TL17CRY
Latest

WannaCry ransomware causes Honda plant to shut down
WannaCry isn't done yet. Honda Motor Co. had to shut down its Sayama plant on Monday after finding the ransomware in its computer network. The plant's production resumed on Tuesday.

US: North Korea's been hacking everyone since 2009
US authorities believe the North Korean government has been using an army of hackers called "Hidden Cobra" to deploy cyber attacks over the past eight years. That's according to the Technical Alert formally issued by the Homeland Security and the FBI, which contains the details and tools NK's cyber army has been using to infiltrate the media, financial, aerospace and critical infrastructure sectors in the US and around the globe. The government agencies issued the alert after tracing the IP addresses of a malware variant used to manage NK's DDoS attacks to North Korean computers. While other players can spoof their IPs to frame NK, the US is encouraging cyber analysts to be on the lookout, warning them that the Asian country will continue to use cyber operations to advance its government's military and strategic objectives.
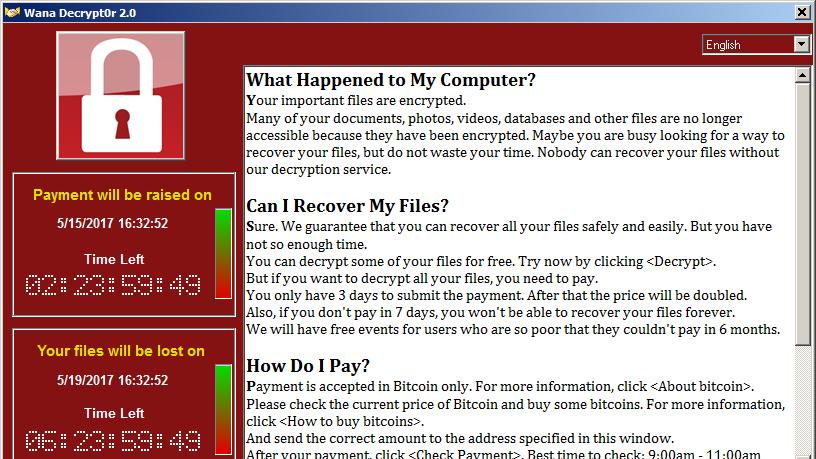
There's an easy fix for WannaCry, if you haven't rebooted yet
There's a glimmer of hope for a specific subset of victims in the WannaCry hack. Security researchers have released a fix that gets rid of the ransomware and restores a device's files, though it only works on Windows XP to Windows 7, and only on computers that have not been rebooted since the infection.
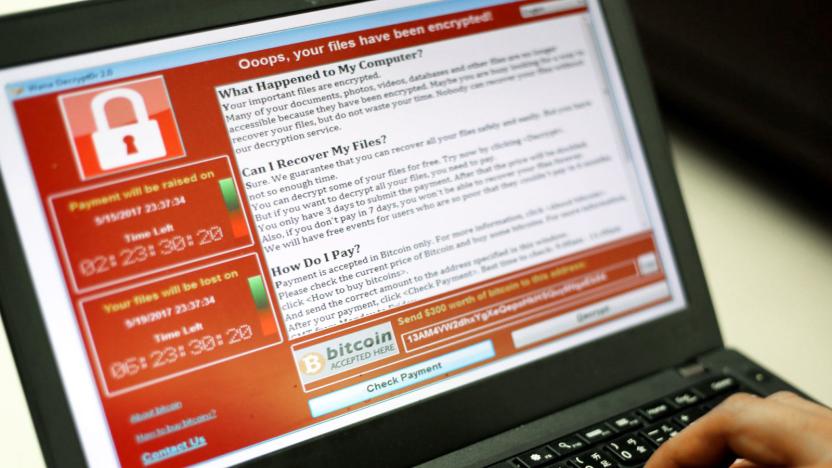
Pirated Windows led to WannaCry's spread in China and Russia
WannaCry, the notorious ransomware demanding up to $300 worth of Bitcoins to unlock victims' computers, hit systems all around the globe over the weekend. According to Finnish cybersecurity company F-Secure, though, Russia and China were affected the most, and it could be due to the rampant use of pirated software in those countries. Microsoft issued a patch for the vulnerability the attackers used as an entry point back in March and even fixed it for XP, which it long stopped supporting. However, pirated systems can't install those patches, so computers running illegal software remained vulnerable.

