authentication
Latest

US carriers testing replacement for two-factor authentication
Major US cell phone carriers are working on a mobile authentication system that could create a new open standard. Under the banner of the Mobile Authentication Taskforce, AT&T, Sprint, T-Mobile and Verizon say they have a solution which could roll out before the end of the year: next-generation, multi-factor mobile authentication (hopefully they'll come up with a snappier name for it before launch), which is intended to provide better security than the two-factor authentication we've become accustomed to (and which is not without its flaws).
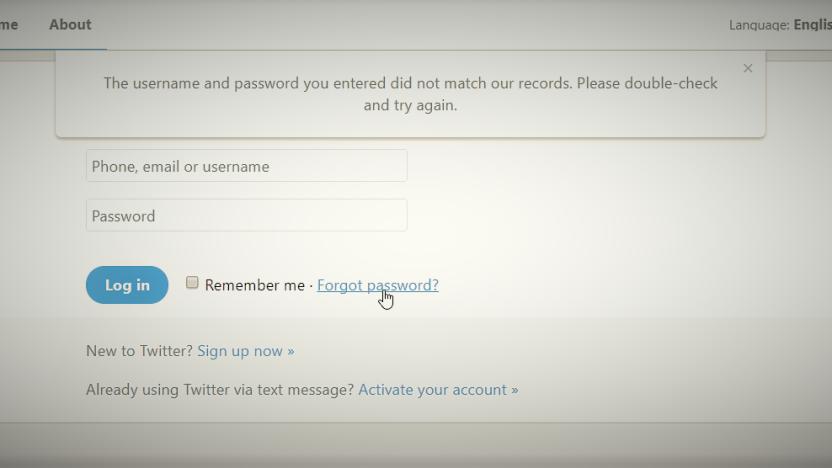
Hawaii governor couldn't log in to Twitter after false missile alert
For most of us, forgetting a password means spending five minutes messing around with authentication emails and reset links. It's annoying, but it's not the end of the world. It was a different story for Hawaii governor David Ige earlier this month, though. After an employee at the state's Emergency Management Agency accidentally sent out a mass text warning of a "BALLISTIC MISSILE THREAT", it took Ige 17 minutes to send out a reassuring tweet -- because he couldn't log in to Twitter.

