GCHQ
Latest

US and UK spy agencies are exploiting flaws in security software
Those worries that governments are trying to undermine security software? They're well-founded. The Intercept has learned that both the US' National Security Agency and the UK's Government Communications Headquarters have been reverse engineering security software, such as antivirus tools and encryption programs, to look for flaws that can be used in surveillance hacks. Some of the targets in recent years include Kaspersky Lab's security suite (sound familiar?), Acer's eDataSecurity and Exlade's CrypticDisk. GCHQ also deconstructed numerous other commonly available programs, including vBulletin's forum software and popular server management tools.

UK government should retain mass surveillance powers, says report
An "undemocratic" and "unnecessary" patchwork of laws that facilitate the UK government's use of mass surveillance should be abandoned in favour of new legislation "drafted from scratch." That's the conclusion of a new, independent review commissioned by the government, which broadly supports the current powers available to intelligence services.

Spying case against UK government heads to Europe's highest court
While it's public knowledge that the UK government has secretly monitored the communications of the British public, questions over the legality of these practices still remain. After an independent UK court first ruled that security agencies, including GCHQ, had partly infringed on human rights laws, only to be overruled by a Intelligence and Security Committee (ISC) report a month later, privacy groups campaigning for clarity are taking their fight to Europe.

Laptop destroyed over Snowden leaks is now an art exhibit
Remember how, after the initial Snowden revelations, the Guardian newspaper was forced to destroy all of its computers that held the whistleblower's leaked documents? It was a strange moment; a small group of editors, under the watchful eye of two GCHQ officials, laying waste to hard drives and other internal components with industrial angle grinders and drills. Now, some of the remains -- a busted MacBook Air and a Western Digital hard drive, to be precise -- are on display at the Victoria and Albert (V&A) Museum in London. It forms part of a new exhibition called "All of This Belongs to You," which runs from now until July 19th. The hardware itself isn't particularly old or unusual, but its role in cybersecurity journalism and the Snowden leaks should make it a provocative exhibit nonetheless.

UK report concludes Huawei's no threat to national security
For years, the UK government has been concerned that Huawei's networking equipment is aiding the Chinese government and threatening national security. In Britain, the company supplies major network providers such as BT, O2 and EE, which only amplifies the anxiety of politicians and security advocates. In 2012, Huawei opened a "Cyber Security Evaluation Centre" to alleviate some of their fears. It's designed to test all incoming updates to Huawei hardware and software used on UK networks. The problem is that all of the staff are employed by Huawei; in 2013, the UK's Intelligence and Security Committee said it was concerned about the arrangement, which effectively relies on self-policing. The government agreed, and said it would investigate the processes inside the centre.

UK report says GCHQ spying wasn't illegal, but lacked transparency
UK data surveillance programs, including the bulk collection of data from ISPs, have been declared legal by a parliamentary committee. However, it also found them "overly complicated" and lacking in transparency. The report from the Intelligence and Security Committee (ISC) probed GCHQ initiatives that tapped massive amounts of emails and other private "upstream" data, often in conjunction with the NSA's PRISM program. The extent of the UK's involvement in that program was revealed by whistleblower Edward Snowden in 2013.

Gemalto: NSA attacked our SIMs, but not on a grand scale
SIM chip maker Gemalto has confirmed that US and UK intelligence services likely attacked it, but said it "could not have resulted in a massive theft of SIM encryption keys." Its comments stemmed from a recent Edward Snowden leak, which revealed a coordinated attack on Gemalto by the NSA and British GCHQ. Following an internal investigation, the previously low-profile company said that a "sophisticated" intrustion by the intelligence agencies did occur in 2010-11 for the purpose of intercepting encyption keys sent to carriers. The attacks consisted of email "phishing" and spying on office networks, and several attempts were made to access the PCs of individual Gemalto employees.

SIM card maker Gemalto investigates spy agencies' hack attack
When word of a savvy hack conducted by agents of two intelligence agencies against SIM maker Gemalto broke yesterday, company representatives seemed to be caught completely off-guard. Now, with egg on its face and a security backlash in the offing, Gemalto's publicly pledging to look into The Intercept's scary allegations. "We cannot at this early stage verify the findings of the publication and had no prior knowledge that these agencies were conducting this operation," the company's statement reads. "We take this publication very seriously and will devote all resources necessary to fully investigate and understand the scope of such sophisticated techniques."

