A Beginner's Guide to Encryption
Mobile apps have replaced texting. Cloud storage have replaced pen drives. Hardly anything exists in the offline mode. Everything is online, interconnected and also increasingly prone to security attacks.
Even if you have nothing to hide, cyber security threats can cause serious damage in the form of identity theft or forgery. Here you can see the dark side of cybercrime report.
In fact, the US Federal Trade Commission says that it has tracked nearly 50% increase in online identity thefts since 2013.
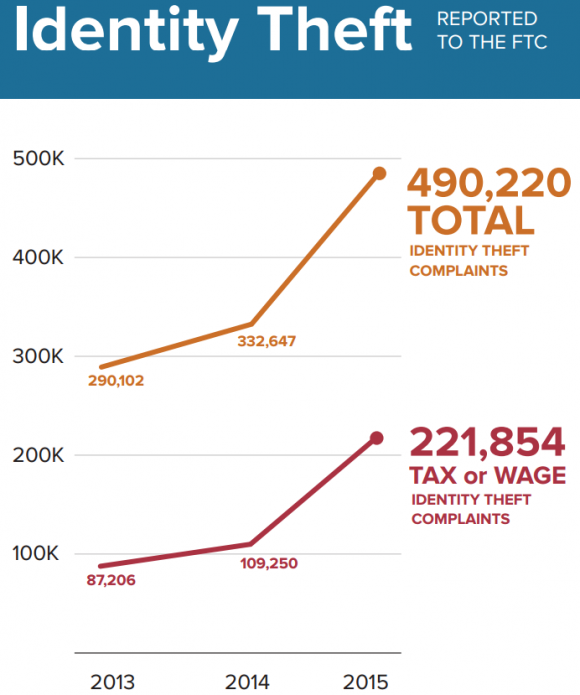
High-profile hacking and cyber attacks have also been reported on several entities including popular eCommerce stores like Target, HomeDepot, eBay, etc.
IT security measures help prevent enterprise-grade data loss. However, for regular and routine Internet safety, the need for a specific made security measure was felt.
Such a measure must be capable of keeping miscreants out while giving legitimate users safe access to data. Thus was born, Encryption.
What is Encryption?
Encryption is a proven way to protect information on the Internet. It scrambles text into something that only someone with a key or special password can read. Anyone else who manages to get the data will not be able to use it or read it without decoding.
Decoding an encrypted message is literally impossible since there will be hundreds of combinations and permutations that can be formed by the scrambled text.
Encryption has become to be accepted as a reliable way to slow down and even prevent cyber security threats. It is now considered to be the cornerstone technology in cyber security that even government security agencies are deploying to protect national digital treasures.
How does Encryption work?
Encryption is grounded on the age-old practice of cryptography. In the past, scholars used to decipher sacred texts and documents in scrambled language that only those with the knowledge of decoding it can read it.
Today, in the digital era, encryption is done using computers and algorithms which convert plain text into incorrigible text. The text which looks like jumbled code can be decoded back to plain text using an encryption key.
Encryption key
An encryption key is a string consisting of several bits which act as the key that decodes the scrambled code or text into readable content.

Workflow of an encryption key (Source: https://docs.oracle.com/cd/E19693-01/819-0997/images/pcrypt.gif)
The encryption key ensures that any unauthorised individual who accesses the data, sees only nonsensical text from which no meaningful information can be derived.
Thus, an encryption key ensures that exchange of information over the Internet happens only between trusted and authorised individuals.
In a real-life scenario, it encrypts the flow of information between the server and the web browser used by the client. Only such users who have the key to encrypt and decrypt data will be able to access it.
Types of Encryption
There are three main types of encryption: Hashing, Symmetric and Asymmetric encryption.
Hashing: In this form of encryption, a definite-length signature set is created for each data. Data which is deciphered using hashing cannot be reversed or changed. Thus, this ensures that data remains encrypted and protected at all times.
Symmetric method: The symmetric method of encryption uses a public key to encrypt and decrypt data. Refer image below.
