phone -- and, in close succession, have both put at least a momentary lockdown on the changes that led to Honan losing much of his digital presence and some irreplaceable photos. His own publication has reportedly confirmed a policy change at Amazon that prevents over-the-phone account changes. Apple hasn't been as direct about what's going on, but Wired believes there's been a 24-hour hold on phone-based Apple ID password resets while the company marshals its resources and decides how much extra strictness is required. Neither company has said much about the issue. Amazon has been silent, while Apple claims that some of its existing procedures weren't followed properly, regardless of any rules it might need to mend. However the companies address the problem, this is one of those moments where the lesson learned is more important than the outcome. Folks: if your accounts and your personal data matter to you, use truly secure passwords and back up your content. While Honan hints that he may have put at least some of the pieces back together, not everyone gets that second chance.

The Soapbox: Eat your tanking or you won't get your ice cream
Disclaimer: The Soapbox column is entirely the opinion of this week's writer and does not necessarily reflect the views of Massively as a whole. If you're afraid of opinions other than your own, you might want to skip this column. Picture this -- you're a parent of a squalling child. (For some of you, this may be a very easy picture as you sit at the dinner table.) Your child is refusing to eat his or her dinner on the basis that the broccoli doesn't taste like doughnuts covered in Skittles. Being a mature adult and realizing that a lifetime of Skittle-based food toppings is not a viable dietary choice, you are trying to patiently reason with said child despite the fact that the child assumes Kevin at school is evil incarnate because he took the good swing despite your child's having called it. Eventually, you break down. You tell your child that a special treat awaits if he or she eats all of those vegetables. And so your child queues up for a random heroic in World of Warcraft, and -- wait, we skipped ahead of the metaphor, but that's essentially what the whole Call to Arms feature boils down to. And it brings up interesting questions of bribery, choice, and what makes a fun and functional mechanic.

EVE Evolved: Death of an Industrialist, part 2
Of all the things that define EVE Online, it's the stories of criminality that stand out the most. The criminal underworld of New Eden is so deeply ingrained in EVE that CCP even made a selling point of it in the latest official trailer. Last week, I began to tell the true tale of one EVE pilot's thirst for revenge and the corporate infiltration techniques he used to get close to his target. In this week's conclusion of the story, Scott's plans for revenge come to fruition. But is Scott really the victim he believes himself to be, or has greed blinded him to what he's doing? If you haven't read part 1 of the story, skip back to read last week's EVE Evolved column before reading on. Newbies again Once in Zeeqo's corp, Scott and his crew began the slow task of setting their target up for a colossal fall. Simply destroying Zeeqo's mining barge could be a swift and fitting retribution, but Scott had a much harsher punishment in mind. Zeeqo would be made to pay for his mistake several times over. The plan for retribution hinged on Zeeqo's weekend freighter runs to Jita, a time at which he flew his most expensive and indefensible ship. This gave the three infiltrators only five days to befriend their target and work out how best to capitalise on his weekly haul.

EVE Evolved: Death of an industrialist
It's often said that the EVE Online universe is a dark and harsh place, the market overflowing with con-artists and the skies filled with pirates looking for some easy prey. The sandbox style of New Eden enables emergent gameplay like market manipulation, corporate infiltration, spying and theft. When faced with the choice, some players choose to be ruthless outlaws who will stop at nothing to further their own goals. Political puppet-masters pull the strings on the alliance war machines from behind the scenes, spies infiltrate corporations to gather intelligence, and thieves plot their way to riches. The latest official game trailer makes a big point of this side of EVE, telling an incredible story of revenge and theft that closely mirrors the reality of New Eden. As if to highlight the point made by the trailer, this week EVE player Bad Bobby confirmed that he'd stolen a total of 850 billion ISK from players in the investment market. Concluding a plan set in motion years ago, Bobby pulled off the theft last week of his supposedly secured Titans4U company. In keeping with this recent theme of theft and corruption, this week's EVE Evolved is a story of revenge, corporate infiltration, social deception and utter destruction. I've embellished the story in places and names have been changed to protect the privacy of all those involved, but the events described are real. In this week's article, I begin to tell the very real tale of an EVE player's revenge -- a precision strike against an industrialist who made one fatal mistake.

Beware of WoW Armory phishing scams [Updated]
First things first: the correct address for the WoW Armory is wowarmory.com. Bookmark it. Memorize it. But don't ever, ever search for it again. We've talked before about how misspelling searches can get you into trouble. But even if you spell WoW Armory correctly when Googling, the first sponsored site that shows up is a phishing site -- and it's a really good one. Update 1:10pm: Google seems to have removed the site from their sponsored listing in the short time since I wrote this post. Kudos! Nonetheless, there are and will be more sites using the same technique, so the warning remains valid. Do not go to the following site: armory-worldofwarcnaft.com/wowarmory/, it is evil. Notice the n in warcnaft? You may not when you are clicking on it in your search page or when it shows up in your address bar. And that's what they are counting on. Because the rest of the site looks authentic. When you type in what you want to search for, you get asked for your Battle.net info. Then, no matter what you type in, it gives you a password error. (I typed in profanity. It was fun.) They have stolen all of the elements of the actual Blizzard pages, so that if you want your login page in other languages, just a click of the button will get you there. But don't. It's evil.

