encryption
Latest

DOJ wants access to suspect's encrypted Facebook Messenger chats
The US government wants Facebook to help break Messenger's encryption to get access to a suspect's voice conversations in a criminal case, sources told Reuters. The case, an investigation of the MS-13 gang, is under seal so filings aren't publicly available. But the sources stated that Facebook has contested the DOJ's demand, and may be held in contempt of court for refusing.

Australian law could force tech firms to hand over customer data
Australia has been relying on criminal telecommunications legislation dating back to the days of the landline, so proposed laws unveiled today are designed to bring the country's legal enforcements in line with the many nefarious opportunities the internet presents for hackers. But it's raised eyebrows among some industry experts.
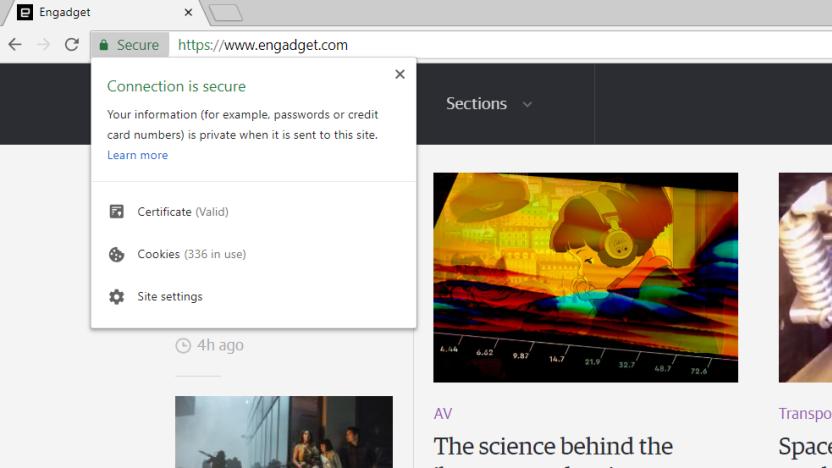
Chrome now alerts you to unsecured HTTP sites
Chrome has already taken numerous measures to inform users if they're on an unencrypted HTTP website, but starting today it's going one step further, with version 68 of the browser displaying a warning whenever you visit an insecure site. Instead of a green padlock and the word "secure" in the address bar, as you'll see on a HTTPS site, you'll see the words "not secure." Click on it and you'll get a warning advising against entering any sensitive information on the site, as it could be stolen by hackers.

Apple's new USB security feature has a major loophole
Apple's new USB Restricted Mode, which dropped with the iOS 11.4.1 release yesterday, may not be as secure as previously thought. The feature is designed to protect iPhones against USB devices used by law enforcement to crack your passcode, and works by disabling USB access after the phone has been locked for an hour. Computer security company ElcomSoft, however, has found a loophole.

Tinder user photos are now encrypted
In January, a security firm discovered that photos exchanged on Tinder weren't encrypted. If the firm connected to the same network as someone using the dating app, pics could be intercepted on their way between the app and the service's servers. Senator Ron Wyden (D-OR) wrote to the company shortly thereafter expressing concern over the vulnerability, but today Tinder wrote back assuring him that all photos are now encrypted, allowing you to upload your lovely or lascivious images securely.

The EFF wants to make email servers more secure
The Electronic Frontier Foundation (EFF) launched HTTPS-encryption initiative Let's Encrypt two years ago with Mozilla and Cisco. Now it's turning its attention to email servers with a new project called STARTTLS Everywhere, which aims to help server admins run STARTTLS emails servers properly. Because according to the EFF, most aren't.

WiFi's tougher WPA3 security is ready
WiFi security is finally getting an upgrade after 14 years. The Wi-Fi Alliance has officially launched WPA3, the next-generation standard that promises to tackle many of the vulnerabilities that have persisted in wireless networking. Most notably, it brings individualized data encryption that should protect your data against eavesdropping from within the WiFi network. You'll also get tougher password-based sign-ins through Simultaneous Authentication of Equals, a key establishment protocol that reduces the chances of someone guessing your password -- even if it's lousy.

Data-stealing router malware bypasses web encryption
A recently discovered strain of router malware appears to be much worse than thought. Cisco Talos has learned that VPNFilter can not only render devices unusable, but can bypass the SSL encryption you often see on the web. A module in the malware intercepts outgoing web requests to turn them into non-secure (that is, basic HTTP) requests, helping it steal sign-ins and other sensitive data when possible. It can also use man-in-the-middle attacks to insert hostile JavaScript into outside websites, and target devices beyond the router itself, such as PCs on the local network.

FBI admits to 'over-counting' inaccessible mobile devices
For the last two years, the FBI has repeatedly claimed that thousands of phones linked to criminal investigations were inaccessible due to locks and encryption. Last year FBI Director Christopher Wray said it had failed to access 7,800 mobile devices, but tonight a Washington Post report reveals that number is incorrect. According to the Post, the accurate number is between 1,000 and 2,000, with a recent internal estimate putting at about 1,200 devices, and in a statement, the FBI responded: "The FBI's initial assessment is that programming errors resulted in significant over-counting of mobile devices reported." The official excuse is that errors caused by multiple databases resulted in devices being counted more than once, but the issue has been an FBI and DOJ pursuit of backdoor access to locked phones. Then-director James Comey cited the inflated figure during a debate over the San Bernardino shooters' locked iPhone, and it has come up again in relation to similar incidents. Without being provided any backdoor by Apple, law enforcement gained access to that device anyway, and as we've recently learned, there are tools it can use for newer phones. The government has repeatedly referred to "Going Dark" as a major problem it faces in investigations, suggesting tech companies are enabling criminals by strengthening privacy protections that they can't get around. But privacy advocates have long thought the agency was pumping up its numbers, and now it's case has taken a significant hit.

