Security
Latest

Carnegie Mellon reveals it was hit by a cyberattack over the summer
The Pittsburgh-based university known for its top tech and computer science programs said on Friday that the attack impacted up to 7,300 students, employees, contractors and other affiliates.

Apparel supplier for North Face, Vans admits its cyberattack led to a data breach of 35 million customers
If you've purchased from its major brands like Vans, North Face, Timberland, Dickies and more, you may have been impacted — but VF Corp still insists that the incident won't impact its financial performance.

Russian state-sponsored hackers accessed the emails of Microsoft’s ‘senior leadership’
A hacking group linked to a Russian intelligence agency accessed the emails of several senior Microsoft executives and other employees, the company disclosed Friday.

The year of the passkey is still far away
To give passkeys the credit they deserve, top security experts agree that the new way of logging in comes with greater security. Like every other security advancement from SMS-based multifactor authentication to hardware authentication keys, however, adoption lags because people still hesitate to make the leap.

What is credential stuffing and how do you keep your accounts safe from it
Credential stuffing has become so prevalent, that you’ve likely already fallen victim.

Toronto Zoo hit by a cyberattack, but don't worry, the hackers didn't go after the animals
The zoo reassured the public that the attack did not impact animal wellbeing and support staff, but it was still determining possible consequences for human visitors.

China says it can bypass AirDrop privacy measures to identify message senders
A Chinese state-backed institute has reportedly found a way to identify people who send files and messages via AirDrop. Police are said to have used the method to identify several people suspected of sharing 'undesirable content.'

Philips' smart deadbolt will unlock a door by looking at your palm
Philips teased its first-ever smart deadbolt that works using a touch-free palm reading system at CES 2024.

Apple reportedly faces pressure in India after sending out warnings of state-sponsored hacking
Indian authorities allied with Prime Minister Narendra Modi have questioned Apple on the accuracy of its internal threat algorithms and are now investigating the security of its devices, according to The Washington Post.

CBS and Paramount’s parent company reports hack affecting over 80,000 people
National Amusements, CBS and Paramount’s parent company, confirmed a year-old hack this month affecting 82,128 people. TechCrunch first reported on the breach, revealed in a company legal filing with Maine’s Attorney General under a 2005 state digital privacy law.

First American discloses a 'cybersecurity incident,' a few years after its major leak
First American, a real estate and mortgage financial firm, experienced a "cybersecurity incident" impacting operations, the company posted on its website on Thursday.
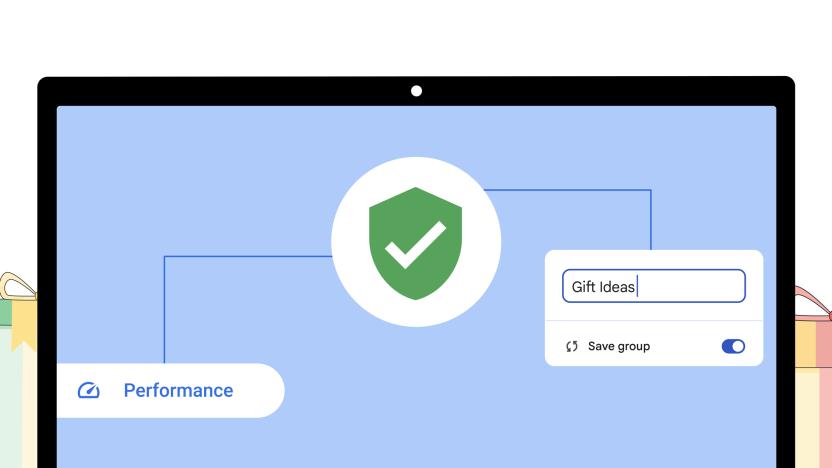
Google tweaks Memory Saver and tab group features in latest Chrome update
Google Chrome is getting new security and performance features. The web browser’s latest version (M12) upgrades Safety Check and Memory Saver while adding the ability to save tab groups.

QR code attacks probably aren’t coming for your scan-to-order menus
The fanfare around these attacks, however, mostly outweighs the threat of using QR codes in your daily life.

The DOJ says it disrupted the Blackcat ransomware group
The US Department of Justice says it has disrupted the Blackcat ransomware group. Also called ALPHV or Noberus, the group has targeted over 1,000 computer networks and extorted millions of dollars from victims.

Major apparel supplier behind North Face and Vans hit by cyberattack, disrupting its holiday fulfillments
VF Corporation reported in a Securities and Exchange Commission filing on Monday that it had been hit by a cyberattack.

