spy
Latest

Hacking game 'TouchTone' turned me into an NSA spy, and I liked it
I didn't think I'd make for a good NSA agent until I played TouchTone. The iOS puzzle game had me looking for enemies of the state by scouring text messages and emails, and it didn't faze me one bit. It's absolutely unlike how I am in real life. I'm not a voyeur in any sense of the word, nor am I nosy. To this day, if my dad asks me to grab his debit card, I just bring him his wallet because I'd rather not snoop through people's stuff. The allure of invading someone's privacy isn't my bag whatsoever. And frankly, how quickly that all fell away once I started TouchTone shocked me.
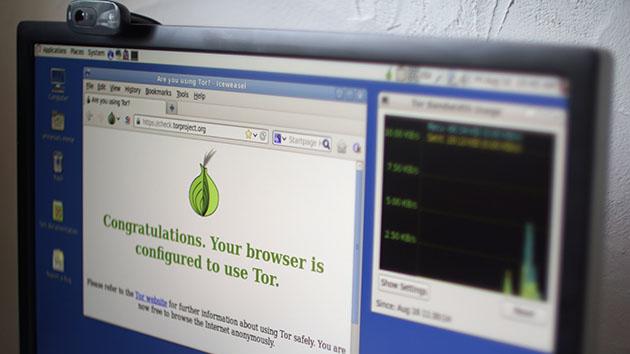
NSA and GCHQ employees may be undermining the agencies' work to hack Tor
It's no secret that US and British spy agencies are trying to crack the Tor network, but new information suggests that the agencies' floundering efforts may be sabotaged from within. For the uninitiated, Tor is a web browser that anonymizes a person's identity, location and browsing activity using various technologies -- it's also a known gateway to the so-called "dark-web" that hosts sites like the Silk Road. Naturally, spy organizations see it as a threat, but the Tor Project's Andrew Lewman says some of the agencies' employees are undermining their own hacking efforts. "There are plenty of people in both organizations who can anonymously leak data to us and say, maybe you should look ere, maybe you should fix this," he told the BBC in a recent interview. "And they have."

UK spies using foreign loopholes to monitor Google, Facebook and Twitter users
GCHQ, the UK's intelligence agency, has yet to confirm whether it taps undersea network cables to gather content from ISPs, but we now know how it would justify access if it did. Charles Farr, the Director General of the Office for Security and Counter Terrorism, revealed that spies could intercept British users' Google searches, Facebook updates and Twitter posts when servers are located outside of the country. The information came to light after Privacy International, Liberty, Amnesty International and a number of civil liberties organizations issued a legal challenge against GCHQ in an attempt to unravel the secrets of agency's Tempora data-tapping program, which were revealed as part of Edward Snowden's NSA document leaks.

US officials reportedly duped into friending Iranian spies on social networks
A fair few government officials will be poring over their personal LinkedIn, Facebook and Twitter accounts today, following a warning about an elaborate hacking campaign that appears to stem from Iran. According to iSIGHT Partners, Iranian hackers have spent the last three years creating a fake news outlet -- Newsonair.org -- and then posing as journalists to give the website an air of credibility (even though all its content was simply plagiarized from elsewhere on the web). Over time, these impostors are alleged to have linked, friended and followed US military, diplomatic and congressional personnel who were attracted to Newsonair's stories. Once a basic connection had been established via a social network, the cyber-spy would then share another interesting-looking story with their target, but this time the shared link would be a so-called spear-phishing site designed to steal login credentials.

Edward Snowden wants you to call him what he is: a trained government spy
Edward Snowden has been called a variety of things: whistleblower, patriot, traitor. But when it comes to his technical expertise, he's usually just referred to as a hacker, contractor or some flavor of system administrator. That, Snowden says, doesn't do his role and background justice. In an excerpt of an NBC interview, Snowden asserts that he's a technical expert "trained as a spy in sort of the traditional sense of the word," worked undercover and overseas for the CIA and NSA, lectured at a counterintelligence training academy and implemented systems for the government "at all levels." According to the infamous whistleblower, he qualifies as a spy in the classic sense since he "lived and worked undercover overseas -- pretending to work in a job that I'm not -- and even being assigned a name that was not mine."

