exploit
Latest

Multiple antivirus apps are vulnerable to common security flaws
At least 28 well-known antivirus apps could be exploited by shared security flaws, and a few are still vulnerable now.

Apple Mail for iPhone may be vulnerable to malware attacks (updated)
Security researchers say they've found a flaw in iOS' Mail app that lets attackers deliver malware without user input, although evidence is scarce.

Safari flaw let intruders hijack cameras on iPhones and Macs
If you're working on a Mac at home or reconnecting with friends on an iPhone, you'll want to be sure you have the latest security updates. Security researcher Ryan Pickren has detailed recently patched Safari vulnerabilities that allowed intruders to hijack the cameras and microphones on iOS and macOS devices. A maliciously crafted website could trick Safari into believing the page had the same camera and mic permissions as one you'd already cleared, such as Skype. The attacker just needed a combination of specially-made web addresses with scripts to perform a "bait-and-switch."

Chinese digital spying is becoming more aggressive, researchers say
FireEye, a US cybersecurity firm, says that it has seen a concerning spike in activity from what appears to be a Chinese hacking group called APT41. The attacks are being deployed against companies in the US, Canada, the UK and several other counties, which is atypical of Chinese hackers' typical strategy of focusing on a few particular targets. According to FireEye's report, the group is exploiting software flaws in applications and hardware developed by Cisco, Citrix and others to gain access to target companies' networks and download files via FTP, among other strategies. According to the firm, the attacks began on January 20th, dipped during the Chinese New Year celebrations and COVID-19 quarantine measures and are now back at full scale, affecting 75 of FireEye's customers.

AMD CPUs for the past 9 years are vulnerable to data leak attacks
It's not just Intel chips that are vulnerable to hard-to-fix security flaws. Researchers at the Graz University of Technology have detailed a pair of side channel attacks under the "Take A Way" name that can leak data from AMD processors dating back to 2011, whether it's an old Athlon 64 X2, a Ryzen 7 or a Threadripper. Both exploit the "way predictor" for the Level 1 cache (meant to boost the efficiency of cache access) to leak memory content. The Collide+Probe attack lets an intruder monitor memory access without having to know physical addresses or shared memory, while Load+Reload is a more secretive method that uses shared memory without invalidating the cache line.

It took Google months to patch a serious Android security flaw
Google has patched a critical security flaw that affects millions of Android devices with chipsets from MediaTek, XDA Developers revealed today. The vulnerability is a rootkit lodged in the CPU's firmware. It allows a simple script to root Android devices that use nearly any of MediaTek's 64-bit chips, so it has compromised hundreds of budget and mid-range smartphone, tablet and set-top box models, XDA says.
Android security flaw lets attackers send malware over Bluetooth
If you're using a not-quite current Android phone, you'll probably want to check for an update. Security researchers at ERNW have detailed a vulnerability, BlueFrag, that lets attackers silently deliver malware to and steal data from nearby phones running Android 8 Oreo or Android 9 Pie. The intruder only needs to know the Bluetooth MAC address of the target, and that's sometimes easy to guess just by looking at the WiFi MAC address. You won't even know the attack is happening, ERNW said.

Intel is patching its Zombieload CPU security flaw for the third time
For the third time in less than a year, Intel has disclosed a new set of vulnerabilities related to the speculative functionality of its processors. On Monday, the company said it will issue a software update "in the coming weeks" that will fix two more microarchitectural data sampling (MDS) or Zombieload flaws. This latest update comes after the company released two separate patches in May and November of last year.

Microsoft will fix an Internet Explorer security flaw under active attack
Mozilla isn't the only one grappling with a serious web browser security flaw. Microsoft has confirmed to TechCrunch that it will fix an Internet Explorer security exploit already being used for "limited targeted attacks." The vulnerability lets attackers corrupt memory used for the scripting engine in IE9, IE10 and IE11 in a way that would let the intruder run arbitrary code with the same permissions as the user, letting them hijack a PC. It's believed to be similar to the Firefox issue disclosed a week earlier.

Homeland Security wants you to update your Firefox browser right now
The Department of Homeland Security is urging Firefox users to update their browsers. The rare warning was issued earlier this week, after Mozilla released two critical security updates. According to the Cybersecurity and Infrastructure Security Agency (CISA), the exploit could allow hackers to "take control of an affected system."

Intel fixes CPU security flaw it said was patched in May (updated)
It turns out that Intel's CPU security fixes from May didn't address everything the company mentioned. Intel is rolling out another patch that does more to close the speculative execution flaws that could let attackers swipe passwords and other sensitive info. The mitigations in the patch should "substantively reduce" the possibility of an attack, Intel said. This still doesn't fully resolve the problem, but Intel is promising future CPU-level microcode fixes. There's a larger concern over how Intel has handled these vulnerabilities in the first place, however.

Amazon Echo Show falls victim to an old flaw at hacking contest
The latest iteration of the Pwn2Own hacking contest just underscored an all-too-common flaw with smart home devices. The security research team Fluoroacetate hacked into an Amazon Echo Show 5 by taking advantage of its "patch gap" -- that is, its use of older software that had been patched on other platforms. Brian Gorenc, the director of contest host Zero Day Initiative, explained to TechCrunch that the smart screen uses a not-so-current version of Google's Chromium browser engine that leaves it vulnerable to attacks. Fluoroacetate exploited this out-of-date code by using an integer overflow JavaScript bug to hijack the device while it was connected to a malicious WiFi network.

