Security
Latest

Can digital watermarking protect us from generative AI?
Digital watermarks might help content creators better authenticate their online works in an age of generative AI misinformation.

Self-proclaimed 'gay furry hackers' breach nuclear lab
Nuclear research hub, the Idaho National Laboratory (INL), confirmed that it fell victim to a data breach on Tuesday.

Smarter public transit comes at the cost of rider anonymity
Payment information, location data and trip patterns can all be attached to our ridership data. Agencies say they use it to better understand how riders use the services and make improvements. But the flip side is transit agencies selling user data to advertisers like a lot of private companies do, or sharing it with law enforcement.

Hackers use a new SEC rule to snitch on the company they infiltrated
A hacking group deployed a surprising tactic after infiltrating a financial software company’s network. They reported the breach to the US Securities and Exchange Commission (SEC).

An email vulnerability let hackers steal data from governments around the world
Google's Threat Analysis Group revealed on Thursday that it discovered and worked to help patch an email server flaw used to steal data from governments in Greece, Moldova, Tunisia, Vietnam and Pakistan.

Amazon’s dinky Astro robot is now available as a security guard
But replacing your flesh-and-blood security guard won't be cheap.

Cybercriminal gang LockBit leaks alleged Boeing data
The leak includes more than 43GB of backup files that LockBit says it stole from Boeing, according to Bleeping Computer.
Data breach of Michigan healthcare giant exposes millions of records
Michigan-based healthcare nonprofit McLaren Health Care notified more than 2 million people about a data breach exposing personal information on Thursday, according to a data breach notification report.

Every car is a smart car, and it's a privacy nightmare
The technology in today’s cars has the ability to collect these kinds of personal information, and the fine print of user agreements describes how manufacturers get you to consent every time you put the keys in the ignition.

Researchers posed as foreign actors, and data brokers sold them information on military servicemembers anyway
Researchers at Duke University released a study on Monday tracking what measures data brokers have in place to prevent unidentified or potentially malign actors from buying personal data on members of the military.

Ace Hardware's online ordering and other systems are still down due to a suspected cyberattack
Home improvement retailer Ace Hardware still can't take online orders as of Friday while it recovers from a cyberattack impacting almost 1,000 servers.

Surfshark VPN review: Basic protection for all of your devices
Surfshark VPN is one of the top VPN services available now, and it's particularly good for those who want to connect multiple devices. Here's Engadget's Surfshark VPN review.

Proton VPN review 2023: Why it's our top-choice VPN
Proton promises “privacy by default,” but that left me wondering if the company meant rigorous security testing — and if a focus on privacy would take away from ease of use. Because it balanced all of the above, Proton VPN landed at the top of our list.

Crunchyroll will pay you $30 for violating your data privacy rights
The anime-streaming service chose to settle with its customers in a class action suit for digital privacy violations.

The SEC is said to be investigating a Twitter security flaw from the pre-Musk era
The SEC is reportedly looking into how Twitter (now X) a security issue in 2018 that led to users' personal information being exposed. The agency is looking into whether executives at the time managed the situation appropriately.

How hackers are using Bluetooth to track police activity
A Bluetooth identifier seems trivial, but it could reveal a lot of information about where cops are and what they’re up to, like when their body cams are recording or they turn on the sirens to respond to a call.

Sony confirms data breach affecting nearly 7,000 employees
Sony Interactive Entertainment (SIE) has warned around 6,800 current and former employees that their personal data was accessed via a data breach.

NordVPN review: A bit too overhyped for the price
You may know NordVPN from its popular ambassador program, taking social media by storm as influencers sign up to make money advertising the virtual private network. But despite its popularity, it didn’t make the list of the nine top providers we published in June.

Sony investigates the alleged data breach that has led to hacker infighting
On Monday, relatively new hacking group Ransomed.vc made the lofty claim that it had successfully compromised "all" of the company's systems, as reported by Cybersecurity Connect. Now a second threat actor has leaked the data believed to be in Ransomed.vc's possession, claiming the former are "scammers" trying to "chase influence."
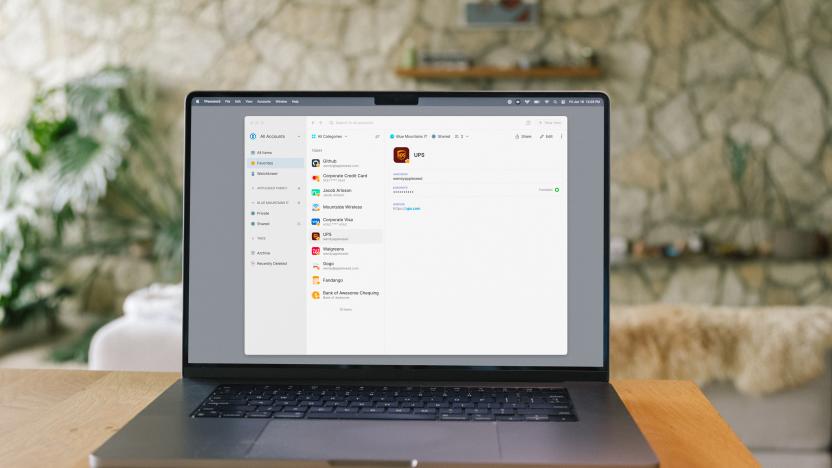
Passkey support is finally available in 1Password
The popular Password manager tool, 1Password, is rolling out support for passkeys. It will be available on desktop browsers, as well as on iOS 17 devices.






