exploit
Latest

Here's how the NSA spied on Cisco firewalls for years
Edward Snowden leaks revealed that the NSA had the ability to spy on Cisco firewall traffic for years, but just how did the agency do it? We now have a clearer idea. An analysis of data from the Equation Group hack shows that the NSA used a specialized tool, BenignCertain, that uses an exploit in Cisco's Internet Key Exchange implementation to extract encryption keys and read otherwise secure virtual private network data. Cisco has confirmed that the attack can compromise multiple versions of its old PIX firewalls, which were last supported in 2009.

Yes, 'No Man's Sky' has a few issues
No Man's Sky landed on PlayStation 4 this week, and it wasn't perfect. Cue a rash of backlash on Twitter, a few dozen angry Reddit threads and a handful of YouTube videos calling creator Sean Murray a liar and a fraud. Ah, the internet. Let's break down a few of the high-profile glitches that people have found so far:

Qualcomm chip security holes affect most Android phones
If you own vaguely recent Android smartphone, there's a good chance that at least one of Qualcomm's many chips powers it... and if so, you might be at risk. Check Point has revealed four vulnerabilities, bundled under the QuadRooter nickname, that take advantage of problems with Qualcomm driver software (for elements such as graphics, memory and routing) to get root-level access and install malware that could hijack your device. All an attacker needs to do is load a seemingly innocuous, permissions-free app to deliver the payload.
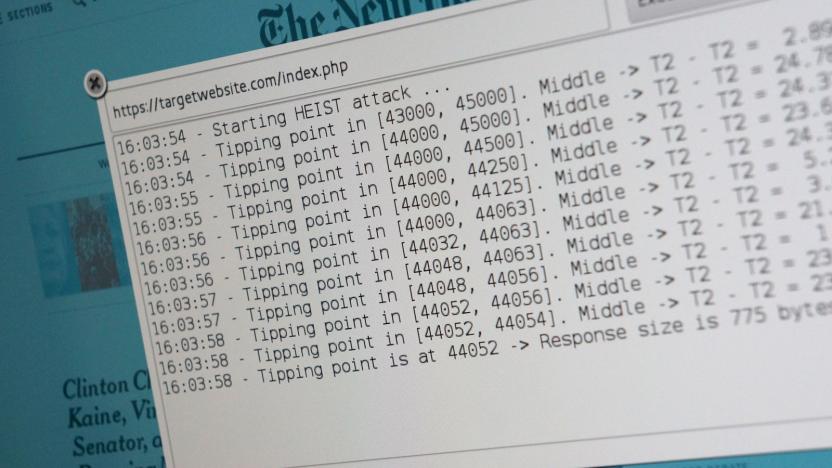
Exploit can attack secure websites through ads
Some web-based exploits are more dangerous than others... and unfortunately, this is one of the nasty ones. Security researchers at KU Leuven have discovered an attack technique, HEIST (HTTP Encrypted Information can be Stolen Through TCP-Windows), that helps compromise an encrypted website using only a JavaScript file hidden in a maliciously-crafted ad or page. Unlike many similar attacks, you don't need a man-in-the-middle spot to make this work -- it can gauge the size of an encrypted response (and thus enable an attack) all on its own. Combine it with another technique and it's relatively easy to pluck sensitive info from encrypted data traffic, such as email addresses and banking details.

Sony sued for not preventing piracy of movie leaked in 2014 hack
The fall 2014 Sony megahack leaked a massive amount of internal documents and content, resulting in plenty of fallout. Even two years later, they company is still not off the hook. The film To Write Love On Her Arms was one of four movies released online in the colossal data dump, and its producers are suing Sony Pictures failing to safeguard it from piracy thereafter.

Security bugs put Apple devices running iOS and Mac OS X at risk
Multiple security vulnerabilities were revealed by Cisco's Talos security team earlier this week, identifying areas at risk of possible exploits in iOS devices and Mac OS X. Some experts believe the exploits to be complex to pull off and likely not worth the time to attack. Regardless, the bugs have already been fixed in the latest versions of both operating systems.

Ancient Windows printer flaw exposes you to malware
Security holes don't always originate in relatively recent bugs... sometimes, they can stem from code written in an entirely different era. Researchers at Vectra Networks have discovered a roughly 20-year-old flaw in Windows Print Spooler (which oversees the printing process) that lets attackers slip malware on to a PC. As the spooler doesn't verify that a printer's drivers are legitimate when you plug the hardware in, it's possible for attackers to install maliciously-coded drivers thorough either the internet or the printer itself. The exploit can not only infect numerous computers if it's shared on a network, but keep infecting as computers discover the peripheral.

Chrome exploit makes life easier for video pirates
Media giants insist on copy protection systems in browsers to prevent bootleggers from copying video streams, but these anti-piracy measures aren't foolproof. Security researchers have found a flaw in Chrome (and any Chromium-based browser) that circumvents Google's Widevine digital rights management. As the system doesn't check to make sure that decrypted video is playing only in the browser, it's possible to capture that video right as it's passed to the browser's media player. With the right software, you'd only need to hit play to start copying a Netflix movie.

Password app developer overlooks security hole to preserve ads
Think it's bad when companies take their time fixing security vulnerabilities? Imagine what happens when they avoid fixing those holes in the name of a little cash. KeePass 2 developer Dominik Reichl has declined to patch a flaw in the password manager's update check as the "indirect costs" of the upgrade (which would encrypt web traffic) are too high -- namely, it'd lose ad revenue. Yes, the implication is that profit is more important than protecting users.

