The only way to stop another WannaCry is with regulations
It's necessary to make cybersecurity a priority.
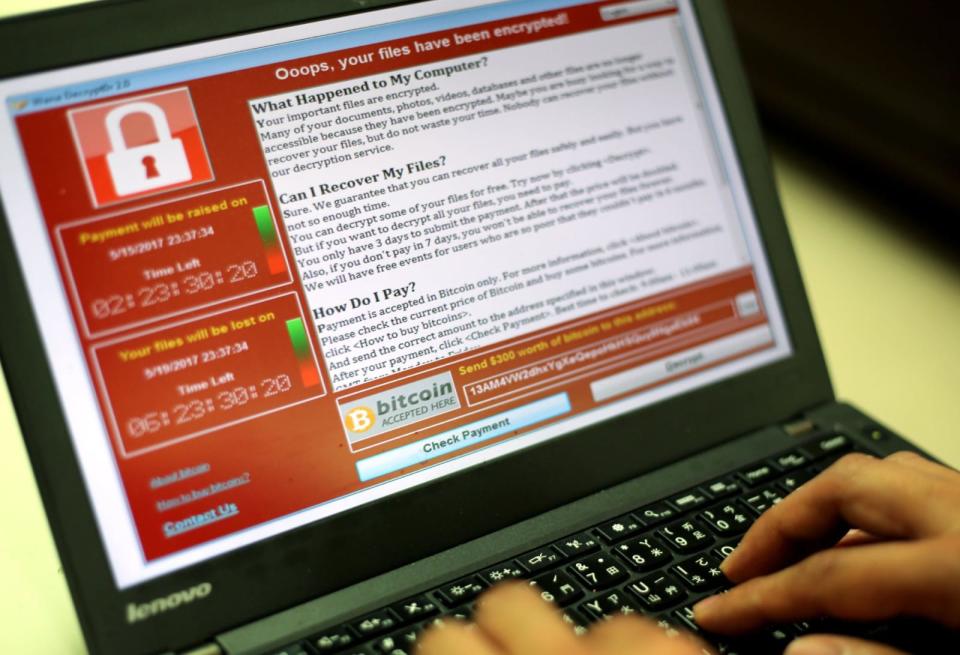
It's been one week since the newest (and therefore scariest) cyberattack, which caused pandemonium across Ukraine and Russia before spreading to other countries. But that came only a few weeks after the WannaCry ransomware targeted Windows XP machines worldwide, which infamously held data from the UK's National Health Service hostage. You might think we've entered a new era of cyberattacks, one that could threaten all of the machines in your home and every internet-connected service you rely on.
The truth is much more boring: It's what we've always dealt with. Sure, in a post-Stuxnet world, there are more countries than ever dabbling in cyberwarfare. But they're generally relying on the same sort of software flaws hackers have been using for decades. If this is all old hat, though, why aren't we getting better at preventing major cyberattacks? Simply put, there still isn't enough motivation for organizations to step up their security practices -- even in the midst of an avalanche of headline-grabbing attacks.
"The larger problem is you have to think about how to get people to do the basics — get them updating and using better authentication," James Lewis, senior vice president at the Center for Strategic and International Studies, told Engadget. "I don't think there's enough of an incentive yet for the market to do this. And when the market isn't doing it, you have to think of regulation."
After a series of cyberattacks targeted New York financial and insurance companies -- including the 2015 Anthem breach, which exposed personal data of 78 million people -- the state responded with one of the country's first set of cybersecurity regulations. It requires that financial-service firms hire a chief information security officer (CISO) to manage and document their cybersecurity plans. Additionally, companies must notify New York's Department of Financial Services of any breach attempts and ensure third-party firms that handle their data implement their own cybersecurity measures.
The New York regulations force potentially vulnerable companies to step up their efforts and accept accountability. Even with the looming threat of losing customer data, it's difficult to make huge companies change their security behavior on their own. While it's too early to tell if the regulations have actually helped stop any major attacks, the measures are at least more proactive than what organizations have done in the past. On the national front, Trump's cybersecurity order doesn't bring much to the table aside from more calls for surveillance.
"The economy would be better off if we could deregulate. That doesn't work for cybersecurity," Lewis said. "Companies hate regulation, I get it. But then you're going to say, 'Well, we're giving up on public safety.'" He likens the current situation with how American car companies, in particular, Ford, were resistant to seat belts and other safety regulations in the 1960s. And that was despite widespread research that seat belts would save customers' lives.
"Many of the temporary standards are unreasonable, arbitrary and technically unfeasible," Henry Ford II, then-CEO of Ford, warned at the time. "If we can't meet them when they are published, we'll have to close down."

A darker possibility that could make security a priority is a massive cyberattack. While WannaCry came close, especially with its effect on the NHS, Lewis notes it really just exposed people who were slow to patching. There's the potential for attacks to be even more aggressive and put even more lives in danger. While it would be nice to see extensive regulations pushing security initiatives, it's not hard to imagine that many firms will resist any change until they're forced to deal with serious consequences.
Following the WannaCry attacks, Microsoft's legal head and president, Brad Smith, blamed the NSA and the US government for "stockpiling" the exploit behind it. That security flaw was discovered by the NSA but stolen earlier this year by hackers. And while Microsoft patched the issue once it was made aware, that didn't help the millions of people running Windows XP and Windows Server 2012 who didn't update. Some companies are stuck with XP because they rely on legacy software and, of course, some users just never get around to updating. XP is 16 years old, and Microsoft officially stopped supporting it in April 2014, so it's surprising they patched it at all.
"We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world," Smith wrote. "Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage. An equivalent scenario with conventional weapons would be the U.S. military having some of its tomahawk missiles stolen. And this most recent attack represents a completely unintended but disconcerting link between the two most serious forms of cybersecurity threats in the world today: nation-state action and organized criminal action."
Lewis considers Microsoft's appeal an attempt to pass the blame, but he notes that governments should be more transparent about their cybersecurity discussions. We've been hearing about talks occurring between the US, China and Russia during the past decade, but they haven't been well-publicized. And while Microsoft's Smith is calling for digital Geneva Conventions to get countries to agree to a certain set of cyberwarfare rules, Lewis doesn't think there's much incentive for a country like Russia to come to any agreement. "What's a cyberattack? People can't even agree on that," Lewis said.
Because it will be incredibly difficult to force other countries to play fair when it comes to cyberwar, the need for regulation seems more pressing than ever. We can't control what other people do, but we can at least prepare for potential attacks as best we can.



