Android apps used by troops in combat contained vulnerabilities
A whistleblower warned about the issues for a year before being acknowledged.
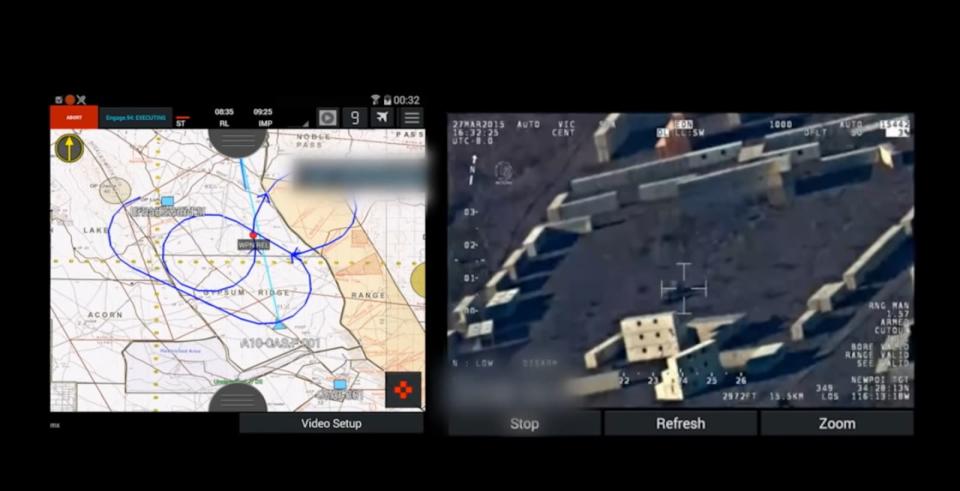
Two Android apps used by the US military in live combat situations contained severe vulnerabilities that could have allowed attackers to gain access to troops' information, a Navy Inspector General report revealed. The mobile apps offered real-time messaging to coordinate with other military branches, displayed mission objectives and goals, showed satellite images of surroundings and highlighted locations of nearby enemy and friendly forces.
According to the report, first published in March but made public today by ZDNet, the two apps in question are called KILSWITCH (Kinetic Integrated Low-Cost Software Integrated Tactical Combat Handheld) and APASS (Android Precision Assault Strike Suite) and were made available to military members through an app store managed by the National Geospatial-Intelligence Agency. A DARPA video on YouTube demonstrates one of the apps in action.
The apps were reportedly only meant for training exercises, so the developers were lax with security practices. Because of the slick interface and features, the apps became popular with US troops and allied forces and started to be used in live combat situations.
The Navy Inspector General determined most military branches failed to properly inform troops about the apps, which resulted in them being used in inappropriate settings. Perhaps the most troubling part of the report though was the IG's finding that a whistleblower had been warning about the security lapses for more than a year.
Anthony Kim, a civilian program analyst for the Naval Air Warfare Center Weapons Division (NAWCWD), first raised concerns about the apps in March 2017. He was ignored but kept raising the issue, only to get punished each time. Kim was scolded, had his pay reduced, placed on leave and eventually had his pay suspended and security clearance revoked. The report vindicated Kim and got his security reinstated.