malware
Latest

Hackers stole credit card data from Buckle stores' cash registers
If you shopped at Buckle in the past several months, you might want to check your financial statements -- the clothing store has confirmed a Krebs on Security report of a data breach. Intruders planted malware on the chain's cash register systems to steal credit card data between October 28th, 2016 and April 14th, 2017. The potential data loss is limited if you used a relatively secure chip-based card, but it's much worse if you relied on the magnetic stripe. The malware looked at stripe tracking data to collect names, card numbers and expiration dates.

Malware downloader infects your PC without a mouse click
You think you're safe from malware since you never click suspicious-looking links, then somebody finds a way to infect your PC anyway. Security researchers have discovered that cybercriminals have recently started using a malware downloader that installs a banking Trojan to your computer even if you don't click anything. All it takes to trigger the download is to hover your mouse pointer over a hyperlink in a carrier PowerPoint file.

Russian malware link hid in a comment on Britney Spears' Instagram
Instagram is on its way to hitting a billion users this year and with that kind of popularity comes a lot of traffic. But lurking among all of many, many harmless comments that get posted each day, there's also the occasional post instructing Russian malware how to get in touch with its controllers. Because of course there is.
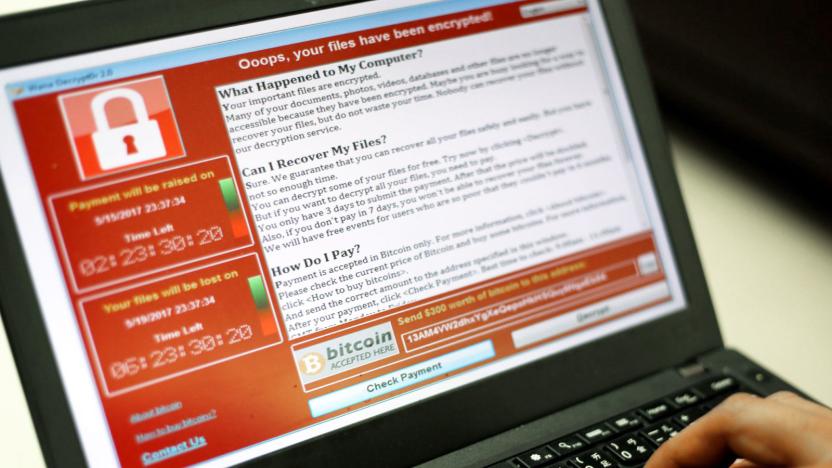
NSA would have to disclose its cyber exploit policies under new bill
It wasn't long after last week's devastating international ransomware attack before details surfaced about how the hackers found the exploit to target: It was stolen from the NSA, which stockpiles the digital vulnerabilities. Now, Democratic Senator Brian Schatz (HI) has introduced a bill that would create policy regulating how and when federal agencies would disclose known attack vectors.

'WannaCry' ransomware showed traces of North Korean code
For all the damage the "WannaCry" ransomware has done, there's still one looming, unanswered question: who's behind it? At last, there might be a clue. Google researcher Neel Mehta has noticed that an early version of WannaCry's code shares similarities with a February 2015 sample from the Lazarus Group, a North Korea-linked outfit blamed for both the Sony Pictures hack as well as the Bangladesh Bank heist. The code changed between then and now, but it at least raises the possibility that North Korea was involved.

