WannaCrypt
Latest

US recommends Windows users patch against worm vulnerability
Microsoft Windows users who haven't patched their OS (or are using an unsupported version) are at risk of attackers exploiting a vulnerability known as BlueKeep. The Cybersecurity and Infrastructure Security Agency (CISA), Homeland Security's lead cybersecurity agency, said it successfully tested a working exploit for the BlueKeep vulnerability. Specifically, the agency was able to remotely run code on a Windows 2000 computer using BlueKeep, it stated in an advisory. The bug effects computers that are running Windows 7 or earlier (as well as Windows Server 2003 and 2008), and gives potential attackers access through Microsoft's Remote Desktop Services.

US government names North Korea as the source of WannaCry
Donald Trump's homeland security adviser, Tom Bossert, said in a Wall Street Journal op-ed that "after careful investigation, the U.S. today publicly attributes the massive "WannaCry" cyberattack to North Korea." Coming during increasing tensions between the two countries over nuclear threats and Twitter outbursts, Bossert said this attribution is based on evidence and agrees with the findings from the UK and Microsoft.

'Basic IT security' could have prevented UK NHS WannaCry attack
England's National Health Service (NHS) could have avoided the ransomware hack that crippled its systems in May, according to a government report. "Basic IT security" was all that was required to prevent the "unsophisticated" WannaCry attack, which affected more than a third of NHS organizations, said the National Audit Office (NAO). The full scale of the incident saw over 19,000 medical appointments canceled, and computers at 600 surgeries locked down.

FedEx estimates ransomware attack cost $300 million
FedEx acquired Dutch shipper TNT Express last year for $4.8 billion, well before the NotPetya ransomware ran wild on TNT's systems June 27th, disrupting much of its shipping operation. Like the earlier WannaCry outbreak, NotPetya used a Windows exploit stripped from an NSA leak to spread across networks. According to FedEx, even though its services and critical systems have been restored, "TNT Express volume, revenue and profit still remain below previous levels." That adds up to a $300 million hit on its operating results, and the company raised the estimate of integrating TNT's systems with its own by $75 million over previous estimates.

'Shadow Brokers' threaten to release more hacking tools in June
An exploit that the "WannaCry" malware used to encrypt computers worldwide first appeared in a leak from "The Shadow Brokers," a group that claims to have stolen a number of tools from the NSA. Now the Shadow Brokers are back with a new blog post threatening more leaks. Through an intentionally sloppy writing style, the group taunts not only TheEquationGroup (read: NSA), but also Microsoft and its blog post blaming spy agencies, claiming that Microsoft is simply upset the NSA didn't pay to hold its vulnerability.

'WannaCry' ransomware showed traces of North Korean code
For all the damage the "WannaCry" ransomware has done, there's still one looming, unanswered question: who's behind it? At last, there might be a clue. Google researcher Neel Mehta has noticed that an early version of WannaCry's code shares similarities with a February 2015 sample from the Lazarus Group, a North Korea-linked outfit blamed for both the Sony Pictures hack as well as the Bangladesh Bank heist. The code changed between then and now, but it at least raises the possibility that North Korea was involved.

NHS Trusts ignored patch that would’ve averted malware disaster
The ransomware attack that crippled crucial NHS systems across the UK and continues to cause disruption could have easily been contained, according to NHS Digital. The body, which oversees data and IT infrastructure across the NHS, said hospitals and other arms of the service had ample time to upgrade their systems. The 'WannaCry' malware variant used a Windows exploit Microsoft patched in mid-March this year. At the end of April, NHS Digital notified staff and "more than 10,000 security and IT professionals," pointing them to a patch that would "protect their systems." It seems this advisory fell on some deaf ears, which explains why only certain NHS Trusts were affected.