Your big-name PC may have a security flaw in its update software
Those problems with security holes in big PC makers' software bundles? They might not be over yet. Duo Security says it found vulnerabilities in the update software for Acer, ASUS, Dell, HP and Lenovo. Some vendors were more secure than others in Duo's testing, but all of them were insecure enough that you could launch a man-in-the-middle attack and run your own code. In the worst cases, they'd send update data without any encryption or validation.

Symantec antivirus security flaw exposes Linux, Mac and Windows
Security holes in antivirus software are nothing new, but holes that exist across multiple platforms? That's rare... but it just happened. Google's Tavis Ormandy has discovered a vulnerability in Symantec's antivirus engine (used in both Symantec- and Norton-branded suites) that compromises Linux, Mac and Windows computers. If you use an early version of a compression tool to squeeze executables, you can trigger a memory buffer overflow that gives you root-level control over a system.

John McAfee claims he can read encrypted messages on Android (updated)
John McAfee is already many things -- entrepreneur, presidential hopeful, alleged criminal. However, you might have to add one more item to that list: the co-discoverer of a potentially major Android security flaw. He and a team in Colorado claim to have found a hole in Google's mobile platform that lets them read encrypted WhatsApp messages (and those from other services, for that matter), rendering its privacy safeguards pointless. McAfee is saying precious little about how the intrusion works, but he supposedly gave Cybersecurity Ventures enough details to suggest that the story might hold up.

Simple exploits use images to attack websites
Would-be hackers don't always have to jump through hoops to bring down a website. Researchers have discovered relatively simple exploits in ImageMagick, a common package for processing pictures on the web, that let attackers run any code they like on a targeted server. If someone uploads a maliciously coded image and ImageMagick handles it, they could theoretically compromise both the site and anyone who visits it. That's particularly dangerous for forums and social networks, where user uploads are par for the course -- a vengeful member could wreck the site for everyone.

Nintendo pulls a 3DS game to fight another homebrew exploit
Nintendo's cat-and-mouse game with homebrew exploits isn't over yet. The gaming giant recently pulled Terry Cavanagh's retro platformer VVVVVV from the 3DS eShop after Shiny Quagsire discovered a way to use the game to run your own code. It's not a direct method, as you need another exploit for this to work (such as in the browser or another game), but that apparently doesn't matter to Nintendo.

Exploit gets around Windows' app security safeguards
For years, business-focused versions of Windows have had an AppLocker feature that lets you blacklist or whitelist apps. It's undoubtedly helpful for companies eager to keep malware (or just risky software) off their network. However, researcher Casey Smith has discovered a vulnerability in Windows that gets around this barrier. If you tell Regsvr32 to point to a remotely hosted file (such as a script), you can make a system run whichever app you want -- just what hackers and virus writers are looking for. It's stealthy, too, as it doesn't require administrator access or give itself away through registry changes.

FBI paid over $1.3 million to unlock San Bernardino iPhone
Today, FBI director James Comey noted that the cost to the bureau to unlock the iPhone used by San Bernardino shooter Syed Farook was more than what he would make in the seven years and four months before his retirement. Reuters busted out its calculators and determined that he would make $1.3 million in his time left as head of the government agency. So, you know, more than that.

Congressman calls for probe of longstanding mobile security flaw
It's no secret that Signaling System 7 -- a set of crucial protocols that define how phone calls, messages and data are routed through networks -- is flawed. Thanks to a recent report by 60 Minutes, though, at least one member of Congress was spooked enough to try and do something about it. According to The Daily Dot, Rep. Ted Lieu (D-CA) is now calling for a full investigation into the flaw that let a well-known security researcher track his movement through Los Angeles and record his phone calls without his knowledge.

Ancient apps leave 3.2 million PCs open to ransomware attacks
Criminals are relying on some particularly insidious ways to spread ransomware. Cisco's Talos group has discovered that intruders are taking advantage of vulnerabilities in old versions of Follett library management software (specifically, the associated JBoss web servers) to install backdoors and slip in ransom code. The attack has 'only' put 2,100 backdoors in place, but about 3.2 million systems are known to be at risk -- many of them at grade schools. Suffice it to say that many educators don't want to pay a hefty sum just to regain access to their library data.

Android's April security update tackles another Stagefright flaw
Google's monthly Android security updates are nothing new, but its latest release may be particularly important. The new April update tackles eight critical vulnerabilites that include one in the libstagefright library -- you know, the same media framework that recently faced a rash of real and potential exploits. It also patches a nasty kernel flaw that would give attackers full control over your device. You'll get first crack at the fixes if you either have a Nexus device or can install an Android Open Source Project build, but other vendors that offer Google's monthly updates will likely follow suit before long.

Recently patched security flaw bypassed OS X's new defenses
Theoretically, the System Integrity Protection introduced in OS X El Capitan makes it very hard to completely compromise a Mac. The feature prevents software from modifying protected files even if you have root access, preventing most software-based attacks from working. However, it's now clear that even this safeguard isn't airtight. SentinelOne's Pedro Vilaça has discovered a security flaw that -- combined with access gained via another method, like a phishing attack or browser vulnerability -- lets you run any code you like on a Mac, even with SIP in effect. The vulnerability takes advantage of a corruption bug in OS X to give a program full control over your system; since certain programs need full privileges for OS X to work (you couldn't update your system otherwise), the intruder just has to target the right file to hijack your computer.