NHS Trusts ignored patch that would’ve averted malware disaster
The ransomware attack that crippled crucial NHS systems across the UK and continues to cause disruption could have easily been contained, according to NHS Digital. The body, which oversees data and IT infrastructure across the NHS, said hospitals and other arms of the service had ample time to upgrade their systems. The 'WannaCry' malware variant used a Windows exploit Microsoft patched in mid-March this year. At the end of April, NHS Digital notified staff and "more than 10,000 security and IT professionals," pointing them to a patch that would "protect their systems." It seems this advisory fell on some deaf ears, which explains why only certain NHS Trusts were affected.
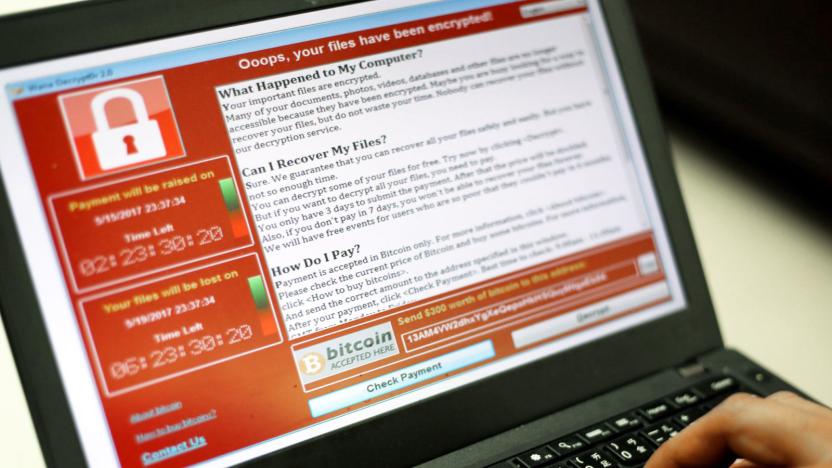
'WannaCry' ransomware evolves despite attempts to kill it
There were predictions that the fast-spreading "WannaCry " (aka "WannaCrypt") ransomware would quickly evolve to get around its domain-based kill switch, and, well... the predictions were right. Security researchers have discovered variants of the Windows malware that either have different kill switches (easy to stop by purchasing the web domain) or don't have a kill switch at all. MalwareTech's initial findings might have stopped the original WannaCry in its tracks, but that was really just a speed bump for malicious coders.

'WannaCry' ransomware attack spreads worldwide (update)
England's healthcare system came under a withering cyberattack Friday morning, with "at least 25" hospitals across the country falling prey to ransomware that locked doctors and employees out of critical systems and networks. It's now clear that this is not a (relatively) isolated attack but rather a single front in a massive digital assault. Update 2 (5/13): In response to infections like the ones that crippled parts of the NHS system, Microsoft is releasing a patch for unsupported systems including Windows XP, Windows 8 and Windows Server 2003.

NHS hospitals in England hit by a widespread cyberattack (updated)
Various NHS Trusts are currently battling with what appears to be a large-scale cyberattack affecting IT systems across the country. According to reports, hospitals and GP surgeries are falling victim to a widespread ransomware attack, causing them to shut down their computer networks. The East and North Hertfordshire NHS Trust was one of the first to acknowledge the problem and switch off its systems, warning locals that they will have trouble getting through on the phone and asking them not to visit accident and emergency unless absolutely necessary. Update: The attack has continued to spread and is now affecting systems around the world. Update 2 (5/13): In response to infections like the ones that crippled parts of the NHS system, Microsoft is releasing a patch for unsupported systems including Windows XP, Windows 8 and Windows Server 2003.

Microsoft just fixed a serious Windows Defender bug
Over the weekend, Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich tweeted about discovering "the worst Windows remote code exec in recent memory." According to Ormandy, it could work against a default installation and even become "wormable" -- able to replicate itself on a targeted machine and then spread to other computers automatically. Now we know more about what the problem is since, in just two days, Microsoft's Security Response Center and Windows Defender developers were able to come up with a fix that is now available via Windows Update for Windows 7, 8.1, RT and 10 (according to Microsoft, the Control Flow Guard security feature lowers the risk of this attack on 8.1 and 10), as well as other versions that IT professionals may be more familiar with.

'Major scale' malware targets your Mac through email scams
Mac users are increasingly being targeted by malware after years of being relatively safe, and that means they're facing attacks that other users have unfortunately come to expect for a while. Check Point researchers have discovered Dok, the first "major scale" trojan that targets macOS through an email phishing campaign. The bogus messages (usually aimed at European users) are meant to trick you into downloading a ZIP file that, if you launch it, gives the malware control over your system and lets attackers intercept your internet traffic to spy on your activity or impersonate websites. It'll even delete itself when the intruders are done.

Gag ransomware forces you to play an anime shooter game
A typical ransomware takes your files hostage in exchange for money, but "Rensenware" asks for something else. It forces you to play an anime-type shooter game called Touhou Seirensen (Undefined Fantastic Object) and score 0.2 billion points in Lunatic mode. Based on what we've seen of the gameplay, some of you might wish your computers were infected with ransomware that ask for a reasonable amount of cash instead. Rensenware, which was first spotted by the Malware Hunter Team, was created as a joke.