Microsoft blasts spy agencies for hoarding security exploits
Microsoft is hopping mad that leaked NSA exploits led to the "WannaCry" (aka "WannaCrypt") ransomware wreaking havoc on computers worldwide. Company President Brad Smith has posted a response to the attack that roasts the NSA, CIA and other intelligence agencies for hogging security vulnerabilities instead of disclosing them to be fixed. There's an "emerging pattern" of these stockpiles leaking out, he says, and they cause "widespread damage" when that happens. He goes so far as to liken it to a physical weapons leak -- it's as if the US military had "some of its Tomahawk missiles stolen."
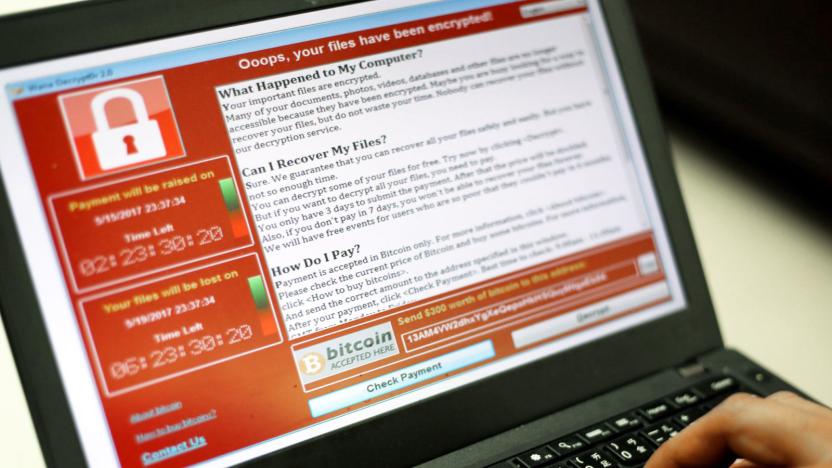
'WannaCry' ransomware evolves despite attempts to kill it
There were predictions that the fast-spreading "WannaCry " (aka "WannaCrypt") ransomware would quickly evolve to get around its domain-based kill switch, and, well... the predictions were right. Security researchers have discovered variants of the Windows malware that either have different kill switches (easy to stop by purchasing the web domain) or don't have a kill switch at all. MalwareTech's initial findings might have stopped the original WannaCry in its tracks, but that was really just a speed bump for malicious coders.

Microsoft patches Windows XP to fight 'WannaCrypt' attacks (updated)
Microsoft officially ended its support for most Windows XP computers back in 2014, but today it's delivering one more public patch for the 16-year-old OS. As described in a post on its Windows Security blog, it's taking this "highly unusual" step after customers worldwide including England's National Health Service suffered a hit from "WannaCrypt" ransomware. Microsoft patched all of its currently supported systems to fix the flaw back in March, but now there's an update available for unsupported systems too, including Windows XP, Windows 8 and Windows Server 2003, which you can grab here (note: if that link isn't working then there are direct download links available in the Security blog post). Of course, for home users, if you're still running one of those old operating systems then yes, you should patch immediately -- and follow up with an upgrade to something current. If you're running a vulnerable system and can't install the patch for some reason, Microsoft has two pieces of advice: Disable SMBv1 with the steps documented at Microsoft Knowledge Base Article 2696547 and as recommended previously. Consider adding a rule on your router or firewall to block incoming SMB traffic on port 445 Update: Microsoft legal chief Brad Smith has written a blog post that both calls for more help from customers (read: update more often) and chastises intelligence agencies for hoarding security exploits. They don't understand the risk to the public if the exploits leak, Smith says -- it's as if someone stole a batch of Tomahawk missiles. We wouldn't count on the NSA or other agencies heeding the call, but Microsoft clearly wants to make its frustrations heard.

'WannaCry' ransomware attack spreads worldwide (update)
England's healthcare system came under a withering cyberattack Friday morning, with "at least 25" hospitals across the country falling prey to ransomware that locked doctors and employees out of critical systems and networks. It's now clear that this is not a (relatively) isolated attack but rather a single front in a massive digital assault. Update 2 (5/13): In response to infections like the ones that crippled parts of the NHS system, Microsoft is releasing a patch for unsupported systems including Windows XP, Windows 8 and Windows Server 2003.





