exploit
Latest

Update your iPhone now to patch a major 'Pegasus' vulnerability
Apple has released a critical iOS 16 security update for iPhones and iPads to patch a particularly malicious bug.

Google says Google and other Android manufacturers haven't patched security flaws
Google's Project Zero team says that Samsung, Xiaomi, Oppo and Google haven't deployed patches for vulnerabilities months after ARM issued fixes for them.

FromSoftware is nearly ready to restore Dark Souls PC multiplayer features
FromSoftware says it’s one step closer to restoring the PC servers for its Dark Souls games, months after the discovery of a remote code execution exploit forced the studio to take them offline.

Wyze was aware of a major camera security flaw for three years
Wyze knew for three years tha its original security camera had a flaw that let hackers access your video.

Apple's latest iOS and macOS updates fix a major web security flaw
Apple has released a swath of updates that fix a significant web security flaw on iOS, macOS and beyond.

'Dark Souls 3' security hole lets attackers hijack your PC
An exploit in 'Dark Souls 3' lets attackers hijack the PCs of online players, and the game's servers are down in response.
Safari exploit can leak browser histories and Google account info
A security flaw in Safari and WebKit lets sites obtain some of your browser history and Google account info.

Roku jailbreak gives users control over what channels they install
Now you can get root access on Roku devices and install your own software.

Researchers detail three new Intel and AMD Spectre vulnerabilities
Security researchers have discovered three new variants of Spectre vulnerabilities that affect Intel and AMD processors with micro-op caches.

Microsoft patches Exchange software flaws targeted by Chinese hackers
Microsoft has rolled out a security update to fix four zero-day flaws in Exchange Server that bad actors have been using to infiltrate companies and organizations across industries.

'Cyberpunk 2077' update fixes a save file exploit on PC
Hackers could have used malware attacks in mods to take over players' systems.

CDPR urges 'Cyberpunk 2077' players to avoid using mods for now
The publisher is working on a fix for an exploit that affects mods and custom saves.

iPhone exploit gave hackers control over WiFi without your input
Apple recently fixed an iOS exploit that let intruders control your phone over WiFi without any interaction on your part.

Homeland Security warns of a 'critical' security flaw in Windows servers
Homeland Security has issued an emergency alert for a Windows security flaw, Zerologon, that allows attackers to compromise entire networks.

Zoom fixed a vanity URL issue that could have led to phishing attacks
It's been beefing up security since a pandemic-driven explosion in popularity.

Facebook paid for a tool to hack its own user, then handed it to the FBI
According to Motherboard, Facebook paid a security firm to develop a hack that the FBI eventually used to bring down a serial child abuser.

Nintendo says 140,000 more NNID accounts were vulnerable
Nintendo's NNID breach was bigger than originally reported.
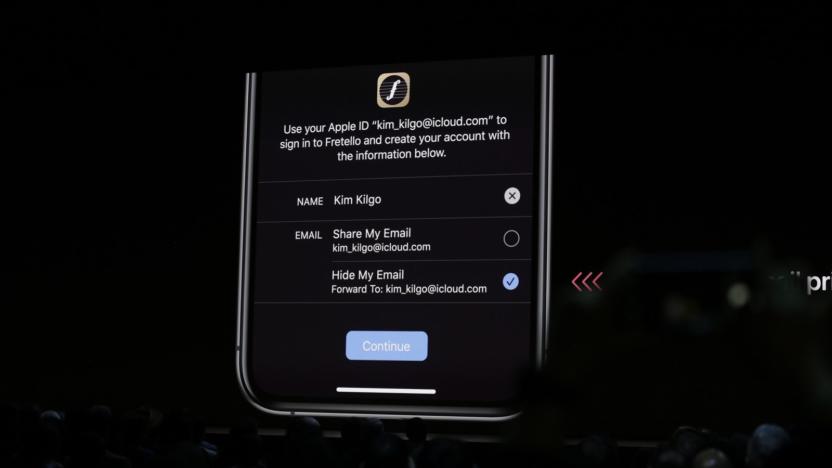
'Sign in with Apple' flaw let attackers take over accounts
A recently fixed 'Sign in with Apple' bug would have let intruders take control of accounts.

The latest iOS jailbreak cracks virtually any iPhone
A new jailbreak can open up virtually any iOS device, including ones using Apple's latest software.

Thunderbolt flaw lets hackers steal your data in 'five minutes'
Attackers can steal data from Thunderbolt-equipped PCs or Linux computers, even if the computer is locked and the data encrypted, according to security researcher Björn Ruytenberg.