NSA review group tells Obama to ditch bulk phone surveillance
2013 has been a hard year for the White House. It's been working overtime to try and manage the PR nightmare sparked by Edward Snowden's NSA whistleblowing -- fighting the outcry of angry citizens, CEOs and major tech firms. President Barack Obama eventually created a panel to review the government's surveillance programs and propose changes that will help restore public's trust. Today, the group's recommendations are in, and in summary, they aren't too surprising: don't spy on your citizens.The report's most public facing suggestion mandates ending the NSA's habit of collecting US phone call metadata. The agency would still be allowed to collect some records, of course, but the panel suggests that this data be maintained by a private third party, or the phone companies themselves. More importantly, this data would only be accessible with an order from the Foreign Intelligence Surveillance Court. That's hardly the panel's only critique, either: the 308 page document actually makes a total of 46 recommendations. It suggests putting international spy operations under heavier scrutiny, for instance, and says that decisions to monitor such communications need to be made by the Commander in Chief -- not the nation's intelligence agencies. It even suggests major tweak to the NSA's structure, asking the president to consider making the next Director of the NSA a civilian.

The Think Tank: Do government spies scare you away from your favorite MMO?
The NSA is listening to our MMO chat logs, and I feel fine. Monday's news has sparked outrage among some gamers, while others yawn and carry on, knowing that they have nothing to fear. So I polled the Massively staff members to gather everyone's thoughts on the topic. Would any of us stop playing our MMOs of choice, knowing that there are government spies all around watching our every move? Or does that just mean more noobs to bash in PvP?

American and British spy agencies targeted Tor network with minimal success
Considering the NSA and Government Communications Headquarters (GCHQ) have been trying to thwart encryption on the internet, it comes as no surprise that the two have spent significant resources trying to crack the Tor network. Tor, as some of you may know, is designed to keep a person's identity, location and activity anonymous and protect him or her from surveillance. Before panic sets in, know that Tor remains largely secure -- the agencies had only limited success in trying to identify users. One of the documents leaked by Edward Snowden, titled "Tor Stinks" reveals the proof-of-concept attack, but concedes that the NSA "will never be able to de-anonymize all Tor users all the time... With manual analysis we can de-anonymize a very small fraction of Tor users." That bodes well for the journalists and political dissidents who rely on the software, which ironically received the majority of its funding from the State Department and Department of Defense.

American and British spy agencies can thwart internet security and encryption
As reporters at the New York Times, the Guardian and ProPublica dig deeper into the documents leaked by Edward Snowden, new and disturbing revelations continue to be made. Two programs, dubbed Bullrun (NSA) and Edgehill (GCHQ), have just come to light, that focus on circumventing or breaking the security and encryption tools used across the internet. The effort dwarfs the $20 million Prism program that simply gobbled up data. Under the auspices of "Sigint (signals intelligence) enabling" in a recent budget request, the NSA was allocated roughly $255 million dollars this year alone to fund its anti-encryption program. The agencies' efforts are multi-tiered, and start with a strong cracking tool. Not much detail about the methods or software are known, but a leaked memo indicates that the NSA successfully unlocked "vast amounts" of data in 2010. By then it was already collecting massive quantities of data from taps on internet pipelines, but much of it was safely protected by industry standard encryption protocols. Once that wall fell, what was once simply a torrent of scrambled ones and zeros, became a font of "exploitable" information. HTTPS, VoIP and SSL are all confirmed to have been compromised through Bullrun, though, it appears that some solutions to the NSA's "problem" are less elegant than others. In some cases a super computer and simple brute force are necessary to peel back the layers of encryption.

Storyboard: Profession discussion - the Spy
Long-time readers will remember that back around the end of this column's first year, I wrote a series of columns about character archetypes. It was a series I'm quite proud of as a whole, and one that I've wanted to follow up for a while, but I had to wait until I had an idea that fit. That was when I started thinking about how that series talked entirely about who a character is rather than what he or she actually does. In reality, the two can be miles apart. Take my first choice of profession, the spy. A spy might believe that she's doing something for the greater good. She might see this simply as part of her duty and a necessary task. She might be doing this because she's fundamentally amoral, she might be hoping to find the answer to a puzzle she's long agonized about, or she might even be doing this because she just really wants to know secrets. But today I'm not going to talk about that. You want to make a spy; let's talk about what goes into that.

