security
Latest

WhatsApp is enabling passkey support on iOS
WhatsApp users on iOS will soon have a more secure way to log in. Meta is rolling out passkey support for that version of the app, several months after it did so for Android.

Creepy monitoring service sells searchable Discord user data for as little as $5
A data scraper is selling information on what it claims to be 600 million Discord users. A report from 404 Media details Spy Pet, an online service that gathers, stores and sells troves of information from the social platform.

Roku suffered another data breach, this time affecting 576,000 accounts
Roku has disclosed a second data breach in as many months. The company says that, this time around, 576,000 accounts were compromised.

DuckDuckGo unveils a $10 Privacy Pro plan with a no-log VPN
DuckDuckGo has announced a Privacy Pro service that includes a VPN, personal information removal and identity theft restoration service. The offering is US-only for now and costs $10 per month.

Authorities reportedly ordered Google to reveal the identities of some YouTube videos' viewers
Federal authorities in the US asked Google for the names, addresses, telephone numbers and user activity of the accounts that watched certain YouTube videos between January 1 and 8, 2023, according to unsealed court documents viewed by Forbes.

Apple Silicon has a hardware-level exploit that could leak private data
A team of university security researchers has found a chip-level exploit in Apple Silicon Macs. The group says the flaw can bypass the computer’s encryption and access its security keys, exposing the Mac’s private data to hackers.

The best password manager for 2024
Remembering dozens of passwords can be difficult for anyone. These are the best password managers you can use to keep your information safe and secure.

Glassdoor reportedly attaches real names to anonymous accounts
Users have reported that Glassdoor is adding their names and other information to their profile — despite never consenting.

The US will investigate cars built in China over security concerns
The Biden administration has announced an investigation into cars built in China and other "countries of concern" over potential security risks.

Members of ransomware gang Lockbit arrested by law enforcement
International law enforcement, led by the UK’s National Crime Agency, disrupted ransomware gang Lockbit's operation.

Defense Department alerts over 20,000 employees about email data breach
The Department of Defense sent a data breach notification letter to thousands of current and former employees alerting that their personal information had been leaked, DefenseScoop reported on Tuesday.

HIPAA protects health data privacy, but not in the ways most people think
With misinterpretations of HIPAA starting with just its name, misunderstandings of what the law actually does greatly impact our ability to recognize how the kinds of data do and don't fall under its scope. That’s especially true as a growing number of consumer tech devices and services gather troves of information related to our health.

Ring’s cheapest subscription plan is going up by $10 a year
Amazon's Ring is raising the price of its cheapest Basic subscription, following similar bumps by Google and others.

US officials believe Chinese hackers lurk in critical infrastructure
By lurking behind the scenes of transportation, water, electricity and other important systems, the hackers have the opportunity to strike whenever they deem the time is right, US officials say in a 50-page report on the subject.

How security experts unravel ransomware
Increasingly, security professionals are coming together with law enforcement to provide free decryption tools — freeing locked files and eliminating the temptation for victims to pony up.

Fallout from the Fulton County cyberattack continues, key systems still down
Key systems in Fulton County, Georgia have been offline since last week when a 'cyber incident' hit government systems.
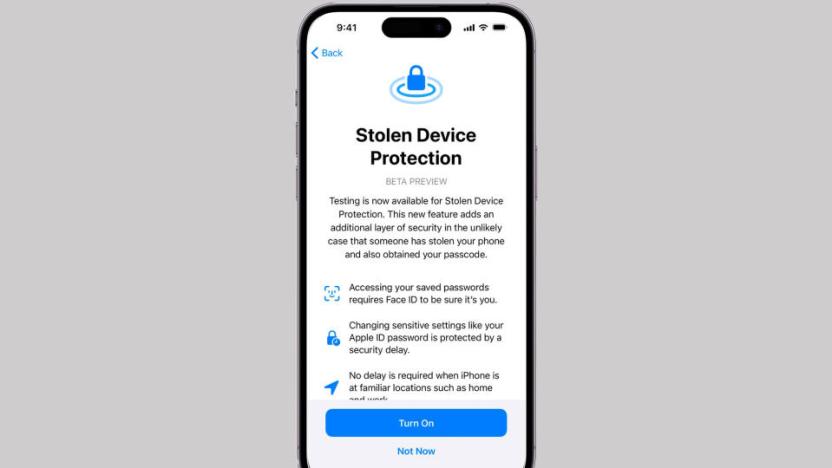
How to turn on Stolen Device Protection on your iPhone to secure your data
Apple’s Stolen Device Protection is a new feature that makes it harder for iPhone thieves to wreak further havoc. The feature requires a combination of biometric scans and time delays before using payment features or changing account security when it's away from familiar locations.

LoanDepot discloses that hackers breached personal data of 16 million customers
As mortgage lender LoanDepot continues recovery efforts from a ransomware attack, it revealed on Monday that hackers stole data from more than 16 million customers.

Carnegie Mellon reveals it was hit by a cyberattack over the summer
The Pittsburgh-based university known for its top tech and computer science programs said on Friday that the attack impacted up to 7,300 students, employees, contractors and other affiliates.

Apparel supplier for North Face, Vans admits its cyberattack led to a data breach of 35 million customers
If you've purchased from its major brands like Vans, North Face, Timberland, Dickies and more, you may have been impacted — but VF Corp still insists that the incident won't impact its financial performance.





