spoofing
Latest

FCC proposes record-setting $225 million fine against robocallers
The FCC has proposed fining robocallers a record $225 million for making 1 billion spoofed calls in just five months.

Security firm details how hackers stole $1.3 million in wire transfers
The thieves targeted high-ranking officials in those companies, including CEOs and CFOs, via phishing attacks.

FCC will require phone carriers to authenticate calls by June 2021
The FCC announced today all carriers and phone companies must adopt the STIR/SHAKEN protocol by June 30th, 2021. The regulatory requirement is designed to combat robocalls, specifically those that try to hide their phone numbers by allowing carriers to authenticate caller IDs.

FCC could require phone companies to authenticate calls
Today, FCC Chairman Ajit Pai proposed new rules that would require phone companies to adopt the STIR/SHAKEN protocol, an increasingly popular method for caller ID authentication. The rules are meant to combat robocalls, specifically those that spoof phone numbers, and the FCC is expected to vote on them later this month.

FCC asks telecom companies to help trace international robocalls
Last year, the Federal Communications Commission (FCC) banned robocalls from international numbers. Now, it's calling on phone companies to help trace international robocalls back to their "fraudster" sources. Today, the FCC sent letters to seven gateway service providers asking them to help track down robocall sources, prevent apparently illegal traffic originating outside the US and provide more info on how they may be facilitating illegal calls.

T-Mobile and Sprint can now verify calls across their networks
Today, T-Mobile and Sprint are rolling out number-verification to customers across both networks. Using the STIR/SHAKEN standards recommended by the FCC, the carriers hope to better fight robocalls. Ideally, this will make it harder for spammers to spoof numbers and give customers more confidence that the number calling them has not been ripped off by a robocall.
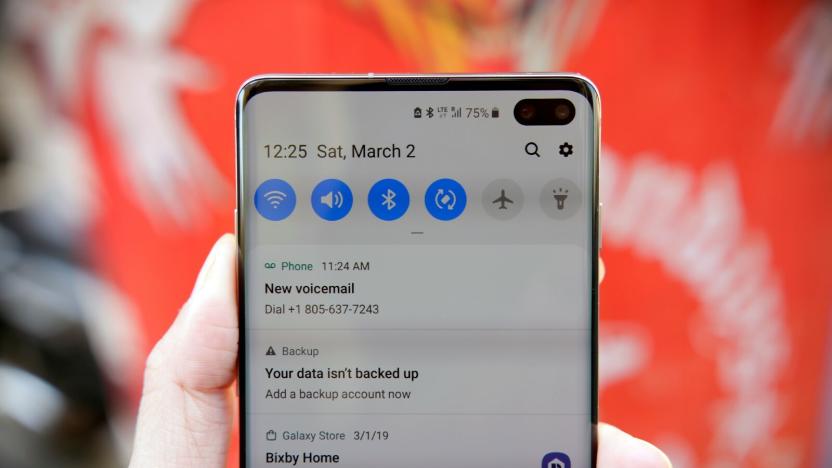
AT&T phones now show when calls come from verified numbers
AT&T is making good on its promise to validate calls and fight robocallers. The carrier has enabled validation displays that let you know when a call really did come from a given number. You'll need a Galaxy S10, Galaxy S10+ or LG V40 ThinQ to use this away from home (it's also available for digital home phone users), but it works same way regardless of platform. If a call has been validated ,you'll see a green checkmark next to the number as well as "valid number" below.

FCC bans spoofed text messages and international robocalls
This week the FCC voted to approve rules that ban spoofing text messages and international robocalls. The new rules close long-standing loopholes in the Truth in Caller ID Act, which banned spoofing domestic calls but made it hard for the FCC to combat malicious text messages and calls coming from overseas. The FCC now has the legal authority to punish the "bad actors" behind these scams.

FCC Chairman wants to ban caller ID spoofing for text messages
FCC Chairman Ajit Pai is advancing the war against robocalls. Today, he proposed adopting rules that would ban caller ID spoofing of text messages and robocalls originating outside of the US. More than 40 state attorney generals have urged the FCC to adopt the new rules, and the Commission is scheduled to vote on them at its August 1st meeting.

FTC crackdown targets operations responsible for one billion robocalls
The Federal Trade Commission (FTC) and its law enforcement partners are cracking down on robocallers. Today, the FTC announced that it's filed 94 actions against organizations responsible for more than one billion illegal calls. As part of "Operation Call it Quits," the FTC has opened four new legal cases and three new settlements, bringing the number of cases the FTC has filed against robocallers to 145.

