vulnerability
Latest

Apple tries to clear up Google's claims about iOS vulnerabilities
Apple has taken issue with Google's findings about exploit-laden websites injecting malicious code into iPhones. Last week, Google published a blog post describing how a handful of hacked websites had taken advantage of an iOS vulnerability. Today, Apple shared a rebuttal.

Vulnerability lets text messages steal emails from Android phones
Bogus text messages aren't just being used to send you to malicious websites or crash your phone -- in some cases, they can hijack your emails. Check Point Research has discovered a vulnerability in phones from Huawei, LG, Samsung and Sony that lets attackers use custom SMS to intercept all email traffic on target devices. The attack uses the common Open Mobile Alliance version of over-the-air provisioning, a carrier technique for deploying settings to new phones, to access emails. The attacks require different methods depending on the phone and available info (such as IMSI numbers and requesting PIN codes), but the result is the same: intruders trick users into compromising their phones through messages that pose as network settings changes.

Twitter temporarily disables tweeting via SMS after account hijacks
Twitter isn't taking any chances in the wake of hackers compromising the accounts of celebrities and its own CEO. The social site is "temporarily" disabling the option to tweet via SMS until there's greater security in place. Carriers need to address "vulnerabilities" in their systems, the company said, while Twitter itself planned to tackle its reliance on linked phone numbers for two-factor authentication. It'll reinstate SMS tweeting in regions that need it for "reliable communication," but it's working on a long-term solution.

Sites stealing iPhone data reportedly targeted Uyghur Muslims
The websites stealing data from iPhones might have been used for particularly sinister purposes. TechCrunch sources claim the sites were part of a state-sponsored campaign, presumably from China, targeting the country's Uyghur Muslim population. The pages would have let China swipe sensitive info like messages and passwords, not to mention track their locations. Apple quietly fixed the issue with iOS 12.1.4 in February, but it's possible that thousands of Uyghurs' phones were compromised before then.

Researchers found another way to potentially clone Model S key fobs
Last year, researchers discovered a vulnerability in the Tesla Model S key fob that would've allowed thieves to clone it in just a couple of seconds. The automaker and the key fob's manufacturer, Pektron, created a new version that upgrades its 40-bit encryption to an 80-bit one to make it harder to crack. But now Lennert Wouters of Belgian university KU Leuven has revealed (as reported by Wired) that it's still possible to wirelessly crack the new key fob's encryption.

Apple re-fixes a bug that let users jailbreak iPhones
Apple fixed a vulnerability that temporarily allowed hackers to jailbreak iPhones. The bug was first fixed in iOS 12.3 but reintroduced in iOS 12.4. Hackers discovered the flaw earlier this month and shared a free public jailbreak just for the fun of it. Today, Apple released iOS 12.4.1, which should take care of the vulnerability once and for all.

Hackers make jailbreaking iPhones a thing again
In the iPhone's early days, hackers would "jailbreak" the iPhone in order to install third-party apps that weren't available through the App Store. It's been a while since anyone seriously needed to jailbreak their iPhone, as there are plenty of apps and more customizable operating systems to choose from. But this weekend, hackers dusted off their jailbreaking skills when a vulnerability was discovered in iOS 12.4. Security researcher Pwn20wnd released the first free public jailbreak for a fully updated iPhone in years.

Even DSLR cameras are vulnerable to ransomware
Cameras are among the few devices that don't connect to the internet, so you'd think they'd be immune to hackers. However, researchers have discovered that some DSLRs and mirrorless cameras are actually vulnerable to ransomware attacks, of all things. Once in range of your camera's WiFi, a bad actor could easily install malware that would encrypt your valuable photos unless you paid for a key.

Google researchers discovered serious iOS security flaws
Six critical security vulnerabilities that were patched in the iOS 12.4 update released earlier this month were originally discovered by security researchers at Google. Natalie Silvanovich and Samuel Groß, two members of Google's Project Zero bug-hunting team, alerted Apple to the issues. Silvanovich will be laying out the details on several of the bugs and provide a demonstration of exploits in action at the Black Hat security conference set to be held in Las Vegas next week.

A Bluetooth vulnerability could give hackers your location
Your Fitbit and other Bluetooth gadgets could be giving away your location data. Researchers from Boston University (BU) detected a vulnerability in several high-profile Bluetooth devices that could allow third-parties to determine your location and other sensitive information. In the wrong hands, that information could be used for stalking or abuse. That's especially concerning given that basically everyone is carrying around a Bluetooth device.

Apple disables its walkie-talkie Watch app due to vulnerability
Apple has disabled its Walkie Talkie Watch app due to a vulnerability that could've allowed someone to listen in on other iPhones, the company told Techcrunch. In a statement, Apple said that the vulnerability -- which requires specific conditions and actions to exploit -- hasn't been used against anyone as far as it knows. It apologized to users and said it would restore the app once a fix is found.

Apple quietly updates Macs to remove Zoom webcam exploit
It's not just Zoom scrambling to fix the exploit that allowed intruders to hijack Mac webcams. Apple has issued a silent, automatic update to macOS that removes the web server used to streamline access to the video conferencing app. The update isn't completely necessary when Zoom has already issued its own patch, but this ensures that people running older Zoom releases won't be vulnerable.

