Amazon AWS error exposes info on 31,000 GoDaddy servers
Server configurations and Amazon Web Services pricing were included.
Data leaks are par for the course these days, and the latest company to be involved in one is GoDaddy. The company, which says it's the world's top domain name registrar with over 18 million customers, is the subject of a new report from cybersecurity firm UpGuard that was shared exclusively with Engadget. In June, cyber risk analyst Chris Vickery discovered files containing detailed server information stored in an unsecured S3 bucket -- a cloud storage service from Amazon Web Services. A look into the files revealed multiple versions of data for over 31,000 GoDaddy systems.
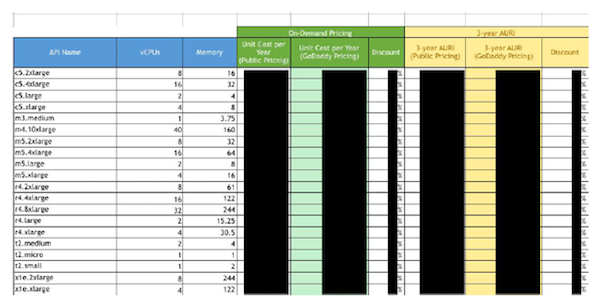
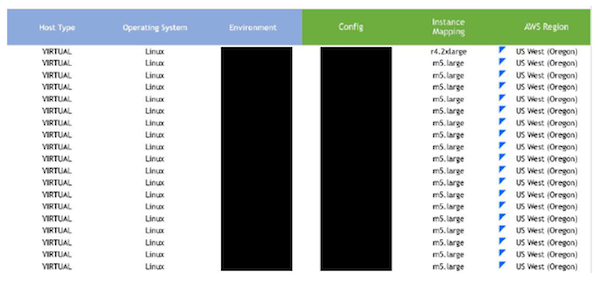
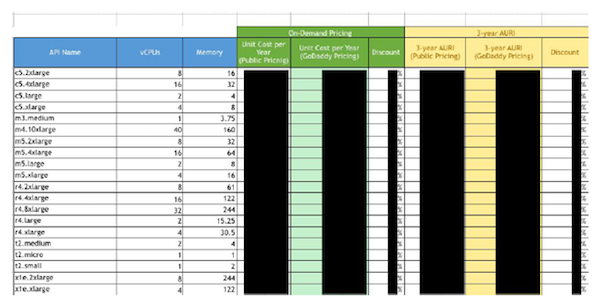
In the most recent revision of the exposed spreadsheet, there were eight tabs with information on GoDaddy's AWS usage as well as pricing and discounts the company was offered by Amazon. It also contained server configuration information including memory and CPU specifications, hostnames, operating systems and server workloads. "Essentially, this data mapped a very large scale AWS cloud infrastructure deployment," UpGuard notes, which could give competitors a look into GoDaddy's business practices and more malicious actors a better strategy for attack.

UpGuard notified GoDaddy of the discovery shortly after uncovering the exposed storage bucket, but GoDaddy didn't secure the information for over five weeks. In that time, when checking up on the progress of his report, Vickery was told that it's typical for there to be a delay following security reports such as this one. GoDaddy didn't respond to inquiries as to whether five weeks was a standard amount of time between an initial report and taking action.
While AWS S3 buckets are private by default, permissions can be altered to give others access. In some cases when sensitive data is found exposed on an S3 bucket, the AWS customer is to blame. But in this instance, it appears that Amazon itself was the cause of the exposure. "The bucket in question was created by an AWS salesperson to store prospective AWS pricing scenarios while working with a customer," an AWS spokesperson told Engadget. "No GoDaddy customer information was in the bucket that was exposed. While Amazon S3 is secure by default and bucket access is locked down to just the account owner and root administrator under default configurations, the salesperson did not follow AWS best practices with this particular bucket."
"As for the documents that were exposed, they were speculative models from an AWS employee and do not reflect work currently underway with Amazon," GoDaddy told Engadget.

While there wasn't any end-user personally identifiable information included in the spreadsheets, there are two major risks brought on by the exposure. The first has to do with GoDaddy as a business. Because the spreadsheet listed both pricing and usage information -- like how much storage GoDaddy predicts it might need and where it might get it -- it offers a window into GoDaddy's practices, finances and strategies. "Anybody that is in the same industry as GoDaddy, anybody that's a competitor, would love to see this kind of stuff," said Vickery. The pricing could be of particular interest to competitors who could, in theory, use it to leverage their own deals with Amazon.
But beyond battling in the marketplace, in the hands of a malicious actor, this information could be used to strategize an attack. The info was detailed enough to provide a roadmap for what hackers would want to "either poke, exploit or ignore," Vickery said. "And if you know what of 31,000 servers is interesting, and what's not, that speeds up an attack plan." UpGuard notes that the workload column might be especially useful, pointing hackers towards the systems that have more important functions and might host desirable data. "One could arguably say that GoDaddy hosts a fifth of the internet," UpGuard says in its report. And a successful attack on its systems could "potentially disrupt global internet traffic."
Neither GoDaddy nor Amazon answered Engadget's question as to whether there was evidence anyone other than UpGuard or Vickery accessed the information.
Over the last couple of years, sensitive data has been left exposed online by defense contractors, voting machine suppliers, the Pentagon, political advertising strategists, a Verizon partner, the US Army and NSA, major management firms and the Cambridge Analytica-connected AggregateIQ. And that's just what UpGuard has found. Dozens of other major companies have also revealed data exposures or hacks during that time, and it all points to a serious global cybersecurity crisis.
So what, if anything, can we do? Vickery, who has seen a lot of this firsthand, has some ideas. He says the first step needs to be admitting that there's an issue. "The cybersecurity and technology industries need to recognize that they have a problem," he said, "and be forthcoming with information about it and be honest with the public and the media about how bad it is."
Vickery also believes the public needs to be better educated on the reality of hacks and data exposures. "Getting the snake oil out of the industry" needs to be a priority he said. Discourse that relies on disingenuous scare tactics is harmful to the public understanding of cybersecurity, he argues, but it has become commonplace nonetheless.
And lastly, while contracts between companies often cover what should happen and who should be liable in the event of a data breach, they should also address security measures up front. Data often becomes exposed when employees or partners use inappropriate accounts or misconfigure security settings. In those cases, the original company would have a hard time keeping track of, or even being aware of, what's happening with their data.
Vickery says those in charge of the legal aspects of a partnership should address where network resources should be stored right in the contract. The idea being "security from the start rather than security as an add-on."
Meanwhile, Congress is starting to pay attention to the issue. Following the massive Equifax breach, which exposed personal information of around 148 million people, Congress did pursue some legislation that would better address what companies should do when faced with a data exposure. But as the Facebook/Cambridge Analytica debacle has continued to shift our collective focus to data privacy issues, it's easy to feel like breaches have slipped by the wayside -- particularly since Equifax seems to have been largely let off the hook.
However, Vickery says data breaches like Equifax's and Uber's haven't been forgotten and at least some members of Congress are still looking to enforce accountability. He said, as far as Congress' interest in security protection goes, "the waters are getting warmer."