Everything we know about the Twitter Bitcoin hack
The investigation is underway, and we're collecting all the updates here.
Author’s note: This story was first published on 7/16/2020, and last updated on 7/17/2020. Check the Latest Updates section for the most recent developments.

What happened?
Early in the afternoon (Eastern time) on July 15th, a hacker -- or hackers -- gained control of a series of Twitter accounts owned by Bitcoin enthusiasts, executives and exchanges. Upon gaining control of those accounts, the hackers tweeted messages to those accounts' audiences claiming that they would be "giving 5000 BTC back to the community" and directing users to cryptoforhealth.com. People who visited the now-defunct website were told that if they sent Bitcoin to a specified address, they would receive double the amount in return, plus a bonus if contributions exceeded a certain threshold.
After the hackers had spread the message from multiple Bitcoin-related Twitter accounts, they went big. The first major account to be breached appears to be Elon Musk's, followed in short order by Bill Gates, Uber, Apple, Kanye West, Jeff Bezos, Mike Bloomberg, Joe Biden and former president Barack Obama, among others.
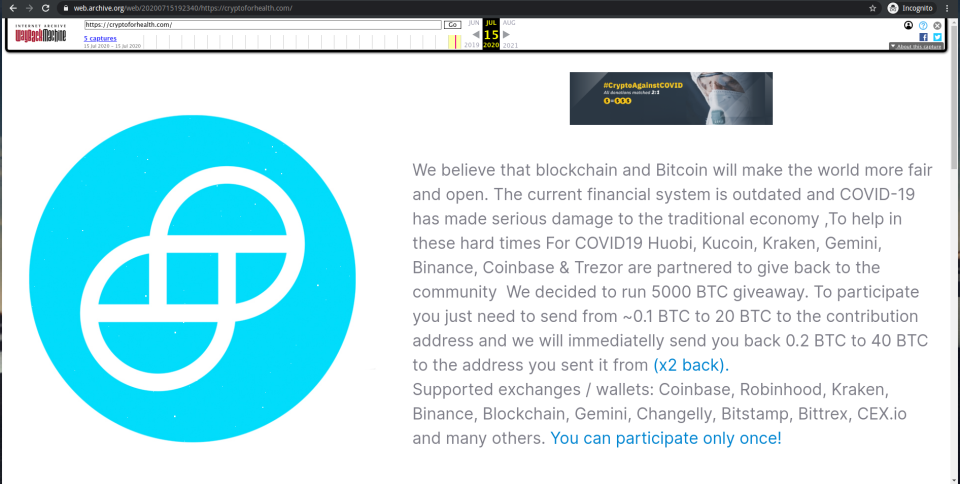
Most of these accounts tweeted some variant of the same message: If someone were to send Bitcoin to the address specified in the tweets during a 30-minute window, the account owner would return double the amount. These outsized claims succeeded in tricking some people into sending over valuable cryptocurrency, but no crypto was ever sent in return. (Obviously.) All of the tweets sent from these high-profile accounts directed victims to the same Bitcoin address.
By this point, Twitter had caught on and was attempting to contain the account breaches. In an effort to prevent more scammy messages being shared, Twitter temporarily removed the ability for verified users to tweet. If the owners of those accounts wanted to communicate on the platform, they either had to create temporary accounts, retweet existing tweets, or both. (Meanwhile, non-verified Twitter users basically had a field day.) Twitter appeared to get the situation under control and restored verified users’ ability to tweet at around 8:30 PM Eastern.
At that time, Twitter confirmed that it had opened an investigation into the hack, and one day later, the FBI confirmed that it was launching an investigation of its own.
We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools.
— Twitter Support (@TwitterSupport) July 16, 2020
How did these accounts get hacked?
At this time, Twitter's investigation is still ongoing, and there is little in the way of conclusive information. With respect to the hack itself, here's what the company has confirmed so far:
Some of its employees were targeted in a social engineering attack because of their access to "internal systems and tools."
The hackers were able to "take control" of verified and high-profile Twitter accounts, and published the scam tweets "on their behalf"
In the wake of the hack, Twitter has taken steps to limit access to the aforementioned internal systems and tools, at least for the duration of the investigation.
The @TwitterSupport account has been largely quiet since issuing those statements, but it's important to note that some news reports published in the wake of the hack stand at odds with Twitter's official narrative.
As mentioned, Twitter said some of its employees fell prey to a social engineering attack. "Social engineering" is a term with many connotations, but is generally taken to mean that one party has tricked or manipulated another to gain information or access to resources that otherwise would have been off-limits. Meanwhile, a report published by Motherboard a few hours after the hack described the situation more bluntly. According to unnamed sources who allegedly took over some of the accounts themselves, hackers bribed at least one Twitter employee for access to powerful platform controls.
Motherboard's interview revealed the existence of a control panel that certain Twitter employees have access to, which allows them to -- among other things -- change the email addresses connected to specific Twitter accounts. By changing information associated with some of those high-profile accounts, the hackers were able to temporarily transfer ownership to themselves. At this point, however, it's unclear whether this method was used to gain control of all the affected accounts. It is worth noting, however, that one of Motherboard's sources claims that a Twitter rep did "all the work" for them, suggesting a level of cooperation that isn't directly addressed in Twitter's statements.
How much did the hackers get away with?