‘Efail’ exploit exposes popular email encryption schemes
Encrypted emails guarded by common encryption tools are allegedly "susceptible to critical vulnerabilities" that would expose their content to potential hackers. Sebastian Schnizel, a computer science professor from the University of Münster called attention to the 'Efail' issue on Sunday via Twitter. He subsequently urged users of PGP/GPG and S/Mime software to disable it in their email clients.

Bipartisan bill aims to prevent the government from forcing backdoors
A number of US Representatives introduced the Secure Data Act today, bipartisan legislation aimed at preventing the government from forcing backdoors into encrypted products and services. The act was introduced by Representatives Zoe Lofgren (D-CA) and Thomas Massie (R-KY) and was cosponsored by Jerrold Nadler (D-NY), Ted Poe (R-TX) and Matt Gaetz (R-FL). "Encryption backdoors put the privacy and security of everyone using these compromised products at risk," Lofgren said in a statement. "It is troubling that law enforcement agencies appear to be more interested in compelling US companies to weaken their product security than using already available technological solutions to gain access to encrypted devices and services."

Twitter is testing an encrypted messaging feature
Twitter is reportedly testing a secret, encrypted messaging option that would enable its platform to go up against Signal, Telegram or WhatsApp. TechCrunch is citing developer Jane Manchun Wong, who found the feature after diving through Twitter's Android app. Twitter wouldn't give the site an official response, but if parts of the system have made their way into the app, clearly testing is at an advanced stage.

Iran tells ISPs to block Telegram
Iranian officials have called for ISPs to block both the mobile and desktop versions of Telegram in the country. ISPs are also reportedly being instructed to block the messaging service in a way that can't be bypassed by a VPN. Reuters reports that Iran's judiciary website Mizan, quoting a court order, said, "All internet providers in Iran must take steps to block Telegram's website and app as of April 30." The site also said that Telegram had threatened the country's security through "propaganda against the establishment, terrorist activities, spreading lies to incite public opinion, anti-government protests and pornography."

France creates secure chat app to keep its president off Telegram
Telegram is about to lose some more customers following the Russia ban, albeit for very different reasons. The French government is testing an encrypted messaging app that would keep officials' data on servers inside the country. It's worried about the "potential breaches" that could happen if data was encrypted in the US or Russia, and it's easy to see why. Between Russia's demand for Telegram encryption keys and Facebook's data sharing scandal, France is concerned that sensitive chats could end up in the wrong hands.

US lawmakers question FBI's decision to sue Apple in 2016
After the 2015 San Bernardino shooting, the FBI sued Apple to forcibly unlock the suspect's iPhone, asserting that the agency had exhausted all options before taking legal action. In the event, the bureau ended up reportedly paying an external vendor to break into the device. But last month, the Department of Justice poked holes in that justification with a report stating the FBI didn't do everything it could before bringing Apple to court. Today a bipartisan group of lawmakers sent a fact-finding letter to the agency's director Christopher Wray questioning whether the FBI could indeed have taken other action before the lawsuit.

Police across the US are buying an affordable iPhone cracker
More and more authorities in the US are getting access to an affordable device that can unlock iPhones, according to Motherboard. The publication's investigation has revealed that a number of local and regional police forces, including Maryland's and Indiana's, have either already bought or are thinking of buying a new piece of iPhone-cracking technology called GrayKey. It reportedly works even on phones running iOS 11, Apple's latest mobile platform, and even if authorities are using it on an iPhone X. Motherboard says the State Department already has one of its own, while the Secret Service and the Drug Enforcement Administration are planning to buy some.

Tor axes its secure messaging app due to lack of resources
The Tor team unveiled its Messenger app in 2015 to boost the security of existing chat clients, but those plans are coming to an end less than three years later. The developers are ending support for Tor Messenger due primarily to a lack of support. The developers behind Instantbird, the foundation of Messenger, have stopped working on the interface. There wasn't much overall progress on Messenger, for that matter. The app was still stuck in beta testing years after its debut, and the creators had to ignore bug reports and feature requests due to the limited resources.

ProtonMail brings encrypted contacts to its mobile email app
ProtonMail's encrypted contacts are now readily available beyond the web -- the company has updated its Android and iOS email apps to add the privacy-minded contacts manager. It uses zero-access encryption to prevent everyone but you (yes, including ProtonMail) from seeing anything besides a name and email address, and includes digital signatures to check for signs of tampering. It's pitched as ideal for journalists who may need to protect their contacts, but it could be just as important to you if you're worried that a thief might use your contacts as a burglary hit list.

DOJ: FBI prematurely took Apple to court over San Bernardino iPhone
In 2016, the debate over whether manufacturers should aid law enforcement officials in unlocking criminals' phones became very heated as the FBI took Apple to court over its refusal to unlock the San Bernardino shooter's iPhone. At the time, the agency said Apple was its only shot at getting access to whatever was stored on Syed Farook's iPhone 5c but it later used an outside vendor to crack the phone and get to its data. Now, the Justice Department's Office of the Inspector General has released a report that says the FBI didn't do everything it could to find a solution before seeking a court order against Apple.

New web security standard promises safer, faster browsing
It's safe to say that web security could use a tune-up given the deluge of malware attacks and data breaches. Thankfully, it's about to get one. The Internet Engineering Task Force has approved Transport Layer Security 1.3, a new standard that makes some fundamental improvements to how and when web encryption kicks in. For the most part, int involves both shrinking the window of opportunity for intruders and preventing them from recycling code.







