Personal Data
Latest

Barnes & Noble confirms hack exposed customer details
Barnes and Noble says payment information was not compromised, but your purchase history could have been.
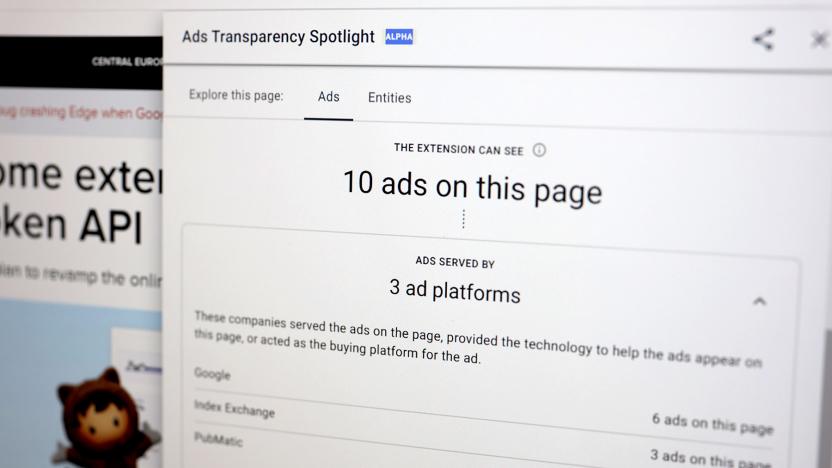
Google's latest Chrome extension shows detailed ad-tracking data
Google has released a Chrome extension that can give you more insight into how you’re being targeted by advertisers. Called “Ads Transparency Spotlight,” it shows the number ads loading on a page, the advertisers and ad tech companies present, and your personal data (demographics, re-marketing, interests, location, etc.) being used to serve the ads.
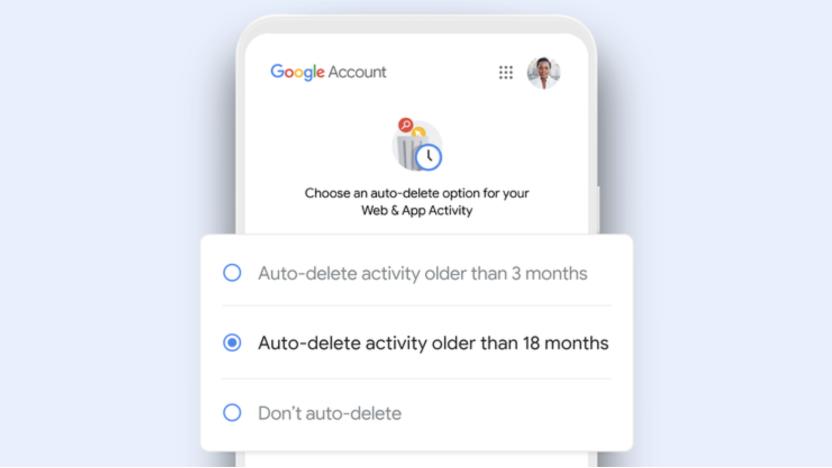
Google will auto-delete new users' web data after 18 months
Google will continuously delete your browsing and location history after 18 months.

India's proposed data laws give the government more access to data
The latest version of India's Personal Data Protection bill could require companies to gain permission before using individuals' personal data, and citizens would be able to demand their data be erased, The New York Times reports. The rules would also place fewer restrictions on the government, which would be allowed to request anonymized and non-personal data from companies. The latest version of the bill circulated this week. According to Financial Times, it was introduced to India's parliament today.

752,000 US birth certificate applications were exposed online
According to a report from TechCrunch, an online company that allows people in the US to obtain a copy of their birth certificate has exposed more than 752,000 applications. The case of negligence was discovered by Fidus Information Security, a company that conducts online penetration testing, and verified by TechCrunch. The two found that the company is storing the applications on an Amazon Web Services (AWS) cache that's not protected by a password. By simply entering the "easy-to-guess" address of the cache in a browser, a malicious visitor could access the documents held within. TechCrunch didn't disclose the name of the company to protect the privacy of those who used its service.

