attack
Latest

Yahoo's latest transparency report reads like tonedeaf fluff
Following all the trouble it has had lately, Yahoo has released its annual transparency report. Globally, the firm had 20,511 data requests, with almost half of them coming from the United States government (9,408). This doesn't tell the entire story, though. The company also issued a "users first" outline that reads like little more than PR fluff. "Our users place their trust in us, and we take seriously their privacy and our role in promoting freedom of expression," the report reads. "Our commitment to and concern for your privacy, security and freedom of expression are demonstrated in our users first approach to government activities." Sure, Yahoo.

Some of the biggest sites on the internet were shut down this morning (update: down again)
Happy Friday! If you've had trouble this morning accessing your favorite internet outlet, you're not alone. Dyn, one of the internet's biggest domain name servers (DNS) got hit with a distributed denial of service (DDoS) attack this morning, making it quite difficult to reach some of the biggest sites and services on the web. Twitter, Spotify, the New York Times, Reddit, Yelp, Box, Pinterest and Paypal are just a handful of the sites under siege this morning.

Report confirms IoT botnet took down Krebs' security site
Two weeks ago, security researcher Brian Krebs' site KrebsOnSecurity got knocked offline by one of the biggest DDOS attacks ever recorded, which peaked at 620 Gbps. What happened? Akamai, which had been protecting the site for free but ultimately had to unload it as the sustained traffic would have cost them millions of dollars, released a postmortem today. In it, they confirm that the attacker mainly used the Mirai malware to ovewhelm Krebs' site, though there may have been another botnet involved. But the most crucial distinction from a normal DDOS strike: These bots were mostly IoT devices.

Acer admits hackers stole up to 34,000 customer credit cards
If you bought an Acer device from the company's store in the last year, there's a chance that your credit card info was hijacked. The Taiwan-based company informed California's attorney general that attackers made off with the "name, address, card number, expiration date and three-digit security codes" of users between May 12, 2015 and April 28, 2016. It sent form letters to the 34,500 affected customers, all of whom are in the US, Canada and Puerto Rico.
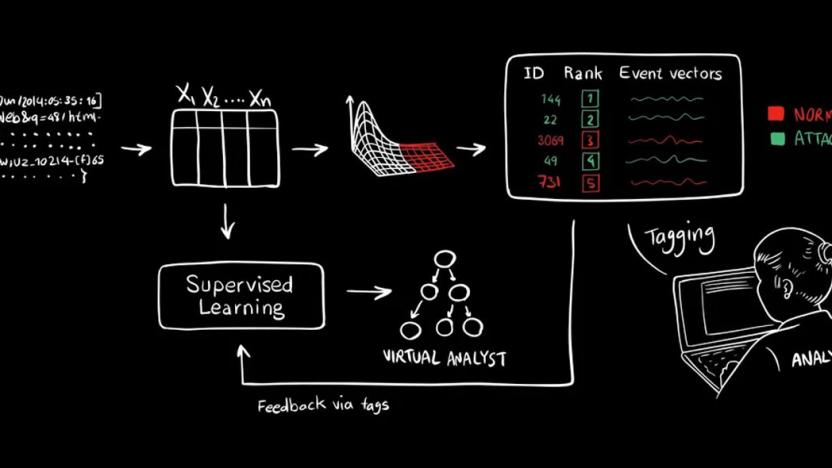
MIT's digital lookout in the crows nest of cyber warfare
"Think about the system as a virtual analyst," says Kaylan Veermachaneni, co-creator of MIT's latest artificial intelligence. He's a research scientist at the university's Computer Science and Artificial Intelligence lab that, along with Ignacio Arnaldo, built an AI that acts as a lookout for the age of cyber warfare. AI2 (Short for Artificial Intelligence Squared) is a system designed to spot a hacking attack better than humans and existing software. They claim that the program can detect 85 percent of malicious attacks, although that figure is set to rise the more it learns. We can already imagine Sony's IT gurus beating a path to Massachusetts with a suitcase stuffed full of unmarked bills.

Adobe warns users to patch a critical Flash vulnerability
Stop me if you've heard this one. Adobe has released a new patch for Flash that fixes "critical vulnerabilities that could potentially allow an attacker to take control of the affected system," according to the security bulletin. It says the update (version 21.0.0.182) is a top priority for users of Windows, Mac, Android, iOS and ChromeOS, so you should install it tout de suite. The upgrade patches 23 holes in the software, but Adobe said one of them, CVE-2016-1010 "is [already] being used in limited, targeted attacks."

