Replacement screens can be used to hijack your phone
New study finds hidden chips in phone parts can compromise your device.
A new study has shown that one of the most common fixes to a stock smartphone ailment can be used to steal your data, and compromise your device. In the newly published paper, researchers from Israel's Ben-Gurion University of the Negev reveal how a replacement screen can easily be altered to override your mobile. By embedding a malicious integrated chip within a third-party touchscreen, the research team were able to manipulate the communications system on a Huawei Nexus 6P and LG G Pad 7.0. This essentially allowed them to record keyboard inputs, snap pictures of the user and forward them via email, install apps, and direct the user to phishing websites. A second class of attack also saw them exploit vulnerabilities in the handset's operating system kernel.
Scariest of all, the researchers claim these hazardous screens can be made to look identical to the real thing -- meaning even handset technicians may not be able to distinguish the difference. Furthermore, the entire process is file-less, allowing it to go undetected by anti-virus software.
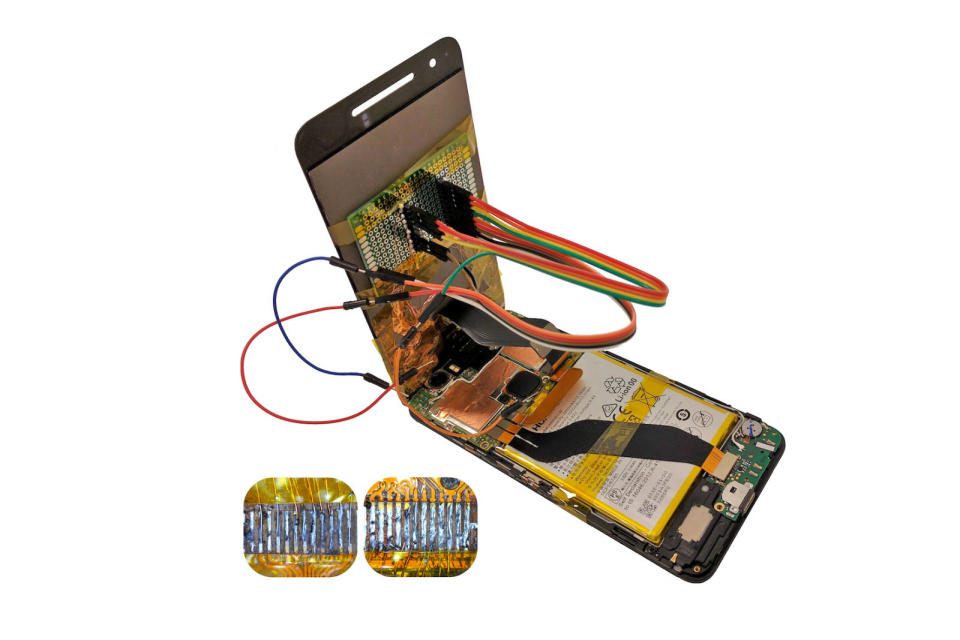
This type of low-cost attack is known as the "chip-in-the-middle" scenario. To carry out their malicious tasks, the researchers used an Arduino platform running on an ATmega328 micro-controller module. They also used an STM32L432 micro-controller, adding that most other micro-controllers could also do the job. They then used a hot air blower to separate the touchscreen controller from the main assembly boards, in order to access its copper pads. Next, they soldered a copper wire to attach their chips to the device.
Although this set-up looks far from inconspicuous, the team claims a little more effort could easily hide the altered part within a reassembled device. It's not just Android phones that are at risk either. The paper also indicates that iPhones could fall prey to the same types of attacks.