Huawei complains about US spying allegations, implies McCarthy-style victimization
"We must remember always that accusation is not proof." So begins a report sponsored and published by Huawei, heavily quoting a 1954 US Senate report that condemned McCarthy and his anti-Communist hysteria. The document is a prelude to Huawei's forthcoming public testimony to the U.S. House of Representatives' Intelligence Committee, and its message is clear: the Chinese manufacturer is tired of how it's being treated in America, where numerous telecoms contracts have been blocked over "national security concerns." Huawei wants to be seen as an "opportunity" rather than a "threat," claiming it has scope to expand its 140,000 workforce and would love to create more jobs in America -- if only the US government would remove its "roadblock." Many other arguments are put forward, but some of the most interesting paragraphs deal with the background of Huawei's founder, Ren Zhengfei. The document claims that Zhengfei has been "tragically misunderstood" and that his alleged roles in the People's Liberation Army and Chinese Communist Party (CCP) are "unsubstantiated." The report doesn't deny those memberships ever existed, but instead downplays their significance -- for example by insisting that the CCP is now focused on promoting "private entrepreneurs" and "democratization." We admittedly stopped reading at that point, but if you'd like to continue then the full 78-page PDF, written by Dan Steinbock of the India, China and America Institute, is linked below.

Huawei working with British spy service to prove its 'kit' is clean
Since Huawei's president formerly served as a senior engineer in the People's Liberation Army of China, it's unsurprising that it's raised the hackles of the US and other countries. It's been blocked from a variety of prime, security-sensitive contracts on suspicion of espionage, but the Chinese company seems bent on proving its honorable intentions, and has opened a "Cyber Security Evaluation Center" in Banbury, UK to do exactly that. According to the Economist, the company will work closely with GCHQ, the British signals-intelligence agency located in nearby Cheltenham, to persuade the UK and other governments that its equipment is trustworthy. It even has security-cleared staff, including some from the British agency, to shake down the gear and ensure it can't be exploited by spooks or crooks. Huawei already has hefty backbone contracts in Canada and New Zealand and is becoming one of the world's largest suppliers of telecom infrastructure, on top of its high ranking as a handset maker. It might hope this new approach will let it break its US and UK market logjam -- but it has a lot of pent-up distrust to overcome.

Former NSA official says agency collects Americans' web data, director denies charges
The NSA director, General Keith Alexander, is coming under scrutiny after he told a crowd gathered at the Def Con hacker conference that the spy agency "absolutely" does not collect data from and maintain files on American citizens. A former official stopped just shy of calling Alexander a liar, accusing him of playing a "word game." William Binney left the department in late 2001, when it became apparent to him that it planned to use the terrorist attacks on September 11th as an "excuse" to launch a data collection program that was already in the planning stages. Alexander for his part maintains that any data, be it web searches, Twitter posts or emails, collected from American citizens is merely incidental, and associated with intelligence gathering on foreign entities. Of course, Binney rejects this claim and testimony from Qwest CEO James Nacchio regarding the NSA's wiretapping program would seem to contradict it. ACLU attorney Alex Abdo, who was on the panel with Alexander, cast further doubt on the director's denial. He noted that loopholes in the law allow the NSA collect vast amounts of information on Americans, without them being the "target" of the surveillance. Since the agency can hold on to any data collected, it can retroactively build dossiers on citizens, should they eventually become the focus of an investigation. For a few more details, hit up the source link.

CIA dragonfly drone almost beat modern UAVs by 40 years, was swatted (video)
US intelligence agencies were just as obsessed with drone spying 40 years ago as they are nowadays -- only then, it was pipe-smoking entomologists and watchmakers who were in charge of building prototypes. Back in the '70s, the CIA needed some kind of miniature flyer to deliver an audio bug, and after considering (and rejecting) a faux bumblebee, decided that a robotic dragonfly would be the best option. The wee UAV used a "miniature fluidic oscillator" as a motor and was propelled by a small amount of gas. It was somehow guided by a laser beam, which served double-duty as the "datalink for the audio sensor payload," according to the CIA Museum. Unfortunately, the insect-based mech proved too difficult to control, especially with any degree of wind, and was eventually scuppered -- all that's left of the now-declassified project is in the video after the break.