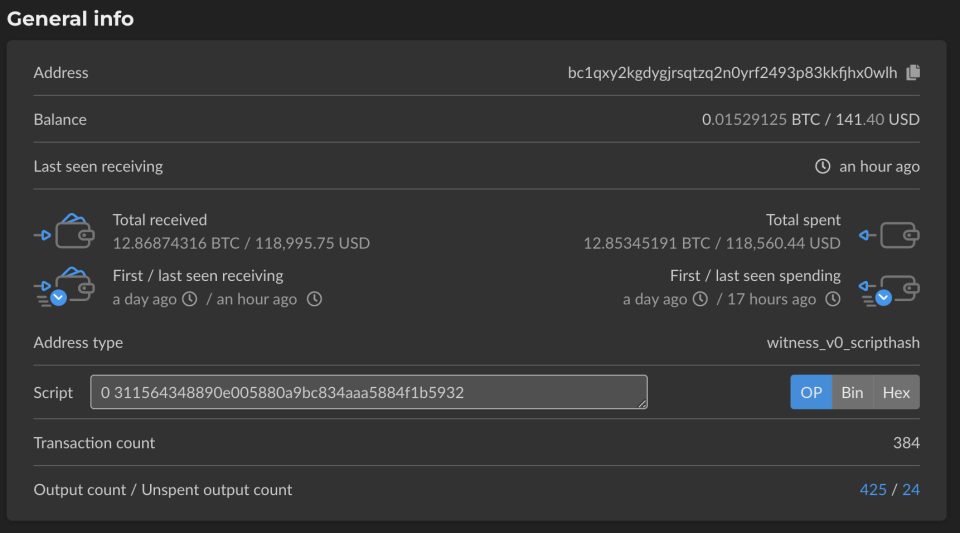
The value of the hackers' final takings aren’t known at the moment. Early on, people monitoring the address specified in those celebrity tweets saw that it was the recipient of nearly $60,000 in Bitcoin transfers. At time of writing, the total amount sent to the address in question stands at 12.86874316 BTC, or $118,995.75. That figure dovetails with an account given to TechCrunch by another unnamed source, who claimed that a hacker known as “Kirk” was behind the hack and generated “over $100,000” in a matter of hours. However, much of the cryptocurrency in the wallet associated with that address is no longer there. As it stands, the wallet currently contains the equivalent of about $141.
What's still unclear is how many of those Bitcoin transfers were initiated by people acting in good faith. In scams like this, it's not uncommon for the perpetrators to "seed" the blockchain ledger with transactions that appear legitimate in an attempt to hoodwink skeptical, would-be donors into sending crypto.
How are lawmakers reacting?
Legislators were, unsurprisingly, appalled. (And then quiet for a little while, after their verified accounts were muted.) While scammy messages were being tweeted, retweeted and scrutinized, Senator Josh Hawley (R-Missouri) drafted a letter to Twitter CEO Jack Dorsey calling for answers to questions about the scope of the breach, the possibility of personal data loss as a result of the breach, and the sorts of protections Twitter has in place to prevent "system-level hacks." Dorsey has not publicly responded to these questions.
Beyond individual members of government, Twitter also faces heightened scrutiny from trade regulators and governing bodies. CNN Business's Brian Fung pointed to the possibility that Twitter would become the subject of a Federal Trade Commission investigation, citing comments from two former directors of the FTC's Bureau of Consumer Protection. Meanwhile, the BBC notes that the European Union will likely take an interest -- despite the fact that the hack's victims were largely American -- because of what the situation says about the company's security practices. If EU regulators find that Twitter was lax in its efforts to protect its users, the social media giant could face a hefty fine.
It was, as CEO Jack Dorsey laconically put it, a “bad day” for Twitter. But the weeks and months that follow may wind up costing the company even more.
Recent updates
7/17/2020: While the Twitter breach culminated in scammy tweets being sent from several celebrity accounts, the scope of the attack was actually much larger. At 10:53 PM Eastern on July 16th, the @TwitterSupport account confirmed that “approximately 130 accounts were targeted by the attackers in some way as part of the incident.” (Read our story here.) Elsewhere that same evening, security researcher Brian Krebs published a detailed report suggesting the foundation of the hack was rooted in a forum known for trafficking in black market social media accounts. (Read our story here.)
7/16/2020: According to The Hill and Financial Times correspondent Kadhim Shubber, the FBI’s San Francisco division has opened an official investigation into the Twitter hack. Meanwhile, on the other side of the country, New York governor Andrew Cuomo is directing his Department of Financial Services “and any other relevant state agency” to investigate the matter. And unlike the FBI, Governor Cuomo admits that his actions are rooted on some level in the need to safeguard the upcoming presidential election. (Read our story here.)
FBI confirms it is investigating the Twitter hacks pic.twitter.com/KHdcVTPiWq
— kadhim (^ー^)ノ (@kadhim) July 16, 2020
7/16/2020: @TwitterSupport added to its investigation thread with some good news at 3:18PM Eastern time. While it has no additional information about the mechanics of the hack, the account notes that there is “no evidence that attackers accessed passwords,” and that the company does not believe changing your password is necessary. (Read our story here.)
Here’s an update addressing questions we’ve heard around passwords and account access specifically:
— Twitter Support (@TwitterSupport) July 16, 2020
7/16/2020: In the immediate aftermath of the hack, one big question still hangs in the air: Were the hackers after more than just money? Some, like digital privacy expert Ray Walsh, told our own Dan Cooper that the hackers were either “highly unimaginative or extremely restrained.” Another theory posits that the hackers were just kind of dumb:
Sometimes hackers come across valuable access they don't know how to properly monetize. Just because they only made $100k from having access to almost every Twitter account doesn't necessarily mean there's a deeper hidden motive. Some hackers just aren't creative.
— MalwareTech (@MalwareTechBlog) July 16, 2020

