Google stats show how much a recovery number prevents phishing
And that for most, multifactor via device prompt is as effective as a key.
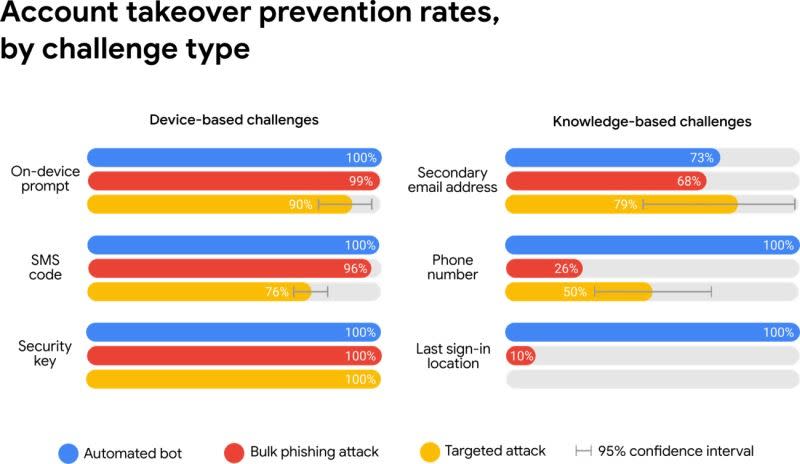
In case you haven't already set up a recovery phone number for your Google account, and enabled extra security features like multifactor authentication, the search giant is using hard data to explain why you should. Interestingly, studies (1)(2) researchers presented this week at The Web Conference found that simply adding a recovery phone number to an account blocked 100 percent of automated attacks, 99 percent of bulk phishing attacks and 66 percent of targeted attacks during the period they investigated.
That's why you should take advantage of a tool like the Security Checkup now, while your account is still secure, and get at least that level of protection enabled.
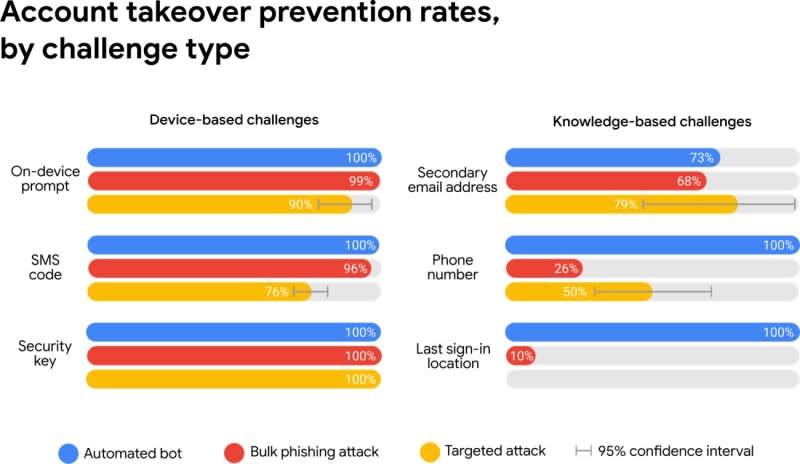
While SMS verification can be defeated by a targeted attack, Google's ability to do things like send a prompt to a connected phone or have users verify where they last log in also help block sign-ins it thinks are suspicious. If you're logging in on a brand new device or from a new location, then you should expect a little more scrutiny, however because 38 percent of users didn't have access to their phone, and 34 percent couldn't get to a secondary email address, the worry is that requiring challenges all the time will increase account lockouts.
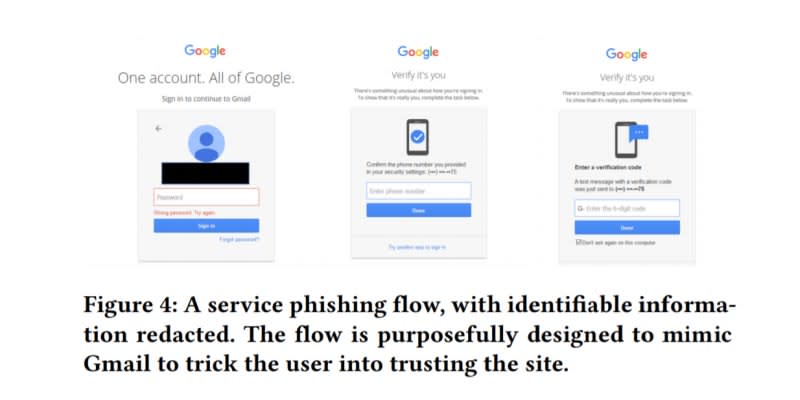
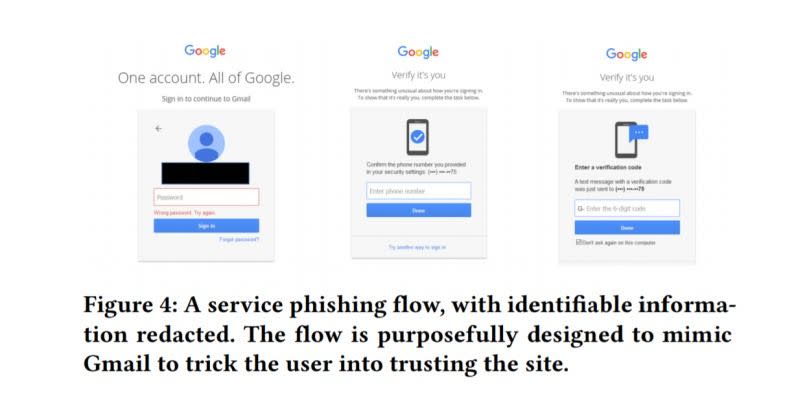
According to the Google data, "hack for hire" attacks that impersonate familiar people or Google itself are incredibly rare, but can include multiple attempts even after an initial message is rebuffed. That's where steps like its Advanced Protection Program -- that requires a user to setup two hardware keys and use one of them to login all the time -- come in handy.
Mirroring the results Google has seen since requiring employees to use hardware keys, researchers said zero users who exclusively use security keys -- despite the presence of a flaw that's caused a recall of Google's Bluetooth Titan Key -- had fallen victim to targeted phishing. Limiting the attack surface based on physical proximity, and because a site has to verify itself to the security key, keeps phishing attacks at bay, even for people who are being targeted specifically.