US and UK spy agencies stole the secrets keeping your phone secure
You might not have heard the name "Gemalto" before, but you almost certainly have one of their products in your pocket. As the world's largest maker of SIM cards, it's a company that's directly responsible for making sure your cell phone connects to the right wireless network. According to documents released by Edward Snowden and obtained by The Intercept, though, it was also the target of a covert, coordinated hack committed by NSA agents and allies at Britain's Government Communications Headquarters. Their goal? To quietly get their hands on the encryption keys that keep our phone calls and text messages private so they could tap people's communications without raising suspicions.

Find out if the UK used NSA data to spy on you
While it's sadly likely that your communications have passed through an intelligence agency at some point, it's usually difficult to know just who got your data. However, you now have a rare opportunity to find out. Thanks to a ruling that the UK's GCHQ illegally spied on people using NSA databases, advocacy group Privacy International has posted a simple web form that lets you ask if you were caught in Britain's law-breaking dragnet -- and, as you might expect, petition against mass surveillance. This won't provide the most comprehensive results (you should use the official form if you're really worried), but it should still lead to GCHQ purging the relevant records if there's a match. The only big problem? The request is limited to the past data covered by the ruling, so there's no guarantee that you're truly off the radar. [Image credit: Christopher Furlong - WPA Pool/Getty Images]

UK government reveals its hacking guidelines
It's no secret that numerous countries see hacking as a viable security strategy, but the British government has been reluctant to admit as much. Ask it about GCHQ's ability to mess with communications, for example, and it will only say that whatever it does is legal and necessary (even if it isn't). The nation's leaders just got a little more honest, however: the UK Home Office has published the guidelines that law enforcement and spies follow when using "equipment interference" (read: hacking) to get into phones and PCs. The rule set largely deals with high-level issues such as proportional uses of hacks, data retention and the validity of warrants, but it's a rare acknowledgment that these digital intrusions even take place. It goes so far as to mention that the UK intercepts and bugs gadgets it wants to spy on, much like its American counterparts. Minister James Brokenshire claims that the government is being "as open as it can be" about its security policies by publishing the documents, and this is certainly a milestone given earlier secretiveness.

UK court rules that GCHQ unlawfully spied on British citizens
Ever since its surveillance tactics were thrust into the public spotlight, GCHQ has had a lot of questions to answer over its reported spying on British citizens. It hasn't exactly been forthcoming with information, but the Investigatory Powers Tribunal (IPT), an independent court set up to keep the UK's secret services in check, has enough evidence of GCHQ's wrongdoings to declare that the agency has been unlawfully snooping on those it's meant to be protecting.

UK spies collected journalists' email as part of a test
Want to know why many people don't like it when governments call for an end to encrypted communication? Here's why. A new round of Edward Snowden leaks at The Guardian has revealed that the intelligence agents at Britain's GCHQ collected email from major news outlets (including the BBC, Le Monde, the New York Times and the Washington Post) in 2008 while testing a system that stripped out data irrelevant to searches. While it's not clear that the agency singled out the press during the test, there's no indication that it got rid of the messages, either.

GCHQ is using an app to teach kids how to become codebreakers
The next time you need a new Android app to keep the little ones entertained, you should consider turning to the UK's GCHQ intelligence agency. No, really. Infamous for its surveillance capabilities exposed by whistleblower Edward Snowden, the (once) super-secret organisation has now released a kid-friendly tablet app focused on cryptography. Originally developed by GCHQ placement students, the Cryptoy app teaches children about traditional encryption methods such as shift, substitution, Vigenère and Enigma. Youngsters can then apply these techniques to create their own encoded messages and send them on to friends for decryption. Cryptography has come a long way since these classic ciphers were invented, but GCHQ says the basic principles are still relevant for modern code breakers. It's also planning an iOS version for next year, so if your kids are using an iPad they shouldn't be left out for too long. Passing notes around in class will never be the same again.