Amnesty International: Facebook and Google are a threat to human rights
Amnesty International, the premiere human rights organization, says Facebook and Google pose an unprecedented systematic threat to human rights. Specifically, Amnesty is concerned with the companies' "pervasive surveillance." In a new report, the organization warns against what it calls "omnipresent surveillance of billions of people" and calls for a "radical transformation of the tech giants' core business model."

Google is making its differential privacy tool available to all developers
Google wants to make it easier for other companies to safeguard their user's privacy. In a blog post, the tech giant announced today that it is releasing an open-source version of its differential privacy library. Differential privacy -- still a relatively new form of data science -- has been used by tech companies to mine large amounts of user data without violating individual privacy. In practice, the tool injects random noise into your personal data so it's impossible to tell individual users apart.

Surprise: People are listening to your Google Assistant queries
It's no secret that Google records your conversations with Google Assistant after you say a "wake word." But what you might not know is that Google uses contractors to manually review a handful of those recordings, about 0.2 percent. Yesterday, VRT NWS released reports detailing how it listened to thousands of recordings leaked by a whistleblower working for Google. At least one audio clip included a couple's address and personal information about their family.

TalkTalk admits attackers stole customers' personal details
TalkTalk has enjoyed its fair share of positive press in recent months, thanks to its new carrier deal with O2 and the acquisition of Blinkbox Movies, but there could be some rougher times ahead. In an email to customers, the quad-play provider confirmed that it was the target of an intrusion at the end of last year, which saw attackers steal personal data including names, addresses, phone numbers and TalkTalk account numbers. The company says that it has confirmed a number of cases where scammers have used that information to tease more sensitive details like bank account and credit card numbers from customers.

EU regulators ask Google to 'pause' its privacy changes, need more time to investigate
Google has gone to great lengths to clarify its revamped privacy policy, but a regulatory body in the European Union thinks the company is moving a little too fast. Today, European regulators formally requested that Google "pause" its rollout, in order to give the EU more time to investigate its forthcoming changes. "Given the wide range of services you offer, and the popularity of these services, changes in your privacy policy may affect many citizens in most or all of the EU member states," the EU's Data Protection Working Party wrote in a letter to Google CEO Larry Page yesterday. "We wish to check the possible consequences for the protection of the personal data of these citizens in a coordinated way." The body didn't specify how much time it would need to investigate, but it stressed that doing so would help to ensure absolute transparency among European users. "[W]e call for a pause in the interests of ensuring that there can be no misunderstanding about Google's commitments to information rights of their users and EU citizens, until we have completed our analysis," the letter reads. Viviane Reding, Europe's commissioner on data protection, heralded the move as an important step in asserting EU authority over online privacy and regulations, but Google was somewhat taken aback by the request. "We briefed most of the members of the working party in the weeks leading up to our announcement," said company spokesman Al Verney. "None of them expressed substantial concerns at the time, but of course we're happy to speak with any data protection authority that has questions." It's worth noting that Google isn't legally bound to heed the Working Party's request, though we'd expect the company to seek some sort of compromise with Europe's regulators, as it has in the past.

Vlingo co-founder explains data-collection issues
With Carrier IQ and O2's most recent data-snooping, people's vigilance about what information cellphones transmit is increasing. Using a Galaxy Note, AndroidPit found that every four minutes, Vlingo's voice-recognition app was sending a packet of data to an unencrypted server. The packet contained your GPS co-ordinates, IMEI (unique device identifier), contact list and the title of every song stored on your device -- without proper warning in the privacy policy you agree to when starting up the app. We spoke with co-founder John Wynn, product marketing head TJ Leonard and communications manager Erin Keleher, who gave us a full and frank discussion about what's going on and the steps it's taking to remedy the situation, which we've got for you after the break.

Carrier IQ VP says software poses no threat to user privacy, backs up his argument with metaphor
The final chapter of the Carrier IQ saga has yet to be written, but at this juncture, even the rosiest of rose-tinted observers would be hard pressed to find a silver lining. The specter of federal investigation looms larger by the day. Implicated carriers and manufacturers are washing their hands with Macbethian fury. Al Franken is on the verge of going Al Franken. And at the epicenter of all this sits Carrier IQ -- a California-based analytics company that has already gone to great lengths to defend its innocence. First, it sought to discredit Trevor Eckhart's ostensibly damning research with a cease-and-desist letter. Then, CEO Larry Lenhart flatly denied Eckhart's findings with an impassioned YouTube address. In recent days, the company has markedly softened its stance, arguing that its apps are only designed to meet operator demands and to "make your phones better." Now, Carrier IQ has elaborated upon these arguments with a more detailed breakdown of how its software functions, and a more substantive defense of its practices. Head past the break to read more.