T-Mobile starts verifying callers to fight spam
More US carriers are taking steps to prevent junk calls from reaching your phone. T-Mobile has launched a Caller Verified system that uses new standards (SHAKEN and STIR) to fight caller ID spoofing and ensure the number you see is real. Ideally, this makes it harder for ad spammers and tech support scammers to dodge screening efforts and blacklist apps.

iPhones may soon be able to automatically detect spam calls
Apple feels your spam call pain. The company apparently filed a patent called "Detection of spoofed call information" that would enable an iPhone to check whether a call is legitimate. If it's not, the phone would automatically either display a warning to the user or prevent call alerts, such as ringing and vibration. The patent was first spotted by Apple Insider.

FCC seeks $37.5 million fine on firm that spoofed consumer numbers
The FCC is looking to fine an Arizona-based company $37.5 million for making spoofed telemarketing calls. The company, Affordable Enterprises of Arizona, made more than 2.3 million calls over the course of 14 months, often masking its own number with those of consumers in the area. The FCC says this is the first major action taken against a company involved in such a practice. While the commission has issued robocall fines before, in those cases, the numbers spoofed were often ones not currently in use.

Security flaw left Safari and Edge users vulnerable to fake websites
A security researcher uncovered a flaw in both Safari and Microsoft's Edge browser that allowed the URL of a safe website to be displayed in the address bar while users were actually being taken to a different, and possibly malicious, website. Rafay Baloch spotted the security issue and notified Apple and Microsoft in early June. But while Microsoft issued a fix in August, Apple has yet to respond to Baloch's report.

Permanent LTE exploits steer users to rogue websites
LTE was theoretically supposed to fix the security holes baked into earlier wireless standards, but it isn't completely immune. An international team of researchers has discovered a attack methods (nicknamed aLTEr) that takes advantage of inherent flaws in LTE to direct users to hostile websites. An active exploit uses the lack of integrity checks in LTE's lower layers to modify the text inside a data packet. Since that's easy to determine with DNS packets, which direct traffic to website addresses, you can steer requests to malicious DNS servers and thus take the user to a website of your choice.

US reportedly launches probe into cryptocurrency price-fixing
It feels like cryptocurrencies like Bitcoin are going mainstream. They're becoming more heavily regulated around the world, in diverse places like Japan and New York. Now people are being investigated for price fixing. According to Bloomberg, the US Justice Department has opened a private criminal probe into traders who may be manipulating the price of Bitcoin and other digital currency products.

ICE insists it doesn’t use Stingrays to track undocumented immigrants
In a letter (PDF), the acting director of the Immigration and Customs Enforcement (ICE) said that the agency doesn't use its Stingray mobile call-intercepting devices while enforcing immigration laws. It does deploy them when pursuing criminal suspects, however, and individual agents might use them while acting in a joint task force with other federal officers.

Position tracking protects drone herds against hackers
Much ado has been made over flying drones in groups, but there hasn't been much thought given to protecting autonomous drone groups against security breaches. What happens if someone impersonates enough drones to hijack their collective decision-making process? MIT might have a viable defense. Its researchers have developed a positioning technique that would prevent and mitigate these kind of impostor attacks. The key is to give each drone a wireless fingerprint that reflects its interaction with the environment -- effectively, the network can tell the difference between the actual drone pack and a fraud operating from the outside.

Trader pleads guilty to sparking stock market 'Flash Crash'
If you were trading on an American stock market on May 6th, 2010, you probably had a minor heart attack: the "Flash Crash" that day sent the Dow Jones Industrial Average down 1,000 points (600 in the first 5 minutes) and recovered virtually all its value in the space of just 15 minutes. However, investigators eventually discovered that the crash was the result of intentional manipulation... and now, investors are getting some justice for that manufactured crisis. Navinder Sarao (above), a British trader extradited to the US, has pleaded guilty to charges of both wire fraud and spoofing that came from using automated trading software to make "at least" $12.8 million in illegal profit from the crash and beyond.
Security writer recovers from massive revenge cyberattack
Journalists are no stranger to making enemies bent on retaliation. However, it's becoming increasingly difficult to survive that retaliation in the internet era... just ask security writer Brian Krebs. An unknown party knocked his website offline last week with a massive distributed denial of service attack (620Gbps of non-stop data) as revenge for exposing two major cyberattack sellers who've since been arrested. He's only back online after taking advantage of Alphabet's Project Shield, which protects journalists against censorship-oriented denial of service campaigns. His previous anti-DDoS provider, Akamai, had little choice but to drop him -- the company tells the Boston Globe that a sustained attack on that level would have cost the company "millions."







