wannacry
Latest

'WannaCry hero' Marcus Hutchins sentenced to supervised release
Marcus Hutchins' efforts to stop the spread of WannaCry malware just helped him avoid prison time. Judge JP Stadtmueller has sentenced Hutchins to a year of supervised release after he pleaded guilty to creating and distributing Kronos banking malware. He was a teen when he committed the offenses, according to the judge, and he was "turning a corner" before he faced charges. Hutchins acknowledged that he'd made "bad decisions" and that he had "no desire" to slip back into a life of online crime.
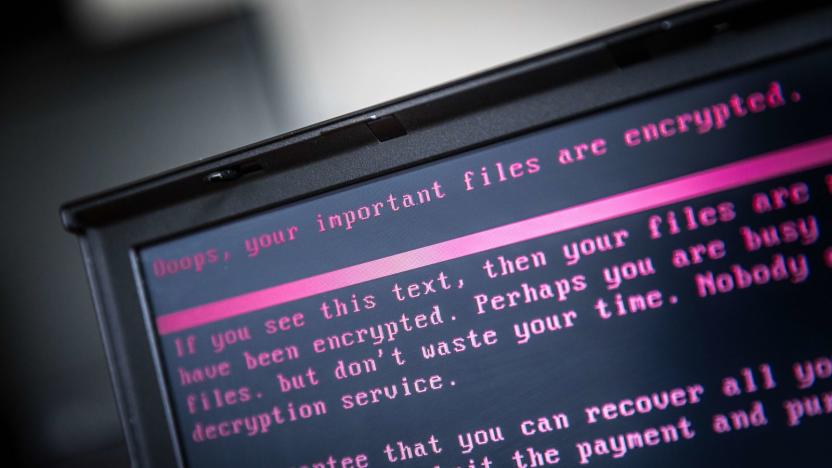
Local governments are still woefully unprepared to fight ransomware
Our state and local governments found themselves under siege in 2019 from William Plunketts for the internet age. But rather than pistols and roadblocks, this new generation of bandits come armed with encryption algorithms and demands for bitcoin. Can today's American cities and counties, long hamstrung by both a lack of interest and funding for cybersecurity efforts ever hope to withstand these digital muggings? Just ask Lake City, Florida.

US recommends Windows users patch against worm vulnerability
Microsoft Windows users who haven't patched their OS (or are using an unsupported version) are at risk of attackers exploiting a vulnerability known as BlueKeep. The Cybersecurity and Infrastructure Security Agency (CISA), Homeland Security's lead cybersecurity agency, said it successfully tested a working exploit for the BlueKeep vulnerability. Specifically, the agency was able to remotely run code on a Windows 2000 computer using BlueKeep, it stated in an advisory. The bug effects computers that are running Windows 7 or earlier (as well as Windows Server 2003 and 2008), and gives potential attackers access through Microsoft's Remote Desktop Services.

Old versions of Windows get a new patch to stop WannaCry-style attacks
Microsoft is trying to head off another WannaCry-style malware outbreak before it starts. The software giant has released fixes for a Remote Desktop Services (aka Terminal Services) vulnerability that could allow "wormable" malware that spreads from computer to computer without requiring any user input. The exploit affects Windows 7, Windows Server 2008 R2 and older releases. Not surprisingly, Microsoft isn't taking any chances. While it's no longer officially supporting Windows XP and Windows Server 2003, it's patching both platforms to prevent ancient PCs (like those used in some business and government scenarios) from falling prey to attacks.

Chinese spies reportedly repurposed NSA tools used to hack their computers (updated)
A group called Shadow Brokers leaked sets of hacking tools back in 2017 that led to massive security breaches around the world, including the infamous WannaCry ransomware attacks. While the group maintained that it stole the tools from the US National Security Agency (NSA), it was a mystery how it got its hands on them. Now, a Symantec report has revealed that prior to the Shadow Brokers leak, NSA tools were captured by the Buckeye, a hacking group that the US government has linked to Chinese intelligence agents. As to how Buckeye got its hands on those tools? It seems they reverse-engineered them after the NSA first used them to attack their computers.