'WannaCry' ransomware showed traces of North Korean code
For all the damage the "WannaCry" ransomware has done, there's still one looming, unanswered question: who's behind it? At last, there might be a clue. Google researcher Neel Mehta has noticed that an early version of WannaCry's code shares similarities with a February 2015 sample from the Lazarus Group, a North Korea-linked outfit blamed for both the Sony Pictures hack as well as the Bangladesh Bank heist. The code changed between then and now, but it at least raises the possibility that North Korea was involved.

The 'WannaCry' ransomware is a stark reminder of a broken system
In April, a hacking group called The Shadow Brokers dumped a cache of Windows' exploits it pilfered from the NSA. The group had decided to start leaking exploits it stole from the agency after it was unable to find a buyer for the government's hacking tools. Inside that April drop was a remote code execution vulnerability called "EternalBlue" (aka MS17-010). Fortunately, Microsoft issued a security patch that fixed EternalBlue in March. What's not so fortunate is that not everyone had applied it to their machines.
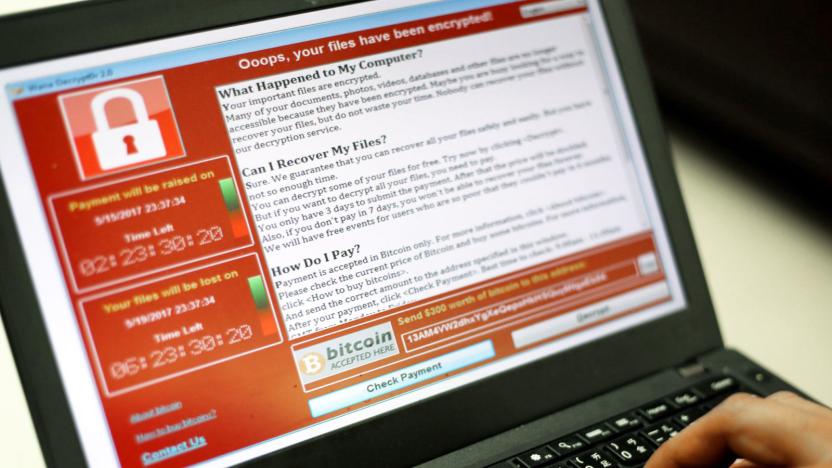
'WannaCry' ransomware evolves despite attempts to kill it
There were predictions that the fast-spreading "WannaCry " (aka "WannaCrypt") ransomware would quickly evolve to get around its domain-based kill switch, and, well... the predictions were right. Security researchers have discovered variants of the Windows malware that either have different kill switches (easy to stop by purchasing the web domain) or don't have a kill switch at all. MalwareTech's initial findings might have stopped the original WannaCry in its tracks, but that was really just a speed bump for malicious coders.

'WannaCry' ransomware attack spreads worldwide (update)
England's healthcare system came under a withering cyberattack Friday morning, with "at least 25" hospitals across the country falling prey to ransomware that locked doctors and employees out of critical systems and networks. It's now clear that this is not a (relatively) isolated attack but rather a single front in a massive digital assault. Update 2 (5/13): In response to infections like the ones that crippled parts of the NHS system, Microsoft is releasing a patch for unsupported systems including Windows XP, Windows 8 and Windows Server 2003.

NHS hospitals in England hit by a widespread cyberattack (updated)
Various NHS Trusts are currently battling with what appears to be a large-scale cyberattack affecting IT systems across the country. According to reports, hospitals and GP surgeries are falling victim to a widespread ransomware attack, causing them to shut down their computer networks. The East and North Hertfordshire NHS Trust was one of the first to acknowledge the problem and switch off its systems, warning locals that they will have trouble getting through on the phone and asking them not to visit accident and emergency unless absolutely necessary. Update: The attack has continued to spread and is now affecting systems around the world. Update 2 (5/13): In response to infections like the ones that crippled parts of the NHS system, Microsoft is releasing a patch for unsupported systems including Windows XP, Windows 8 and Windows Server 2003.