WikiLeaks' Spy Files shed light on the corporate side of government surveillance
WikiLeaks' latest batch of documents hit the web this week, providing the world with a scarily thorough breakdown of a thoroughly scary industry -- government surveillance. The organization's trove, known as the Spy Files, includes a total of 287 files on surveillance products from 160 companies, as well as secret brochures and presentations that these firms use to market their technologies to government agencies. As Ars Technica reports, many of these products are designed to get around standard privacy guards installed in consumer devices, while some even act like malware. DigiTask, for example, is a German company that produces and markets software capable of circumventing a device's SSL encryption and transmitting all instant messages, emails and recorded web activity to clients (i.e., law enforcement agencies). This "remote forensic software" also sports keystroke logging capabilities, and can capture screenshots, as well. Included among DigiTask's other products is the WifiCatcher -- a portable device capable of culling data from users linked up to a public WiFi network. US-based SS8, Italy's Hacking Team and France's Vupen produce similar Trojan-like malware capable of documenting a phone or computer's "every use, movement, and even the sights and sounds of the room it is in," according to the publication. Speaking at City University in London yesterday, WikiLeaks founder Julian Assange said his organization decided to unleash the Spy Files as "a mass attack on the mass surveillance industry," adding that the technologies described could easily transform participating governments into a "totalitarian surveillance state." The documents, released on the heels of the Wall Street Journal's corroborative "Surveillance Catalog" report, were published alongside a preface from WikiLeaks, justifying its imperative to excavate such an "unregulated" industry. "Intelligence agencies, military forces, and police authorities are able to silently, and on mass, and [sic] secretly intercept calls and take over computers without the help or knowledge of the telecommunication providers," wrote Wikileaks in its report. "In the last ten years systems for indiscriminate, mass surveillance have become the norm." The organization says this initial document dump is only the first in a larger series of related files, scheduled for future release. You can comb through them for yourself, at the source link below.

Google announces 'opt-out' feature for wireless network owners, aims to allay privacy concerns
Google, as promised, responded to concerns over its data collection policy this morning, by announcing a new "opt-out" feature for its location based services. Under the new policy, WiFi operators can remove their home networks from Google's geolocation database by simply adding "_nomap" to the end of their access point's SSID. A network named "Engadget," for example, would be renamed "Engadget_nomap," and dutifully removed from the Google Location Server. In a blog post announcing the change, the company explained that this solution offers "the right balance of simplicity as well as protection against abuse," since it "helps protect against others opting out your access point without your permission." For more details, hit up the source link below, or check out Google's Help Center for more detailed instructions on how to opt out.

iSpy software can read texts and steal passwords with its little eye (video)
We spy, with our bleary eye, a new piece of software that could make it dramatically easier to steal personal data. The program, known as iSpy, allows devious voyeurs to remotely identify and read text typed on touchscreen displays. That, in and of itself, isn't exactly new, but iSpy takes shoulder surfing to slightly terrifying new areas -- namely, those beyond the "shoulder." Developed by Jan-Michael Frahm and Fabian Monrose of the UNC-Chapel Hill, this program, like those before it, takes advantage of the magnified keys found on most touchscreens. All you'd have to do is point a camera at someone else's screen and iSpy will automatically record whatever he or she types by stabilizing the video footage and identifying the enlarged keys. If you're using a smartphone camera, you'll be able to eavesdrop from up to three meters away, but if you opt for a more heavy duty DSLR device, you could steal passwords from up to 60 meters away. The software can also recognize any words typed into a device, and, according to its architects, can identify letters with greater than 90 percent accuracy. When used with a DSLR camera, iSpy can even pick up on reflections of touchscreens in sunglasses or window panes from up to 12 meters away. To avoid this, Frahm and Monrose recommend disabling the magnified key function on your smartphone, or using some sort of screen shield. We recommend checking out a video of the program, after the break.

