anonymous
Latest

Whisper app now includes related posts, still keeps your identity anonymous
Whisper, the anonymous secret-sharing app, now delivers a more personalized experience -- but don't worry; your identity will still be hidden. To show you relevant posts without revealing who you are or using your phone's address book, the Whisper team redesigned the app to show related content after you submit a new secret. In other words, the app isn't personalized to display confessions from people you know, but instead it delivers content related to your own anonymous secrets. Additionally, the app now sorts Whispers by location, so you'll be able to zoom into general (not super-specific) areas to see what users are talking about.
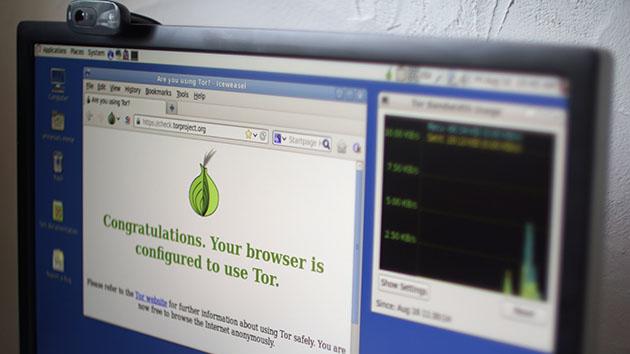
Edward Snowden's OS of choice, the Linux-based Tails, is now out of beta
Edward Snowden knows better than most how effectively the NSA can scope us online, so that's why he used the Amnesiac Incognito Live System (Tails) to cover his own whistleblowing. That OS is now out of beta as version 1.0, letting you surf on most PCs while leaving zero trace of your activities. Its anonymizing apps include email and IM clients, an office suite, a web browser, image and sound editors and the infamous Tor anonymity network system. There's no need for an installation, as it can run from a USB key, DVD or SD card independently of your existing OS, without touching your hard drives. If you've used the app before, the (anonymous) developers are advising you to grab the new release, as there are a host of security and bug fixes.

Facebook announces anonymous app login at F8 conference
Facebook founder Mark Zuckerberg is known for having dubious ideas about privacy. The billionaire founder is famously quoted in David Kirkpatrick's book The Facebook Effect as saying, "having two identities for yourself is an example of a lack of integrity" and "the days of you having a different image for your work friends or co-workers and for the other people you know are probably coming to an end pretty quickly." During today's F8 conference however it seemed that Zuckerberg and Facebook had come around to the idea of privacy, at least in small doses. After a three year absence Facebooks F8 conference has returned, bringing with it an exciting new development for the social media giant; anonymous login. Almost every modern app now requires you to login to an account before working. Most of these apps allow you to use your Facebook login instead of creating a new account each time you want to use a new app. Unfortunately using your Facebook login gives that app's developer access to an incredible amount of your personal information. Utilizing the new anonymous login feature users will be able to login to apps using their Facebook accounts without having to share their personal information with the developers. Once a user is comfortable with an app, they can change their settings to login with their actual Facebook account. Theoretically, more privacy should ultimately lead to users feeling more comfortable trying out new apps. Considering how many apps including sharing options back to Facebook, this news should help the company. This also removes the potentially embarrassing situations that can arise when someone uses your Spotify account to stream a Britney Spears album or three, only to have that information pop up on your Facebook feed. There's another angle to consider. Facebook is a social media giant, but they're also a giant data mining operation. They sell information about users to a number of sources for lots and lots of money. By removing an access point for app developers to gain information about the demographics of the users using Facebook to login to their app, Facebook may be opening up a new revenue stream. How valuable would it be to King, the makers of Candy Crush, to know who is playing their game and how they're sharing it? If a majority of new users start logging anonymously, the company is still going to want that information, and only Facebook will be able to share it. This is purely speculation, of course. As a user who reviews apps for a living, being able to login anonymously with my Facebook account will be a privacy godsend. We look forward to seeing how the feature is implemented when it launches in the future.

Anonymous' radio-based networking keeps protesters off the grid
Despite being an internet activist group, Anonymous knows the value of avoiding traditional communication; it's sometimes the only way for dissidents to elude surveillance and service disruptions. Accordingly, the group has just unveiled AirChat, a networking system that uses any available radio connection to share data between PCs. Nearly all of its infrastructure is based on encrypted data packets -- you need encryption keys to get a spot on the network and receive any private information, making it virtually impossible to fake an address. Users can share internet access if they get it, and there's support for both proxy servers and Tor routing to anonymize any online activity.