X-37B finally touches down, completing its not-so-secret classified mission (video)
After more than a year of circling the globe, the US Air Force's X-37B has finally touched down at Vandenberg Air Force Base in California. The unmanned, reusable space plane spent 469 days in orbit, performing a number of experiments (many of which are classified) before finally ending its lengthy run Saturday. What exactly the military has learned from the extended orbital excursion is unclear, but, like the Mars rovers before it, the X-37B turned out to be far more robust than many had anticipated. Its mission was originally intended to last just nine months, but its operators managed to milk about six more months out of the craft. While we wait to find out what the next step is, enjoy the video of it landing after the break.

NASA gets two 'Hubble-class' military telescopes, fist-pumps with joy
Imagine all you wanted for Christmas was a telescope. As you frantically peel off layer after layer of wrapping, there it is -- your brother's old one. Well, okay, if your brother was the National Reconnaissance Office (and you were NASA) this might not seem quite as unjust. Thankfully so, as that's effectively what's just happened. The NRO has given NASA two 2.4-meter "space qualified" telescopes and satellite casings for it to play with. The gifts -- which can observe about 100 times the area of the Hubble telescope -- could complement existing projects and provide much-needed resources at the space agency. As there is currently no funded mission for them, however, they'll remain firmly on the ground for now, but at least this implies they're not needed elsewhere -- hinting at improved international relations. Unless the NRO just got an upgrade?

Army spy blimp to launch within weeks: 300 feet long, $500 million, 'multi-intelligent'
It can't go faster than 34MPH and it's already a year late for its planned deployment in Afghanistan, but Northrop Grumman's Long Endurance Multi-Intelligence Vehicle (LEMV) is now set for its maiden flight. The test run is scheduled for sometime between June 6th and 10th over Lakehurst, New Jersey, whose residents ought to be forewarned that it is not a solar eclipse or a Death Star, but simply a helium-filled pilotless reconnaissance and communications airship that happens to be the size of a football field. After floating around for a while, the giant dirigible is expected to journey south to Florida, where it'll be fitted to a custom-built gondola that will carry the bulk of its equipment, and by which time her enemies hopefully won't have come into possession of an air force.

Happy Biiiirthday Mr. USAF X-37B Robot Space Plane
The X-37B was only meant to stay up in space for a gestational nine months, but a full year has now passed since launch and the US Air Force apparently has little interest in bringing its baby home. On the contrary: according to Space.com, the plan is to send up another unmanned space plane to keep the X-37B company on its [CLASSIFIED] missions. Whatever it's getting up to in that airless playground, it must be doing something right. Air Force Lt. Col. Tom McIntyre says the craft is "setting the standard for a reusable space plane and, on this one-year orbital milestone, has returned great value on the experimental investment." Which is a fine way of saying [STILL CLASSIFIED].

BMW i8 production prototype goes dancing in a winter wonderland (video)
It's been almost a year since we last wrote about the BMW i8 being winter-tested and here it is again -- this time in production prototype form -- doing donuts (!) in the snow. This plug-in gasoline electric hybrid vehicle started life as the Vision EfficientDynamics, promising sub five-second 0 - 60mph times while still achieving an impressive 87mpg (2.7 liters per 100km). We last saw the i8 concept at the Frankfurt Motor Show but the sporty coupé with the funky gullwing-like doors isn't expected in BMW showrooms until sometime in 2014. So for now just sit back, relax and check out the video above.

Wi-Spi Helicopter and Intruder RC toys put the childlike wonder back into spying on your neighbors
Sick and tired of spying on the neighbors the old-fashioned way? Good news, all. Interactive Toy Designs showed off two new products in its not-so-subtly named Wi-Spi line of remote control vehicles. Really driving the notion home is the Intruder, the name given to the little red sports car. The helicopter, on the other hand, is called just that, though we're sure you can intrude upon people with the thing, if you really put your mind to it. Both vehicles have built-in cameras that beam live feeds to your iPhone or Android devices. You can also record the video and upload it instantly to social networking sites, to really get that spying 2.0 feel. The Intruder and Helicopter are both arriving in the fall, for $100 and $120, respectively. Edgar Alvarez contributed to this report.