In defense of care packages and mandatory authenticators
If you read WoW.com with any regularity, you probably saw and read our pieces on Friday discussing some rather curious policies Blizzard has recently instituted. There are two in particular that I'd like to discuss further: The care package for hacked accounts and the possibility of mandatory authenticators. First, how many of you have had your accounts stolen, or know someone that had theirs stolen? Chances are good every single person that reads this post will raise their hand to that question. The problem is not a small one. I'm in a rather large guild, and every few weeks someone has their account stolen and the little bits of our guild bank they have access to go with them. My large guild is also just one guild in a larger guild alliance which suffers the same problems. Every two weeks or so, someone I see online on a regular basis gets their account stolen.

How flaws in Blizzard's billing department are being exploited
Please see the update to this original post. In our continuing series on account security issues present within Blizzard's offices, we bring you news that lax training in Blizzard's billing department is being exploited by those attempting to game the system and illegitimately acquire more gold and high value in-game items. The critical flaw in Blizzard's system is that billing support personnel are currently given the ability to "roll back" characters to previous versions more or less on the spot, with the customer on the phone. Because of this, there is a high degree of flexibility and personal accountability on the part of the billing representative. The flexibility extended here is vitally important to customer service, however the training that comes with the flexibility, we are told by multiple sources, is inadequate and leads to this exploit being practiced by a growing number of individuals. The exploit involves human interaction (aka social engineering), which in security systems is the notoriously weak point. The exploit is often referred to internally as "onioning," which involves the player repeatedly claiming the account was compromised to the Blizzard billing support representatives. There are obviously more details to doing this, but we don't want to provide a how-to. Blizzard is aware of how this is done, and they are currently not implementing checks to combat this.

Popular scams and how to avoid them
We have a lot of reports of scams coming in to our tip line and many of us are receiving the same phishing emails you are. Even Scott Kurtz from PvPOnline was tweeting about getting one the other day. These scams can be initiated via email to any one of your email addresses. Or they may start in game. Regardless of where they attack you, most of the scams require some form of social engineering to get your info and therefore access to your in-game valuables.What is social engineering? Social engineering is manipulating victims to volunteer personal information about themselves in order to perpetrate a con, scam, fraud, etc. If you have seen the movie Groundhog Day, then you have seen a very good example of it. Phil, a television weatherman, is living the same day over and over. One iteration of his morning, he asks an attractive woman her name, where she went to highschool and her English teacher. The next iteration of his morning, he "accidentally" runs into her and pretends to know her from highschool, resulting in her going to bed with him.

Lame scams still profitable in Guild Wars, over 1000 bans every week
Would you fall for this? (Please say 'no'...): A complete stranger approaches you on the sidewalk outside of your bank and shows you a rare coin he says is worth twenty thousand dollars. "I want to just give this coin to you," he says, "but I don't want anyone to know we did this... tax issues, you see." The stranger suggests putting it in your safe deposit box, but because he's so concerned about privacy, he wants access to your safe deposit box to be sure the rare coin gets there, with no one the wiser. The problem is that he can only get in there with your express permission...We're guessing 99.99% of you would never get suckered by something asinine like this, but why then do people fall for the exact same thing in the virtual realm? Specifically, it seems that Guild Wars players regularly turn over their login info to account thieves in hopes of getting something for nothing, as mentioned by Ravious over at Kill Ten Rats. This ultimately leads to a continuous deluge of stolen accounts, tears, and rage.

WoW Insider Interview: Blizzard speaks about Authenticator security
About a month and a half ago, we reported on the story of a player who had apparently gotten their account hacked while they were using the new Blizzard Authenticator key, and it raised a lot of questions in players' minds about the only hardware Blizzard's ever made: just what does the Authenticator do to protect players' accounts? Have Authenticators actually prevented accounts from being hacked? And what would it take to, through social engineering or other methods, actually remove an Authenticator from an account?At the time we published that first story (which was later disputed by a customer support representative), Blizzard contacted us here at WoW Insider, offering to clear up players' concerns about the new keys. We quickly submitted to them a few questions pulled from our own writers and a few submitted by readers, and they've now returned the answers to us -- you can find Blizzard's answers to our questions about the Authenticator after the break. Thanks to Blizzard for answering our questions about how these keys work, and clarifying some of the issues around their security.