'MalwareTech' security researcher pleads guilty
In 2017, Marcus Hutchins went from being a relatively unknown 23-year-old, to being a worldwide hero, to facing criminal charges all in a span of a few months. After he shut down the rapidly spreading WannaCry malware by finding a killswitch domain in the software, UK tabloids exposed his real name. Then in August of that year, just as he was about to leave Las Vegas after the Defcon event there, US authorities arrested Hutchins, claiming he'd played a part in creating a different type of malware, Kronos, years earlier. Today he pleaded guilty to a pair of charges related to the malware, for which he faces up to ten years in prison. In a statement posted on his personal website, he said: As you may be aware, I've pleaded guilty to two charges related to writing malware in the years prior to my career in security. I regret these actions and accept full responsibility for my mistakes. Having grown up, I've since been using the same skills that I misused several years ago for constructive purposes. I will continue to devote my time to keeping people safe from malware attacks. As described in court documents published by ZDNet, the government's case was that Hutchins developed the malware, known both as UPAS Kit and Kronos, to collect info, while targeting banking information. He worked with partners to distribute and sell the malware to others who made use of the tools. At the time of his arrest, Engadget columnist Violet Blue described the chilling effect this prosecution could have on security research. To get the experience needed to shut down malware that threatened computers worldwide one might follow a career that includes some steps outside the lines, and this may make fighting for legitimacy even tougher.

US charges North Korean man linked to Sony hack and WannaCry
The US Treasury Department announced today that it has sanctioned one individual and one group connected to malicious cyber activities perpetuated by North Korea's government. Park Jin Hyok, a computer programmer, was sanctioned today along with Korea Expo Joint Venture, an agency he allegedly worked for. The Treasury Department claims Hyok is part of a conspiracy responsible for the 2014 Sony Pictures hack, the 2016 Bangladesh Bank heist and last year's WannaCry ransomware attack. The Department of Justice also confirmed to reporters that it has charged Hyok with extortion, wire fraud and hacking crimes, according to Motherboard.

DOJ will reportedly charge North Korean operative for Sony hack
The Justice Department will reportedly announce charges today against at least one North Korean operative connected to the 2014 cyberattack on Sony Pictures, the Washington Post reports. Officials told the publication that computer hacking charges would be brought against Park Jin Hyok, who is said to have worked with North Korea's military intelligence agency the Reconnaissance General Bureau. It's the first time these types of charges have been brought against an operative of North Korea.

TSMC says virus that shut down its plants is a WannaCry variant
Over the weekend, chip manufacturer TSMC reported that some of its fabrication plants had to be shut down because of a virus that had infected the company's systems. While some were able to resume operations quickly, others were out of commission for up to a day. Now, TSMC has blamed a WannaCry variant for the disruption. Bloomberg reports that the company has resumed full operations but shipment delays are expected.

'WannaCry hero' faces more federal malware charges
Marcus Hutchins, the cybersecurity researcher credited with helping stop last year's WannaCry virus, is facing four new charges related to malware he allegedly created to steal financial information. Now, the FBI says Hutchins lied about creating the malware called Kronos, and that he conspired with others to promote it online, including via YouTube.

Boeing: Reports of WannaCry outbreak 'overstated and inaccurate'
This afternoon a report by the Seattle Times cited internal messages showing that aircraft builder Boeing had been hit by the WannaCry ransomware and there were fears it could affect production. Boeing VP Linda Mills tells Engadget in a statement that its network security "detected a limited intrusion of malware that affected a small number of systems," and it shouldn't affect deliveries. Issues with ransomware have not tailed off since last year's worldwide outbreak of WannaCry/NotPetya, and the city of Atlanta's government is still recovering after "SamSam" ransomware locked down some systems last week. Even if this occurrence is as controllable as Boeing believes, it's surely not the last time we'll hear about a large organization suddenly locked out of its own computers.

2017’s biggest cybersecurity facepalms
2017 was a year like no other for cybersecurity. It was the year we found out the horrid truths at Uber and Equifax, and border security took our passwords. A year of WannaCry and Kaspersky, VPNs and blockchains going mainstream, health care hacking, Russian hackers, WikiLeaks playing for Putin's team, and hacking back. In 2017 we learned that cybersecurity is a Lovecraftian game in which you trade sanity for information. Let's review the year that was (and hopefully will never be again).