Invasive, self-destructing iOS hack is even worse on Android
Security researchers from Google and Lookout are warning Android users about "one of the most sophisticated and targeted mobile attacks we've seen in the wild." Called Chrysaor, it's the sibling of Pegasus, a zero-day iOS exploit that was used to spy on a United Arab Emirates human rights activist. Once installed, attackers are able to spy on calls, texts, and emails, microphone, camera, keylogging, GPS and other user data.

Trojan uses a key internet feature to receive marching orders
If malware uses a remote command-and-control server to function, it's relatively easy to cripple it by blocking the internet addresses it uses. It's not always that easy, however, and researchers at Cisco's Talos group have found a textbook example of this in action. A recently discovered Windows PowerShell trojan, DNSMessenger, uses the Domain Name Service for communication -- you know, one of the cornerstones of the internet. Few computer users are equipped to block DNS without causing other problems, and they might not notice unusual data traffic even if they're looking for it. While using DNS isn't completely unheard of, DNSMessenger uses an "extremely uncommon" two-way approach that both sends commands to victim machines and sends results back to the attacker.

Spyware targeted proponents of Mexico's soda tax
Surveillance-oriented spyware is dodgy in itself, but it's even worse when it's abused to intimidate political enemies -- just ask Mexican health advocates. The New York Times has learned that someone used commercial spyware from NSO Group to target proponents of Mexico's soda tax, including researchers and activists, right as they were rallying support for doubling the tax. The attackers sent personalized messages that warned of bogus news (say, a daughter's accident) and urged the victims to tap a link. If they did, the hostile would infect their devices and track everything from messages to location. It'd even quietly record camera footage.

Google explains how it spots malicious Android apps
Android's Verify Apps feature performs malware scans on newly downloaded applications to make sure they're safe. But since some malicious apps can prevent the feature from working, the company had to find an alternative way to figure out if a phone stopped using Verify because you no longer use it or if it's due to malware lurking in your device. In a blog post on Android Developers, Google explains how it detects if a particular application is harmful even with the absence of Verify's verdict. "To understand this problem more deeply," the post reads, "the Android Security team correlates app install attempts and Dead or Insecure (DOI) devices." To note, the team marks devices that stopped checking up with Verify as DOI and those that continue to use the feature as "retained."

Apple faces a price-fixing suit over App Store purchases
Apple is in court once again. This time, the company is part of an anti-trust lawsuit over the strict limitations over where users can buy iOS applications. Specifically, the requirement that all apps be purchased through the Cupertino company's App Store. The suit alleges that by not allowing customers to buy apps from third-party services, Apple was price fixing and that customers could sue as a result, according to Bloomberg.

Vermont power company finds malware linked to Russian hackers (updated)
Just a few days ago, the FBI and the Department of Homeland Security released a report detailing their assessment that Russian hackers were behind a series of attacks on US agencies and citizens. While the Obama administration issued sanctions, code linked to those hackers has been shared with other agencies, and on Friday, the Burlington Electric Department found malware with a matching signature on one of its laptops. The discovery raises more questions than it answers, but with recent reports of Russian hackers attacking the power grid in Ukraine, it obviously has raised alerts all over.

Barnes & Noble's $50 Nook came pre-installed with spyware
Barnes & Noble introduced the $50 Nook just in time for the holiday shopping season, but it failed to mention one crucial bit of software pre-installed on its 7-inch e-reader: malware. Specifically, the new Nooks came with an ADUPS program that granted a third party full access to all of a device's data plus complete control privileges. This means someone overseas had the ability to collect your personal information and wipe your Nook clean, if it had the ADUPS spyware installed.

Cybercrime network 'Avalanche' shut down in global sting
A mammoth cybercrime network known as Avalanche has been shut down, following a four-year investigation by German police and a coordinated strike by Europol, the FBI and agencies in many other countries. With a name like a Bond movie title, Avalanche was a sprawling cloud-based network that cybercriminals could rent, using it to distribute malware, ransomware, run phishing campaigns and launder extorted or stolen money.