UK man arrested in VTech kids app hacking scandal
Police have arrested a 21-year-old UK man in relation to the VTech kid's app hacking scandal that compromised the accounts of up to 6.3 million users. The crime unit said he was being held on "suspicion of unauthorized access to computer[s] to facilitate the commission of an offense," but cautioned that the investigation was still in the early stages. The man was arrested in Berkshire, west of London, but his name wasn't released. As a reminder, the breach last month affected users of VTech's Learning Lodge app and Kids Connect chat program, and allowed the attackers to collect photos, chat logs and other private information.

Vodafone says 1,827 customers' bank details accessed in attack
In what's been a big week for corporate security following the TalkTalk hack, Vodafone has confirmed that it has also been the target of a malicious attack. In a statement today, the company said that between midnight on October 28th and midday on the 29th, it saw an unauthorised party attempt to access customer's details, including bank account numbers. Unlike its telecoms rival, which saw its website compromised via SQL injection, the carrier believes the source of the attack stems from criminals utilising "email addresses and passwords acquired from an unknown source external to Vodafone."

TalkTalk customers must prove fraud to avoid cancellation fees
With investigations making progress and a 15-year-old suspect in custody following a "significant and sustained" attack on its website, TalkTalk has begun notifying customers of their next steps. In its latest update, the company says that "as a gesture of goodwill," subscribers wishing to cancel their service can have their termination fees waived only if they can prove they had money stolen from them. Personal details including names, addresses, phone numbers and credit card/account numbers were taken in the attack, but the company later clarified that banking data was obfuscated and could not be used to directly empty customer accounts.

Facebook will warn you if you're subject to government 'attacks'
Imagine logging into Facebook to find a message telling you that your profile may have been targeted in a suspected state-sponsored attack. It's now a possibility, after the social network announced that it'll display a new notification if someone who is suspected of "working on behalf of a nation-state" has attempted to snoop on or take over your account.

One of Japan's lovable store robots was drunkenly punted
Just one month after Hitchbot was brutally attacked in Philadelphia, a shop assistant robot in Japan has also suffered the wrath of angry humans with a grudge. According to Japan Times, a drunken 60-year-old entered a Softbank store and, after an angry exchange, punted one of the company's cute Pepper robots. The kick-happy individual may not have thought too hard about the unit's humanity (or otherwise) but it's another in a growing list of anti-robot acts. A recent Wired piece points out that people's fears about futuristic AI stealing our jobs might be unfounded, since more people will be required to maintain our new overlords. As for the victim in this incident, Pepper's family have asked for privacy, but Japan Times believes that the robot is currently moving slower than normal, and may have suffered damage to its internals. Aww.

Russia apparently gets the blame for hacking Pentagon email
A couple of weeks ago the Pentagon's Joint Chiefs of Staff suddenly shut down its unclassified email network for all users, but didn't say why beyond citing "suspicious activity." Now, anonymous sources and unnamed government officials have told NBC and The Daily Beast that investigators believe the network was compromised through a spear phishing attacked launched by Russia. The only problem? Even for anonymous sources, they're kinda light on evidence.

Piracy app Popcorn Time vulnerable to hack attack
Get ready for a shock, but Popcorn Time, the illegal-as-hell streaming app for pirated movies, may not exactly be secure. Researcher Antonios Chariton told Torrent Freak that he found a vulnerability that could let attackers take complete control of your computer. The bad guy would have to be a "man in the middle," between you and Popcorn Time's Cloudflare infrastructure, ie, a local attacker, network admin or ISP. If so, he could intercept requests that are sent via insecure HTTP channels, and send a malicious "XSS" code response by exploiting another problem, the lack of input checks.

Teen arrested for breaking an entire school district's internet
A teenager from Idaho has landed themselves in hot water after arranging a takedown of their school district's internet access. KTVB News reports that the 17-year-old student paid a third party to conduct a distributed denial of service attack that forced the entire West Ada school district offline. The act disrupted more than 50 schools, bringing everything from payroll to standardized tests grinding to a halt. Unfortunate students undertaking the Idaho Standard Achievement test were required to go through the process multiple times because the system kept losing their work and results.