Judges rule that UK spying doesn't violate human rights
British spies may be peeking into webcams and modifying internet traffic, but all that is above board -- if you ask the UK's Investigatory Powers Tribunal, anyway. Its judges have ruled that the Government Communications Headquarters' (GCHQ) intelligence gathering practices aren't violating the European Court of Human Rights' safeguards for free speech and privacy. The Tribunal agrees that unchecked mass data collection would be illegal, but contends that the ways GCHQ selects and preserves that data are reasonable. It doesn't have "carte blanche" to do what it likes, according to the ruling.

Researchers link carrier-focused malware to US and UK spy agencies
Symantec said that the recently detailed Regin spyware looked like it was created for government surveillance, and there's now some strong support for that claim. Both Kaspersky Lab and Wired understand that the super-sophisticated malware was used to infiltrate both Belgian carrier Belgacom and cryptographer Jean-Jacques Quisquater. Given that the NSA and Britain's GCHQ have been linked to these malware attacks, it's easy to connect the dots -- from all indications, one or both spy agencies used Regin to snoop on these targets. There are also hints that it may have been used to hack into the European Commission back in 2011. The Commission's director of security couldn't tell Wired if the malware in that incident was the same, but the code involved was built from a "series of elements" that worked together, like Regin does.
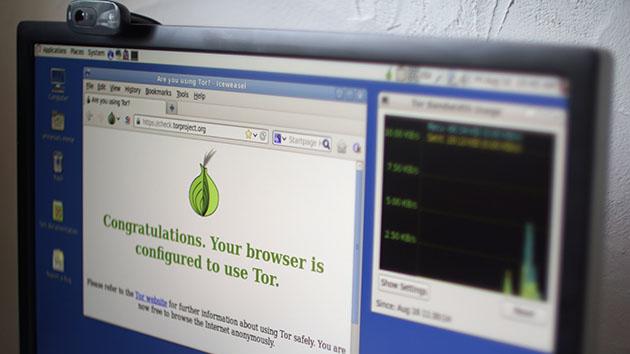
NSA and GCHQ employees may be undermining the agencies' work to hack Tor
It's no secret that US and British spy agencies are trying to crack the Tor network, but new information suggests that the agencies' floundering efforts may be sabotaged from within. For the uninitiated, Tor is a web browser that anonymizes a person's identity, location and browsing activity using various technologies -- it's also a known gateway to the so-called "dark-web" that hosts sites like the Silk Road. Naturally, spy organizations see it as a threat, but the Tor Project's Andrew Lewman says some of the agencies' employees are undermining their own hacking efforts. "There are plenty of people in both organizations who can anonymously leak data to us and say, maybe you should look ere, maybe you should fix this," he told the BBC in a recent interview. "And they have."

UK spies have scanned the internet connections of entire countries
You may know that the UK's GCHQ intelligence agency pokes its nose into people's internet service accounts, but it's now clear that the spy outfit is mapping the internet connections of whole nations, too. Heise has obtained documents showing that a GCHQ system, Hacienda, can scan every internet address in a given country to see both the connection types in use (such as web servers) as well as any associated apps. The scanning platform is looking for relevant targets and any exploitable security holes; if a target is running software with known vulnerabilities, it's relatively easy for agents to break in and either swipe data or set up malicious websites that trick suspects into compromising their PCs. Poring over this much data would normally be time-consuming, but there's a companion system (Olympia) that makes it easy to find useful information within minutes.

UK spy agency gives thumbs up to grad degrees in online security
Good internet security isn't just about having the right tools to fend off cyber attacks; you need smart people, too. The UK government clearly knows this, as GCHQ has just accredited Master's degrees in online security that live up to the intelligence agency's "stringent criteria." If you pursue the right grad studies at one of six British universities (including London and Oxford), you'll both be well-equipped to handle digital threats and get an edge when hunting for that first big InfoSec job.

The United Kingdom can manipulate major communication services, from Facebook to phone calls
British intelligence agency GCHQ is able to not just monitor, but also modify many of the world's most widely-used communications services: Facebook, YouTube, and phone calls are just a few of the services affected. The Intercept revealed the documents today (which can be read here), continuing reporter Gleen Greenwald's year-plus of working with whistleblower Edward Snowden on exposing the clandestine surveillance tactics of the United States and Britain. So, what exactly can the GCHQ do to these communications services? Beyond monitoring, of course; it's already been revealed that the GCHQ is doing that.