Facebook and Microsoft disabled slew of North Korean cyber threats
If you ask the White House, North Korea's WannaCry attack was just the tip of the iceberg. Homeland security adviser Tom Bossert reported that Facebook and Microsoft disabled a range of North Korean online threats in the past week. Facebook removed accounts and "stopped the operational execution" of ongoing attacks, while Microsoft patched existing attacks that went beyond WannaCry. Details of just what those attacks were aren't available.

US government names North Korea as the source of WannaCry
Donald Trump's homeland security adviser, Tom Bossert, said in a Wall Street Journal op-ed that "after careful investigation, the U.S. today publicly attributes the massive "WannaCry" cyberattack to North Korea." Coming during increasing tensions between the two countries over nuclear threats and Twitter outbursts, Bossert said this attribution is based on evidence and agrees with the findings from the UK and Microsoft.

'Basic IT security' could have prevented UK NHS WannaCry attack
England's National Health Service (NHS) could have avoided the ransomware hack that crippled its systems in May, according to a government report. "Basic IT security" was all that was required to prevent the "unsophisticated" WannaCry attack, which affected more than a third of NHS organizations, said the National Audit Office (NAO). The full scale of the incident saw over 19,000 medical appointments canceled, and computers at 600 surgeries locked down.
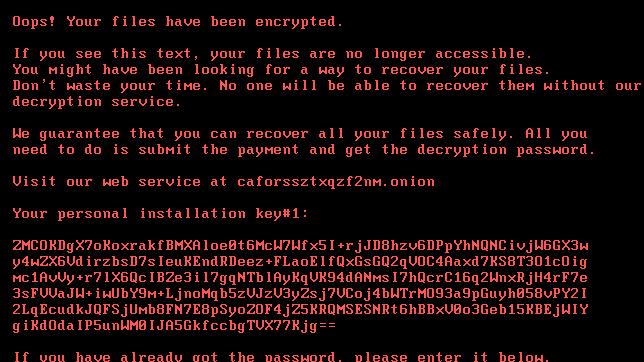
New ransomware is causing major issues across Europe and Russia
There's a new ransomware making the rounds today with confirmed targets in Russia, Ukraine, Turkey and Germany. Kaspersky Labs says that nearly 200 victims have been hit with the ransomware that's been dubbed Bad Rabbit.

FedEx estimates ransomware attack cost $300 million
FedEx acquired Dutch shipper TNT Express last year for $4.8 billion, well before the NotPetya ransomware ran wild on TNT's systems June 27th, disrupting much of its shipping operation. Like the earlier WannaCry outbreak, NotPetya used a Windows exploit stripped from an NSA leak to spread across networks. According to FedEx, even though its services and critical systems have been restored, "TNT Express volume, revenue and profit still remain below previous levels." That adds up to a $300 million hit on its operating results, and the company raised the estimate of integrating TNT's systems with its own by $75 million over previous estimates.

UK cybersecurity researcher pleads not guilty to malware charges
Marcus Hutchins, the British cyber security researcher who won attention for helping to halt the spread of the WannaCry malware program earlier this year, has just entered a plea of not guilty for a set of unrelated charges. Hutchins was arrested by the FBI at the Def Con security conference in Las Vegas and was due for arraignment in a Milwaukee court last Friday. The arraignment was postponed until Monday, August 14th, which is when Hutchins entered his plea.

FBI arrests UK security researcher who stopped WannaCry outbreak (updated)
Marcus Hutchins, the 23-year-old security researcher who is credited with halting the spread of the WannaCry malware program earlier this year has been arrested by the FBI while attending the Def Con security conference in Las Vegas, Motherboard reports.

The only way to stop another WannaCry is with regulations
It's been one week since the newest (and therefore scariest) cyberattack, which caused pandemonium across Ukraine and Russia before spreading to other countries. But that came only a few weeks after the WannaCry ransomware targeted Windows XP machines worldwide, which infamously held data from the UK's National Health Service hostage. You might think we've entered a new era of cyberattacks, one that could threaten all of the machines in your home and every internet-connected service you rely on.