eBay will now verify luxury handbags sold on the site
eBay is now offering a new service for sellers of high-end handbags. Today the company launched eBay Authenticate, a program that photographs, lists, sells, ships and verifies the authenticity of luxury handbags from 12 major brands. eBay says the goal is to provide would-be buyers with more confidence in the items they're about to throw down a lot of money for.
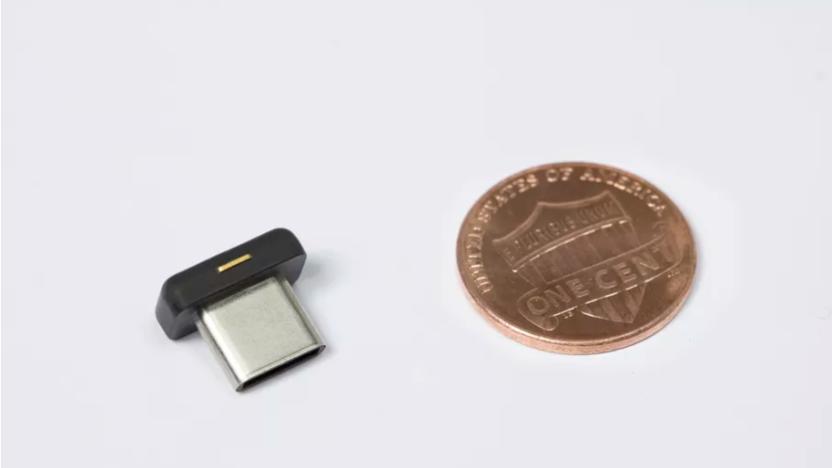
Get ready to lose the tiniest USB-C authentication key in the world
Yubico has launched a new USB-C authentication key and it is tiny. The tiniest in the world, in fact. But size doesn't matter in this instance, as the YubiKey 4C Nano it works just like any other USB-C authentication key. Designed to replace text messages or external authenticator apps when using two-factor authentication, just insert the key into your PC and bingo, you've got access. Interestingly, though, the company claims its incredibly small size makes it well-suited to simply being left in your laptop, which kind of defies its security and protection purpose. Of course, the alternative is taking it out and -- for something of this size -- inevitably losing it.
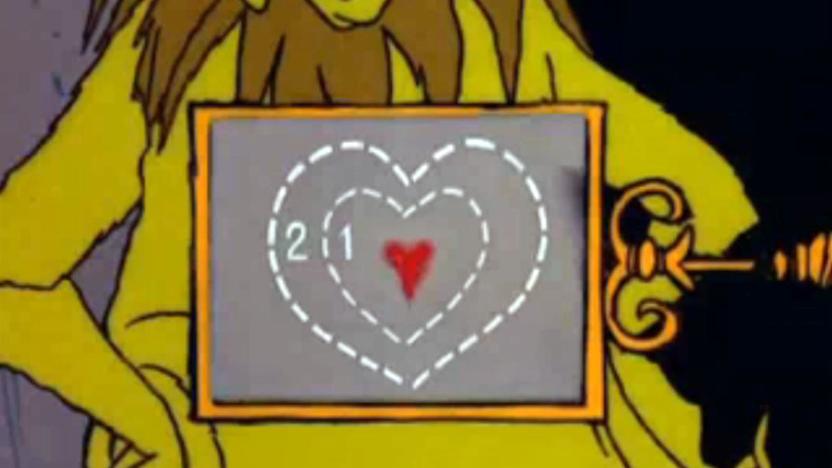
Researchers can use the size of your heart to unlock a PC
Most biometric security has one inconvenience: you have to take an active step to sign in, whether it's putting your finger on a pad or staring at sensors. Wouldn't it be nice if simply being near your device was enough? It might happen. Researchers have created a computer authentication system that uses your heart's shape and size to sign in. It uses low-level Doppler radar to continuously scan your heart's dimensions, granting access so long as you're in the right place. In other words, Cindy-Lou Who couldn't hijack the Grinch's PC when he steps away for a coffee break.

Nintendo rolls out two-step authentication for online accounts
Nintendo now supports two-factor verification to its Nintendo Accounts. This adds another layer of security by requiring codes generated from the Google Authenticator app, though it comes years later than most other gaming platforms.
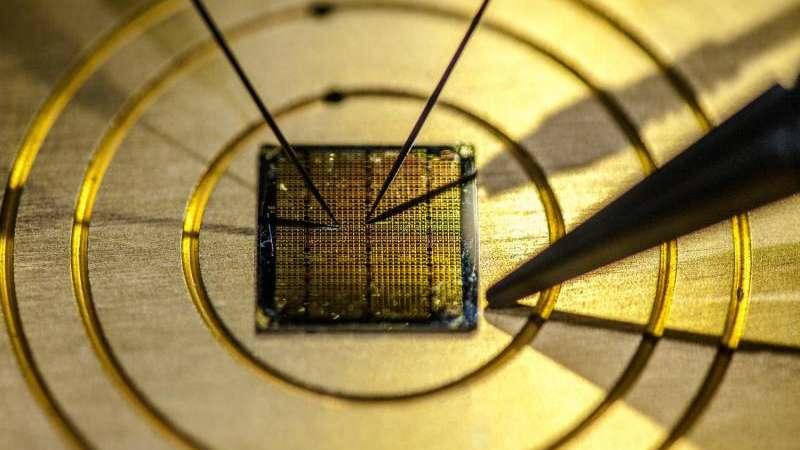
Researchers use quantum physics for counterfeit detection
Scientists from Lancaster University have developed a foolproof anti-counterfeiting measure using a combination of quantum physics and smartphone technology. Previously, the team created unique atomic-scale IDs based on irregularities found in 2D materials such a graphene -- irregularities which, unlike current anti-counterfeiting technology such as holograms, are impossible to clone. Quantum physics amplifies these irregularities and, once turned into a tag, makes it possible to "fingerprint" objects.