Hackers behind PlayStation Network, Xbox Live disruption reportedly targeting Tor
Lizard Squad, the merry band of hackers that claimed responsibility for taking Xbox Live and the PlayStation Network offline for Christmas, appears to have a new target: Tor. Reports of an attack on the network, which offers online anonymity, appeared earlier today, following a warning on December 19th of "Possible upcoming attempts to disable the Tor network." A Tor spokesperson acknowledged the attacks, but said they were unlikely to have an effect on users' anonymity. "This looks like a regular attempt at a Sybil attack: the attackers have signed up many new relays in hopes of becoming a large fraction of the network. But even though they are running thousands of new relays, their relays currently make up less than 1% of the Tor network by capacity. We are working now to remove these relays from the network before they become a threat, and we don't expect any anonymity or performance effects based on what we've seen so far.

World of Warcraft hit by DDoS attack on expansion launch day
There's something about a major launch that brings out all of the cyber griefers, and Warlords of Draenor's launch day is no different. Blizzard confirmed this evening that the game was hit by direct denial of service (DDoS) attacks that have been causing issues, and the studio is taking steps to combat it, including temporarily lowering the maximum populations on servers: We're excited to finally launch Warlords of Draenor and explore this new world with you, but we know that the experience has been less than ideal as we approach our first full day of launch. Europe was our first region to launch, and we encountered a few issues due to the sheer number of players attempting to enter Draenor from a single location. We worked to add multiple new ways to access Draenor, and this helped ease some of the initial rush into the new expansion as players were able to access it from their capital cities, as well as from the shrines in Pandaria. While that solution helped a ton for our North American launch, we ran into a few other issues, including a distributed denial of service attack, that resulted in increased latency. Later this evening, Bashiok updated players on the ongoing server issues as they unfolded over US prime time: We're continuing to work toward greater realm stability and address the service issues impacting latency. Our current biggest hurdle is the concentration of players in specific areas and zones, and an unexpected effect of that concentration on the realm stability. We're continuing to maintain a lowered realm population cap to help with the stability, which is resulting in increased queue times. We're seeing some increase in individual zones drop which are causing localized player disconnections as we get into primetime in the Americas, and if someone is disconnected they will quite likely run into a queue to log back in. Work is progressing on improving realm stability through fixes targeting individual in-game issues, as well as on the backend game and network services.

Trion's games DDoSed again
E-thugs are at it again: Trion's MMO services are once again under attack. Last night, the official RIFT twitter account announced, "Ascended, our servers are experiencing a DDoS at the moment. We're working to restore network stability as quickly as possible." On the official forums, RIFT Executive Producer Bill "Daglar" Fisher confirmed that ongoing RIFT lag problems are compounded by the attacks: "Adding on top of the oddities that people are reporting, we've also been under DDOS attacks and our network team has been working to minimize the impacts of these." Overnight, even the first few pages (five, as of the time of this writing) of the RIFT general forums were flooded with spam from attackers. Several low-traffic forums on the ArcheAge boards have also been spammed early this morning. [With thanks to Omedon for the tip and apologies to Daglar for the temporary demotion!]

PSA: PSN gets knocked down again [Update: Back online]
The PlayStation Network servers are currently out of commission for the second time in as many days. Sony posted a notice to its official Twitter account that its engineers are "aware of connectivity issues" and "are working to resolve" them. PSN suffered an outage for the majority of Sunday thanks to an apparent DDoS attack (distributed denial of service). Sony noted that no personal information was accessed in the attack. b=Both PSN and Sony Entertainment Network were "impacted by an attempt to overwhelm our network with artificially high traffic," though it's unclear if that's also causing today's issues. We'll update this post when PSN is up and running again. Update: Sony said that "network connectivity is being restored," and thanks players for their patience. [Image: Sony]

CloudFlare donates tech to stop politically-sensitive sites from being knocked offline
If protecting yourself from hackers wasn't tough enough, there's another crippling internet attack that knocks websites completely offline while you're a target: a denial of service attack. That's why a company called CloudFare has launched Project Galileo, a free service that helps "protect politically and artistically important organizations and journalists against attacks that would otherwise censor their work." CloudFlare has been in the business of protecting sites for quite some time, operating as a content delivery network that offers DDoS protection, but only to paid customers.

EVE and DUST DDoS attack not a threat to customers
This weekend's downtime in both EVE Online and DUST 514 -- the results of a distributed denial-of-service (DDoS) attack -- is now over and both CCP games are back online, according to a statement from the studio's COO, Jón Hörðdal Jónasson. CCP assures its customers that "at no time was customer data compromised or accessible in any way." Compensation to all EVE and DUST players will be announced soon.