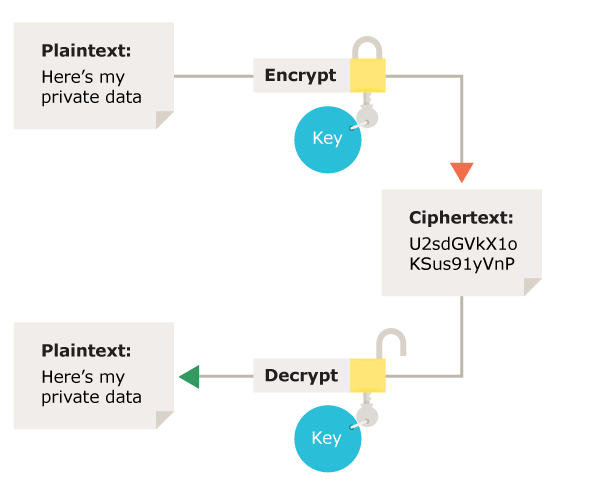
Image Source: ico.org.uk
Asymmetric encryption: In asymmetric encryption, a different key is used for encryption and for decryption. The key used for encryption is known as a public key and the one used for decryption is known as a private key.
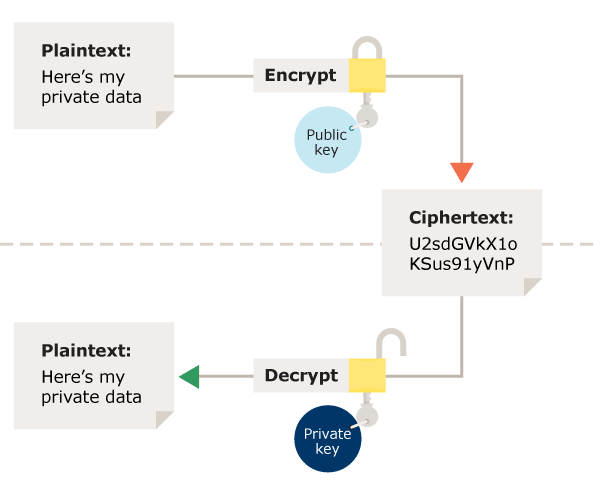
Image Source: ico.org.uk
Each method of encryption is best suitable for given scenarios. There is no one fit solution for all. For instance, hashing may be perfect for signups and logins, for websites and asymmetric encryption for high-level websites where login credentials need to be guarded heavily (For eg: banking and finance companies.)
How can businesses embrace encryption to ensure data security?
Encrypting cloud and email servers
With cloud becoming easily available and affordable, most small and medium enterprises are resorting to cloud solutions instead of having owned network solutions. Combined with that they use third party email services, which may not have the best security features at all times.
This causes a precarious condition giving an opportunity for hackers to penetrate the system and make way for sensitive information. The key is to encrypt cloud networks and email servers with an SSL certificate. An SSL certificate will ensure that all the data flow between the Internet and the browser is encrypted and safe from unauthorised infiltration.
Encrypt operating systems
Unlike in the earlier versions, the recent versions of Windows, Apple OS X and Linux come with system-level encryption. In Windows, it is referred to as BitLocker and in Apple systems, it is popular as FileVault. These applications are encryption and ensure high-level data security, similar to online banking websites for the exchange of data from and to the system.
Needless to say, upgrading to the latest OS with system-level encryption is a great start to ensure data security.
Set up minimum password strength
Strong passwords are the launchpads for encryption. In fact, history of data breaches pinpoints poor password strength as the main cause. According to a study by Lastpass, passwords are still the weakest links which hackers break to gain access to sensitive areas.
The remedy for this common trap is to raise the bar for password health. Passwords that satisfy minimum password strength like a combination of capital, small letter or special characters will help data breaches at bay. Alternatively, users may also be asked to change the password compulsorily every 30 days or such period as deemed fit for the organisation.
Finally..
Since 2016, the average number of ransomware attacks per day has increased to 4,000. Security is no longer a topic that businesses can bother less about. It is the only ray of hope to keep data secure in an increasingly complex and sophisticated digital environment.
Encryption is the first foot forward to ensuring data security. Encrypting email servers, cloud servers and operating systems can help reduce the number of data leaks that are bound to happen in an organisation. Depending on the organisation and its business model, the business can adopt encryption to stash away data from hackers.
