Sophisticated Android malware tracks all your phone activities
It targets Middle East victims for cyber espionage purposes.
An advanced type of malware can spy on nearly every Android smartphone function and steal passwords, photos, video, screenshots and data from WhatsApp, Telegram and other apps. "ZooPark" targets subjects in the Middle East and was likely developed by a state actor, according to Kaspersky Lab, which first spotted and identified it.
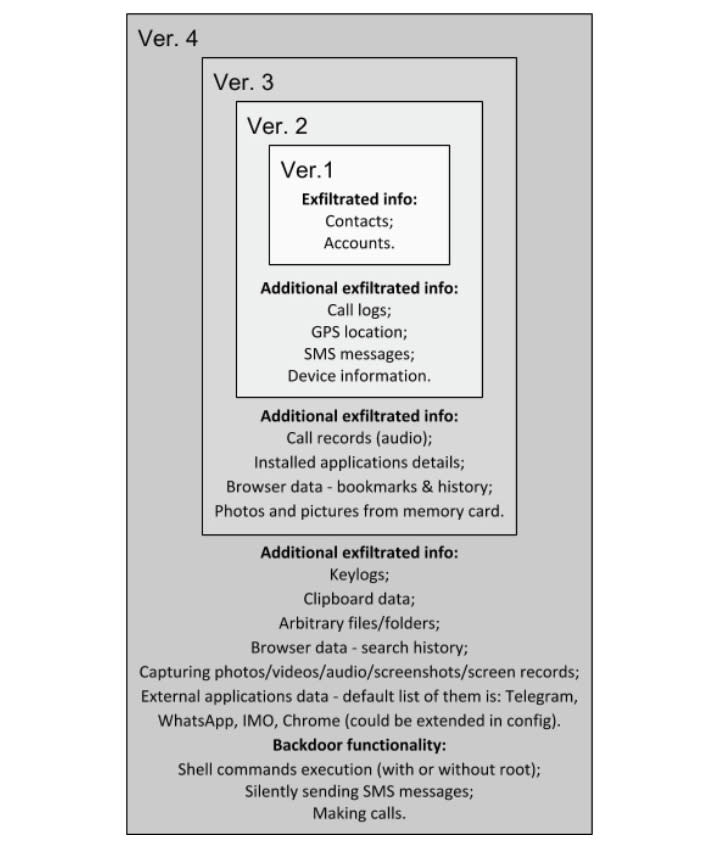
ZooPark has evolved over four generations, having started as simple malware that could "only" steal device account details and address book contacts. The last generation, however, can monitor and exfiltrate keylogs, clipboard data, browser data including searching history, photos and video from the memory card, call records and audio, and data from secure apps like Telegram. It can also capture photos, video, audio and screenshots on its own, without the subject knowing. To get the data out, it can silently make calls, send texts and execute shell commands.
Kaspersky -- a company with its own spotty security history that has been banned by the US government -- said that it has seen less than 100 targets in the wild. "This and other clues indicates that the targets are specifically selected," Kasperky Lab's Alexey Firsh told ZDNet. It also implies that the campaign is backed by a nation state, though the security firm didn't say which.

At the same time, Kaspersky suggested that the malware might not have been built in-house. "The latest version may have been bought from vendors of surveillance tools," it wrote. "That wouldn't be surprising, as the market for those espionage tools is growing, becoming popular among governments, with several known cases in the Middle East."
As is now known, a lot of those tools came from the US government itself. A group called Shadow Brokers famously stole exploits from the NSA -- some of the zero day, unpatched variety -- and eventually released them to the public. In other words, a hacking group was able to obtain malware from what should be the most secure agency in the world. That's one of the reasons that security experts and companies like Apple don't trust the US government with device backdoors.