Here’s everything you should do to up your security before next year
Here's a quick holiday checklist you and your loved ones can spend an hour doing during your holiday downtime to set up for a more secure year.
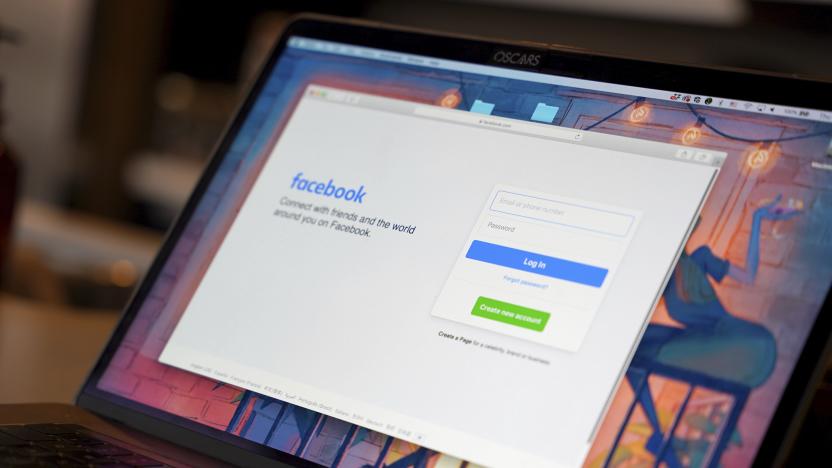
How a social engineering hack turned these Facebook pages into a dumping ground for spam
Much of the cyber criminality today is social engineering jobs, ripping off mid-level creators with much fewer resources than a multinational corporation, but also significantly less technical know-how.

Apple and Google are probably spying on your push notifications
Push notifications, the dings you get from apps calling your attention back to your phone, may be handed over from a company to government services if asked. But it appears the Department of Justice won't let companies come clean about the practice.
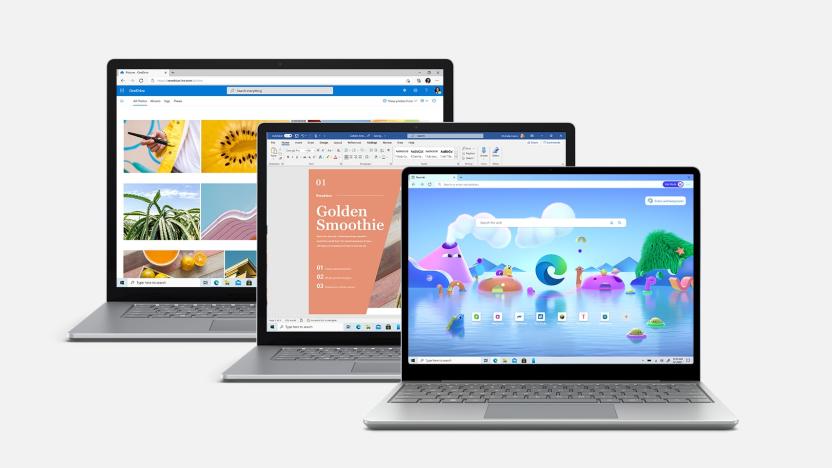
Windows 10 will receive its final security update in October 2028
Microsoft's Extended Security Update (ESU) program for Windows 10 will stretch its lifespan by up to three years.
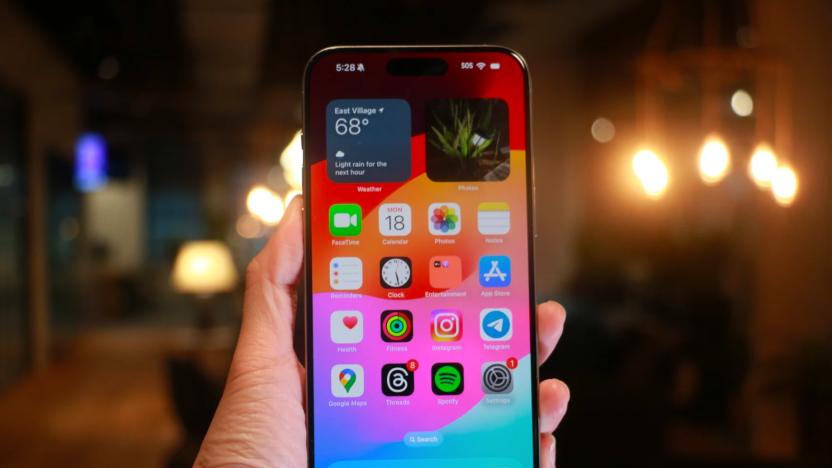
Apple patches two security vulnerabilities on iPhone, iPad and Mac
Apple pushed updates to iOS, iPadOS and macOS software today to patch two zero-day security flaws. The company suggested the bugs had been actively deployed in the wild.