A biometric ring could replace your passwords, cards and keys
Smart rings aren't a novel idea: There are plenty of fitness tracking, notification-sending, payment or even protective finger ornaments around. But none have the ability to identify you and authorize your transactions wherever you go. That is, until Token hits the market. It's a biometric ring that can be used to open house doors, start cars, make credit card transactions and sign in to your computer. That all sounds nifty in theory, but without any real cooperation from the third parties that enable those authorizations, Token is all but useless. The good news is that its makers managed to get support from an impressive list of partners including MasterCard, Microsoft, Visa and HID.

Airbnb fights off account hijackers with new security tools
If you get hacked on Airbnb, you won't only have to worry about criminals getting ahold of your credit card details. You'll also have to fret about internet scammers knowing exactly where you're staying on a particular date or the addresses of the properties you own. In a blog post, the company has announced that it has added new security measures to protect your account from hijackers. Starting today, you'll have to authenticate every new phone, tablet or computer you log into by typing in the unique code Airbnb sends you via text or email. It's no two-factor authentication, but it can at least lessen the chances of a rando getting into your account.

US government agency calls for the end of SMS authentication
The US agency that sets guidelines and rules in cryptography and security matters is discouraging the use of text messaging in two-factor authentication. In the latest draft of its Digital Authentication Guideline, the National Institute of Standards and Technology (NIST) states that "[out of band authentication] using SMS is deprecated, and will no longer be allowed in future releases of this guidance." Out of band authentication means utilising a second device to verify your identity.

Google Authenticator takes security codes from your smartwatch
It can be annoying to set up two-factor authentication and boost the security of your accounts, but Google may have found a way to ease your pain. It's delivering an update to Authenticator for Android that not only touts a "refreshed" design, but receives codes from Android Wear smartwatches. You're no longer stuck using this solely on your phone. To top things off, Google is rolling in early support (sadly, developer-only) for the FIDO Alliance's NFC Security keys -- in the future, you may only need to tap devices together to sign in. If you can't bear the thought of logging in with a regular password, you'll want to grab this upgrade in short order.

Twitch rolls out two-factor to reduce profile hijinks
Twitch announced today that it is implementing optional two-factor authentication on its user profiles. The increased security measures, while "100 percent voluntary" according to the streaming site's release, are meant to improve user experiences while reducing the need for conventional, easily hackable passwords.

Lock down your Dropbox account with a USB security key
If you're so concerned about the security of your Dropbox account that even two-factor authentication through your phone seems too risky, you can rest easy. The cloud storage outfit has added support for USB keys as part of the two-factor sign-in process. Rather than punch in a code, you just plug in a stick to prove that it's really you. You'll need a key that meets FIDO's Universal 2nd Factor standard, but this key will also work with Google and any other U2F-capable service. Frankly, this is a long-due upgrade -- if you regularly access Dropbox from PCs, you won't have to worry quite so much that someone will get your login details and swipe your files.

The NSA wants to identify phone users by their finger swipes
For the National Security Agency, the fingerprint reader on your smartphone just isn't secure enough. Lockheed Martin has confirmed to Nextgov that the intelligence outfit is testing Mandrake, an identification system that verifies who you are based on the way you swipe your finger across the screen. The technology measures not only the shape of your movements, but the acceleration and speed. It can tell whether you draw in broad, fast strokes or tend to be cautious. Lockheed doesn't know whether or not the NSA is deploying Mandrake in the field, but it wouldn't be shocking. Given that it's possible to fake fingerprints, gesture-based authentication may the best way of proving that the right person really is present.