Hacker-turned-FBI informant may have orchestrated foreign cyberattacks
The hacker subplot in House of Cards' second season might have felt out of place, but from the sounds of a recent New York Times report, Frank Underwood's methods for putting captured hackers to work might not be too far-fetched. After being busted by the FBI, top LulzSec hacker Sabu may have conscripted at least one former accomplice to carry out a string of cyber-attacks against foreign banks and government websites, according to interviews and documents obtained by the Times. Sabu's seemingly indirect involvement suggests that he may have acted as a federal informant, helping to exploit the likes of the Heartbleed security flaw for state-sponsored cyber-terrorism. For the full report, be sure to head over to the source link. [Image credit: Idhren/Flickr]

Daily Roundup: Samsung Gear 2 review, allure of the anonymous internet and more!
You might say the day is never really done in consumer technology news. Your workday, however, hopefully draws to a close at some point. This is the Daily Roundup on Engadget, a quick peek back at the top headlines for the past 24 hours -- all handpicked by the editors here at the site. Click on through the break, and enjoy.

Shh, it's a Secret: The allure of the anonymous internet
"I'm terrified I might not actually be all that smart." "Made a batch of Jello just to stick my dick in it. No regrets." "I like taking the ferry because I get to drink in public legally." This is just a small sampling of posts I've recently seen on Secret, an anonymous-sharing app that's part of a new trend in Silicon Valley. It's a little like Whisper, a competing app that's been around since 2012, except that instead of letting you broadcast your anonymous missives to the world, posts on Secret are limited to a network of friends based on your phone's address book.

Dropbox goes down following problem with 'routine maintenance' (update 2: what happened)
We hope you weren't planning a big Dropbox sync this evening. The cloud storage service reports that it's having problems with its site following an issue with "routine internal maintenance." Just what that means isn't yet clear, although it's not believed to be an intrusion attempt. While Anonymous Korea and 1775 Sec claim to have hacked Dropbox, the company tells Engadget that the outage isn't the result of "external factors." That news won't be much consolation to those who still can't reach their online data, but it at least suggests that users won't have to worry about changing their passwords. Update: Dropbox says that its site is back -- as expected, it adds that claims of a leak are a "hoax." Update 2: A few days later, Dropbox has explained what happened. It was attempting to upgrade operating systems when a scripting bug reinstalled a number of active machines, bringing down Dropbox's service in the process. The company restored its core functionality within about three hours of the failure, but it took until Monday to get all its databases running smoothly. If this ever happens again, though, Dropbox will be prepared -- it built a tool that will let it recover much more quickly.

BitTorrent's peer-to-peer Chat service will use strong encryption to protect your identity
In the NSA age, being paranoid really doesn't mean they're not out to get you, so placating your fears has suddenly become a cottage industry. BitTorrent, for one, has just spilled more beans about Chat, it's peer-to-peer, encrypted messaging service that recently sent out a call for alpha testers. Rather than receiving a username, you'll actually be given a so-called cryptographic key pair, making it nearly impossible for others to guess your identity. Security is also enhanced with distributed hash tables (DHTs) -- like those used in uTorrent -- so that message requests are passed securely along the network to your intended recipient. That also avoids the use of a central server which could give a single point of attack for snoopers. There's no word yet on a release date, but the group is busy upgrading its backend for the service so you might be able to put the tinfoil hat in mothballs soon.

Pogoplug's new Safeplug anonymizes all your home's web browsing for $49
It's easy to worry about internet privacy these days, but it can be a pain to set up a Tor connection that keeps the snoops and thieves at bay. Pogoplug wants to simplify the process with its newly available Safeplug adapter. The peripheral connects to most any internet router and uses Tor to anonymize all web requests that pass through, saving the trouble of launching a special browser every time you want to keep your data secret. It can also join the Tor network to help safeguard others' information, if you're feeling generous. While the Safeplug won't be much help when you're away from home, it's relatively cheap at $49 -- a small price to pay if you don't want anyone tracking your web surfing habits.