Zoom will remove server behind Mac webcam security hole
Zoom is acting quickly on the security flaw that let intruders hijack Mac users' webcams. The video conferencing firm is releasing a patch on July 9th (that's today, if you're reading in time) that removes access to the local web server behind the vulnerability. It'll also let you manually uninstall Zoom and remove all traces of the app so that there's no chance of an exploit later on. Another update, due for the weekend of July 12th, will also ensure that rookies who choose "always turn off my video" will automatically have their preferences honored in those situations where a meeting host would normally require that video switches on.

US Cyber Command warns of nation-state hackers exploiting Outlook
The recent surge in state-backed hacking campaigns isn't dying down any time soon. US Cyber Command has reported that unnamed state actors are making "active malicious use" of a 2017-era Outlook vulnerability (long since patched) to escape the email client's sandbox and run malware on a target system. While officials didn't say who was involved, some clues have hinted at a possible connection to Iran.

EA patched Origin security flaws that put millions of users at risk
EA patched flaws in its Origin platform that could have enabled hackers to hijack and exploit millions of users' accounts. The vulnerabilities were spotted by Check Point Research and CyberInt, and once exploited, they could have allowed player account takeover and identity theft. The cybersecurity companies alerted EA, which was quick to take action.

Senate finds US agencies left security holes untouched for a decade
It's almost a truism to state that government IT security is frequently lacking, but a new Senate subcommittee report has underscored just how severe the problem is. Investigators found that several federal agencies (including the State Department, Homeland Security and the Social Security Administration) didn't adequately protect personal data, and that six of them hadn't installed security patches in a "timely" fashion to close vulnerabilities. In some cases, these flaws had lasted for roughly a decade or more.
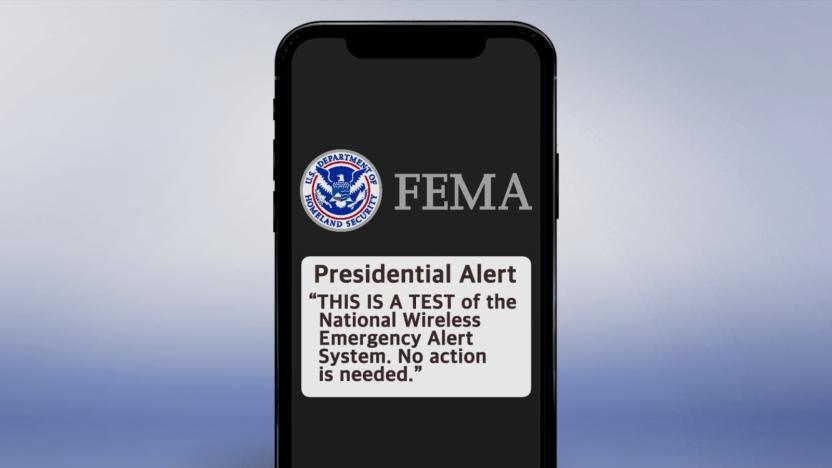
FEMA's presidential alerts are an easy target for spoofing attacks
Last fall, FEMA conducted the first nationwide test of its Wireless Emergency Alert (WEA) system when it beamed a "presidential alert" to all capable phones in the US. WEA has long been used to send alerts about missing children, natural disasters and other dangerous events. But a few years ago, the FCC voted to expand WEA so that, among other changes, government officials could write longer messages. Now, researchers from the University of Colorado Boulder warn that WEA's presidential alerts can be easily spoofed.
Indian streaming giant broke Safari support to deal with security hole
Websites tend to drop support for a particular browser due to obsolescence or just a lack of functionality, but India's biggest streaming service apparently had another reason: a piracy-friendly security hole. TechCrunch sources understand that Disney-owned Hotstar disabled Safari support (both desktop and mobile) on June 7th to limit the effects of a flaw that let people bootleg videos, including premium material.

Exposed database revealed security details for large hotel chains
Yet another unprotected database could pose a security risk -- this time if you're a traveler. VPNMentor researchers have discovered an exposed database that contained security audit logs for hotels run by the Pyramid Hotel Group, including numerous locations attached to major chains. Affected chains included Marriott's Aloft Hotels in Florida, Tarrytown House Estate in New York and multiple Irish hotels (such as Temple Bar), and might include more -- Pyramid operates hotels on behalf of Sheraton, Westin and others.

Mac security hole reportedly lets attackers bypass app safeguards
Apple may have another Gatekeeper security flaw on its hands. Researcher Filippo Cavallarin has detailed a macOS vulnerability that he said would let attackers install malware without the usual permission request. As Gatekeeper considers network shares to be 'safe' locations that don't require permission checks, an intruder just has to trick the user into mounting one of those shares to run the apps they like. A maliciously crafted ZIP file with the right symbolic link could automatically steer you to an attacker-owned site, for example, and it would be easy to trick someone into launching a hostile app -- say, a virus masquerading as a document folder.