Device Analyzer Android study wants to track your every move, if you'll let it
And here we thought folks were concerned about protecting their personal data. As it turns out, however, a surprising chunk of Android users have volunteered to give a group of University of Cambridge researchers a look at exactly how they use their cellphones. By downloading the Device Analyzer app from the Android market, more than 1,000 participants have allowed the data collection program to harvest statistics in the background while they use their phones. Those statistics -- varying from when the power is switched on, to which apps are in use -- are then made available to users via the Device Analyzer website. Of course, this is Cambridge, a rather well respected institution of higher learning, and the researchers involved say the data collected is stripped of personal information "as best as possible," but we're not keen on anyone peeping our cell stats. If you're an Android exhibitionist, however, you can sign up for the study at the source link below.

Google's wardriving days are over, says Canadian privacy commissioner
When Google's Street View cars glide through your neighborhood next, you can leave the WPA2 encryption off -- Canada says that the company has "discontinued" the practice of snooping on unsecured WiFi networks with its mapping vehicles, and "has no plans to resume it." That's one of several findings in a report by Canada's privacy commissioner today, which also claims that the controversial data collection feature was the work of a single Google engineer, and that Google intends to use smartphones to pinpoint WiFi networks from now on. Naturally, the latter caused the commissioner concern that Android phones might capture the same data as the cars. Perhaps you'd best keep those shields up after all.

Street View cars mistakenly nabs personal data over open WiFi networks, says Google
Let this be a very strong reminder to password-protect your WiFi networks... but first, some backstory. In 2006, a Google engineer "working on an experimental WiFi project" wrote a piece of code for collecting "all categories of public broadcast WiFi data" -- basically, all information (known as "payload") downloaded and uploaded from an open / non-password protected network. That code -- by mistake, as VP of Engineering and Research Alan Eustace says -- wound up a year later into the software Google's Street View cars used to collect location-based data. Eustace addressed the situation in an official blog post today -- the revelation of the payload data reportedly discovered after an audit requested by Hamburg, Germany's data protection authority (DPA). The original intention, he said, was to obtain only SSID information and MAC addresses, but that just wasn't the case. Offering an open apology, he reassured that this affected only open networks and, given the cars being "constantly on the move," only fragments of data were collected -- fragments that he says were never looked at or even noticed until the audit. Plans are currently in action to remove the extraneous info -- "we want to delete this data as soon as possible, and are currently reaching out to regulators in the relevant countries about how to quickly dispose of it." Additionally, all affected Street View cars have been grounded, so that great idea you had about dressing up as a Power Ranger and getting yourself a spot in Google Maps coordinates? Looks like that loss of privacy might've afforded you some extra time to paint the helmet.

UK T-Mobile customer data sold to cold callers, responsible staff to be prosecuted
Let's be honest, who here is actually surprised that underpaid and overworked data workers would sell on our details for a few extra quid? Given the number of uninvited calls to our unlisted phone numbers, we know for a fact that somebody has been dishing our personal contacts to those Nigerian princes and caring loan consolidators, so it's no shock to learn that T-Mobile employees have been fingered for committing the deed and are now facing prosecution. We're told that inappropriately leaked information made its way into the hands of brokers, who then "cold-called the customers as their contracts were due to expire" without T-Mob's knowledge. Disappointed by the failure of current fines to discourage such illegal information trade, British Justice Minister Michael Wills has even called for "custodial sentences" to be levied against the poor slobs responsible. So, if you're scoring at home, that's now two black eyes for T-Mobile when it comes to keeping our data safe. For shame.

Used BlackBerrys sold for $20 at McCain-Palin blowout, contacts and emails included
It's pretty much common sense that when you're ditching your old cell phone you want to erase your personal data, contacts and emails -- or at least try to. Oh sure, there are plenty of examples of failing to do so, but this one's rather... shall we say, "special." Some operatives at Fox 5 in Washington, D.C. booked over to the McCain-Palin campaign headquarters' yard sale yesterday, and they saw some ultra cheap Blackberrys -- just $20 a pop, probably an inventor's discount -- so they picked up a few, undoubtedly thinking they'd make nice holiday gifts. They were kind of surprised to find that, after giving the 'Berrys some juice, one of them had 50 contacts for "campaign leaders, politicians, lobbyists and journalists" as well as hundreds of emails. When reached for comment, a campaign spokesperson said that "procedures are being put in place to ensure all information is secure," followed minutes later by a blank email CC'd to his entire address book with the subject line "We're so screwed."