Rumor: Maxis insider claims SimCity servers not essential
Though EA's official stance on SimCity's persistent Internet connection has been that it's absolutely required for the core game to function, a report from Rock, Paper, Shotgun claims that is not the case. An inside source who asked to remain anonymous told RPS the online servers are "not handling any of the computation done to simulate the city you are playing."According to the source, the servers are coordinating social messages between cities in a region, as well as "cloud storage of save games, interfacing with Origin, and all of that. But for the game itself? No, they're not doing anything."Even when the servers go down, certain cities have stayed online and playable for a period of time, suggesting off-site computation is not entangled in the main gameplay loop. The RPS source claims servers are also being used to repeatedly check for instances of hacking and cheating – and the game's verification messages to servers are creating queues and hampering responsiveness.Finally, the source casts doubt on EA's claims that a single-player version of this SimCity would be impossible to produce. "It wouldn't take very much engineering to give you a limited single-player game without all the nifty region stuff." EA's current public reasoning about why the game needs to stay online has done little to quell frustration voiced over the game's tremendous launch issues.Joystiq has contacted EA for comment regarding the source's claims.

Vint Cerf: Google services need a degree of anonymity, and they deliver it
Google has drawn flak for wanting much of our access to its services linked under a single Google+ identity -- and preferably a real one. However, company internet evangelist Vint Cerf argues that Google shouldn't (and doesn't) cross a line in the sand on user anonymity. He contends in a Reuters interview that no one should be forced to use their real name, and that Google won't press for one, especially in politically oppressive situations where there could be dire consequences to protesting under a real identity. What about less sensitive conditions, however? Cerf would like to strike a balance: he prefers solutions that "strongly authenticate" people when necessary, without eliminating anonymity altogether. We're glad to hear that there's a place Google won't go in its quest for social network supremacy, although we're sure some would like the search giant to take another step back and restore the controls over anonymity and privacy that they believe have been lost. [Image credit: Joy Ito, Flickr]

David Schuetz cracked the case of stolen iPhone UDIDs
Earlier this week, Blue Toad publishing confirmed that it, and not the FBI, was the source of 1 million UDIDs leaked by hacker group AntiSec. The company was tipped off by mobile security expert David Schuetz of Intrepidus Group, who spent days poring through the data and discovered references to Blue Toad and its employees. It's an impressive piece of work by Scheutz, who details how he discovered the Blue Toad link in a lengthy blog post on Intrepidus Group's website. His story is well worth the read when you have a few minutes to spare. [Via Apple 2.0]

Blue Toad publishing claims itself as source of leaked UDID database
According to a report in NBC news, a small publishing company is the source of Apple UDIDs leaked by hacker group AntiSec. AntiSec and Anonymous claimed the UDIDs were stolen from an FBI employee's laptop, but the governmental agency denied that it was the source the leak. Paul DeHart, CEO of Blue Toad publishing company, told NBC News that his company compared the leaked Anonymous database with its own database and found a 98 percent correlation between the two datasets. DeHart did not provide details, but said forensic analysis by his company showed the data a had been stolen within the past two weeks.

Anonymous: PSN hacked again, 10 million accounts at risk [update: Perhaps not]
A tweet by hacker group Anonymous links out to a document titled "Sony Hacked (LEAK) Playstation Network Pwned," containing a list of email addresses and what appears to be hashed passwords.The hacker claims to have about 50 gigabytes of information beyond what's in the document, and about 10 million accounts are "at risk." "Yes, if you play PlayStation Network, you're included <3." So yeah, change your passwords, remove your credit card info from your account. Unfortunately, you know the drill by now.Update: Kotaku reports that the list in the Pastebin doc is a copy of a seemingly unrelated list of email addresses from March 2012, called "Email accs! // universe security sucks." The PSN hack, in other words, appears to be a rumor that didn't turn out to be true. We're checking with Sony regardless.Still, when was the last time you changed your password?

Google Voice brings greater control over anonymous and unknown callers
Think about it for a moment: do you recall a single instance when you were actually glad that you answered a telephone call from a blocked number? Unless that bill collector turned out to be your future spouse, the answer is likely no. Now, Google Voice users will find an extra perk in the online settings that should take the edge off of receiving calls from unknown sources. You'll now find the ability to screen anonymous callers, whereby the system will prompt the individual to state their name, and only then will your phone ring. From there, you'll have the option of answering the call, sending it to voicemail, or even listening in as the caller leaves a voice message -- kinda like back in the days of answering machines. Similarly, you'll also find the ability to apply this same screening process to callers who aren't in your address book. As proof that Google isn't a total grouch, it's also thrown in a new option that allows you to customize a warm greeting for those contacts who are, in fact, in your address book. After all, it never hurts to show some love.