Windows 10 log-in options will include fingerprint, facial and iris recognition
Microsoft thinks it's high time you ditch your passwords. The company, which is readying Windows 10 for release later this year, just announced that its next-gen OS will include built-in support for several alternative log-in options, including fingerprint, facial and iris recognition. That means so long as a Win 10 machine has at least one of the necessary sensors -- a fingerprint reader, eye scanner or illuminated IR sensor for facial recognition -- there will be a built-in framework called "Hello" that helps users enroll their fingerprints, or face, or what have you. In other words, then, regardless of who made your machine (Acer, HP, et cetera), you'll get a consistent user experience for setting up a biometric log-in.

Apple's two-factor authentication still leaves some of your data exposed
Apple took a big step forward when it expanded the scope of its two-step authentication last year, since it's now relatively hard to peek at someone's sensitive content unless you also have their device. However, this extra security measure still isn't the all-encompassing safety net you might expect it to be. Need proof? Just ask Dani Grant: she recently gave a friendly reminder that two-factor doesn't even enter the picture with a number of Apple's services. You only need an Apple ID's email address and password to get into FaceTime, iMessage, iTunes and the company's website. You'll need verification if you change account details, sign in to iCloud or try to buy an app, but that basic login is enough to see people's contact information, view their app download history or impersonate them on iMessage. You don't always get email alerts (they typically appear when signing into FaceTime, iCloud or iMessage for the first time on a new device), so it's possible for someone to misuse your account without your knowledge.

You only need a camera (and luck) to copy someone's fingerprints
Forget having to lift smudges from a touchscreen to copy someone's fingerprints. According to a Chaos Computer Club presentation, you only need a camera... well, that and a little luck. The hacking association's Jan Krissler recently demonstrated that you can reproduce someone's fingerprint by getting a few good photos of their hand and processing it through off-the-shelf authentication software like VeriFinger. In Kessler's case, he got the German Defense Minister's thumbprint through photos from a press conference.

Tech industry completes its standards for banishing passwords
Hate typing passwords? You might not have to enter them for much longer. The FIDO Alliance (backed by Google, Microsoft, PayPal and Samsung, among others) has just published the completed versions of its password-free standards for both regular and two-factor authentication. Apps and websites using the technology can now rely on a number of easier and typically more secure ways to sign you in, such as fingerprint readers and USB dongles, without having to worry about the exact device you're using. There are already some hardware and software solutions that play nicely with FIDO, but the existence of firm specs should significantly boost your choices in 2015.

Google now lets you prove your identity with a USB security key
It shouldn't surprise you that Google's a big proponent of online security, and that's why it's rolling out support for a new way to prove you are you who are: a USB Security Key. Google's normal approach to two-step authorization involves getting a text on your phone to verify your identity, but that isn't always ideal. Maybe you suck at keeping your phone charged. Or maybe you're abroad (your author's had to deal with that particular headache a few times) and don't want to get slammed with roaming charges. Having a dedicated secure USB key around means you'll be able to log into Google's ecosystem without having to worry about phishing or having your phone handy.

Japanese carrier Docomo wants to move your phone's SIM card into a wearable
The Portable SIM, as Japan's Docomo is calling it, will combine your tiny mobile card with Bluetooth and NFC to make a standalone authentication device, allowing users to 'wave' the portable over tablets and smartphones to connect and login to phone networks, transferring information, like phone numbers and login details and opening up the possibility of multiple devices with a single SIM card. (Android and iOS, all at once!) It will even store multiple online logins for shopping sites and social networks, according to the Japan's largest phone carrier. The current prototype is around the size of a WiFi hotspot, although Docomo plans to shrink the tech down to a size that would fit into a wearable device, likely to be around the size of current wearables like Acer's Leap band we've used in the mock-up above.