The first in-the-wild BlueKeep cyberattack isn't as dangerous as feared
When word broke of the BlueKeep vulnerability in Windows, many feared a repeat of NotPetya and other widespread worms that have wreaked havoc. They might not have to worry quite so much, though. Kryptos Logic has discovered the first known in-the-wild BlueKeep exploit, and it isn't as vicious as feared. The initial attack from a "low-level actor" appears to have scanned the internet and infected vulnerable systems with a cryptocurrency miner, but little else. There are no data wipes, no automatic spreading or other signs of a worm in action.

Second SIM card attack can send texts and phone location data
Simjacker isn't the only SIM-based attack that could put phones at risk. Ginno Security Lab has detailed another exploit, WIBattack, that compromises the WIB (Wireless Internet Browser) app on some SIM cards to take control of key phone functions. Like its counterpart, WIBattack infects a phone through a carefully formatted SMS text that runs instructions on cards that don't have key security features enabled. If successful, the intruders can send texts, start calls, point your web browser to specific sties, display text and send location info.

iPhone exploit could allow permanent jailbreak for millions of devices
Jailbreaks seemed to be a thing of the past, but last month, a security research released the first free, public iPhone jailbreak in years. Now, another security researcher has discovered an exploit that could make it possible to permanently jailbreak any iPhone from the 2011 4S to the 2017 iPhone X and 8/Plus.
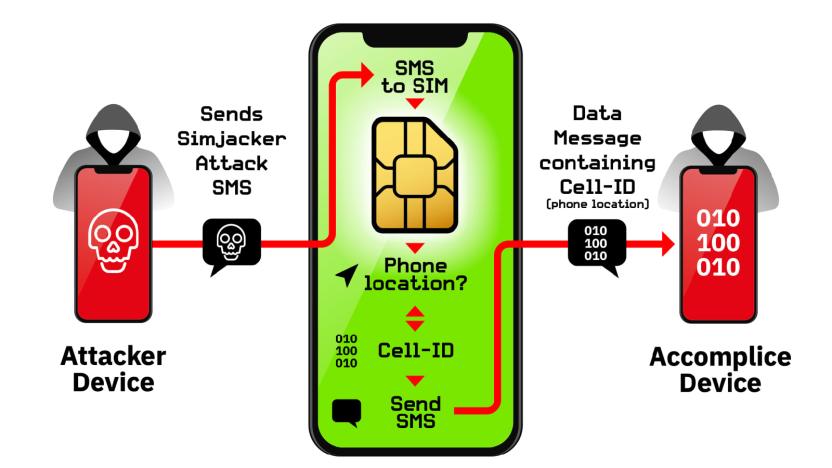
SIM-based attack has been used to spy on people for two years
In a few cases,your SIM card may pose more of a security risk than your phone's software. AdaptiveMobile Security researchers say they've discovered a new vulnerability, nicknamed Simjacker, that's being used to surveil people's devices by an unnamed surveillance company. The technique sends SMS messages containing instructions for an old S@T Browser app supported on some carriers' SIM cards. Where S@T was originally intended to launch browsers, play sounds or otherwise trigger common actions on phones, Simjacker uses it to obtain location info and IMEI numbers that are later sent to an "accomplice device" (again using SMS) that records the data.

Apple tries to clear up Google's claims about iOS vulnerabilities
Apple has taken issue with Google's findings about exploit-laden websites injecting malicious code into iPhones. Last week, Google published a blog post describing how a handful of hacked websites had taken advantage of an iOS vulnerability. Today, Apple shared a rebuttal.

Vulnerability lets text messages steal emails from Android phones
Bogus text messages aren't just being used to send you to malicious websites or crash your phone -- in some cases, they can hijack your emails. Check Point Research has discovered a vulnerability in phones from Huawei, LG, Samsung and Sony that lets attackers use custom SMS to intercept all email traffic on target devices. The attack uses the common Open Mobile Alliance version of over-the-air provisioning, a carrier technique for deploying settings to new phones, to access emails. The attacks require different methods depending on the phone and available info (such as IMSI numbers and requesting PIN codes), but the result is the same: intruders trick users into compromising their phones through messages that pose as network settings changes.

Twitter temporarily disables tweeting via SMS after account hijacks
Twitter isn't taking any chances in the wake of hackers compromising the accounts of celebrities and its own CEO. The social site is "temporarily" disabling the option to tweet via SMS until there's greater security in place. Carriers need to address "vulnerabilities" in their systems, the company said, while Twitter itself planned to tackle its reliance on linked phone numbers for two-factor authentication. It'll reinstate SMS tweeting in regions that need it for "reliable communication," but it's working on a long-term solution.

Sites stealing iPhone data reportedly targeted Uyghur Muslims
The websites stealing data from iPhones might have been used for particularly sinister purposes. TechCrunch sources claim the sites were part of a state-sponsored campaign, presumably from China, targeting the country's Uyghur Muslim population. The pages would have let China swipe sensitive info like messages and passwords, not to mention track their locations. Apple quietly fixed the issue with iOS 12.1.4 in February, but it's possible that thousands of Uyghurs' phones were compromised before then.