My whole life is a hack: how Geohot owned the iPhone, PS3 and inadvertently rallied hacktivists
George Hotz is no stranger 'round these parts. Better known as Geohot, he first achieved internet fame at the age of 17 with his announcement of a hardware unlock method for the original iPhone. From there, he moved on to even greater notoriety with a PlayStation 3 exploit that quickly attracted the ire -- and legal wrath -- of Sony. Now profiled in The New Yorker, we're given a candid and unique insight into the world of George Hotz, whereby his own admission, he wasn't motivated by an ideology so much as boredom and the desire to control a system. The freedom issues, it seems, were merely an afterthought. George Hotz is unique. We're talking about someone who was programming by age five, building video game consoles by the 5th grade and making appearances on NBC's Today at age fourteen. Like many brilliant adolescents, he experimented with drugs and rebelled against authority. Eventually, the powers that be caught up with him, and George Hotz was sued by Sony on January 11th, 2011. The lawsuit drew the attention of malicious hacker groups such as Anonymous and LulzSec, which retaliated against the company in very public ways. However unintentional, Geohot became the poster child for hacktivists and inspired a movement that quickly grew out of control -- if only more of us could be so productive with our boredom. For an insightful read into one of the most influential hackers of our time, be sure to hit the source link below.

How GeoHot went from winning science fairs to instigating the hacker war
Hackers built the Internet. Throughout the 1970s and '80s hackers altered the Internet from a strictly business communications system for the defense department and librarians into a robust online community for anyone with a computer to use as they pleased. The Internet and computer technology is still evolving, perhaps at a a faster, more public rate today, and hackers are still at the forefront of its design. Hackers such as Geohot, the guy who rooted Sony's PS3 early last year.George Hotz posted the PS3 root key online with a statement reading "I don't condone piracy" in January 2011 and it spread online. Geohot became an unsuspecting martyr in the hacker community when Sony sued him and won an injunction barring him from ever tampering with a Sony product again. Thus began the hacker wars, The New Yorker suggests in a biographical run-down of 2011's events.Hotz was brilliant in science and technology fields throughout middle and high school, winning $15,000 at the Intel International Science and Engineering Fair in 2007 and appearing in Forbes and on The Today Show for his technological achievements.He hacked the PS3 master key while he was high on OxyContin and Vicodin. He didn't condone or participate in any of Anonymous' hacks into Sony's servers, and since his online spotlight has faded he's worked for Facebook, quit and run amok in Panama, and met with Sony engineers curious about his methodology. He has reminders to "Call therapist" on his whiteboard. Geohotz is human, The New Yorker makes sure to point out.The full story is available here, or we figure you can just watch this eerily similar dramatic recreation of an antisocial programmer's rise to fame. They're both human, after all.

European carriers take shots at Nokia's Lumia line without leaving cover
Reuters reports that four big European carriers are disappointed by Nokia's Lumia range and its ability to compete with the big hitters from Apple and Samsung. None of the naysayers have been named, but an executive from one of the companies has been quoted as saying that "no one comes into the store and asks for a Windows Phone" and that Lumia handsets would be "easier to sell" if they ran Android. Another said Nokia should "lower the price" in order to make the Lumia range a loss leader and "get it out of the door." Meanwhile, AT&T claims to be having a different experience in the U.S., having gone to unusual lengths to market the Lumia 900 (even if that recent Time Square fandango was all Nokia) and now seeing it sell out in "many stores." That proactive approach appears to contrast with the attitude taken by some of Reuters's European insiders, who insist that all they can do is "open our stores to [Nokia] and train our staff to sell the phones."

Hacker spites Symantec, puts pcAnywhere's source code out in the open
Symantec said that folks running its pcAnywhere utility were at an "increased risk" when it revealed that the company had been hacked and its source codes pilfered, and advised customers to stop using pcAnywhere for the time being. Sage advice, as a hacker with the handle YamaTough -- who's affiliated with Anonymous -- helped do the deed and has now published the code for all the world to see. Apparently, the hacker and hackee had attempted to broker a deal for $50,000 to keep the code private, but neither side negotiated in good faith -- YamaTough always intended to release the code, and law enforcement was doing the talking for Symantec to catch him and his hacking cohorts. The good news is, Symantec has released several patches to protect pcAnywhere users going forward. As for the stolen code for Norton Antivirus, Internet Security and other Symantec software? Well, the company's expecting it to be disclosed, too, but because the code is from 2006, customers with current versions can rest easy.













