botnet
Latest

How an animated-GIF camera morphed into a nascent chip empire
Not many computers can thank GIFs for their existence. In 2013, Dave Rauchwerk worked on a San Francisco art installation that allowed people to record and project a GIF of themselves onto a building. It was popular and led to Rauchwerk joining with two friends to start a hardware company called Next Thing Co. Their aim? To create a camera that can capture GIFs for $100. After a long stay in China with the HAX Accelerator, Next Thing Co. launched OTTO, a $250 "hackable GIF camera" in 2014. It was the first product to integrate Raspberry Pi's Compute Module, and generated a lot of interest. Keen mathematicians may have noted the discrepancy in the intended and actual price -- $250 is many more dollars than $100 -- and the public did, too.

Twitter botnet quotes 'Star Wars' from the middle of the sea
Along with trolls and bullies, one of Twitter's biggest problems is bots -- automated accounts that puff up follower numbers, troll users or turn fake news into trending topics. Researchers investigating botnets found maybe the strangest one ever: 350,000 that tweet only random Star Wars quotes from Windows Phone devices. While that's actually kind of amusing, the researchers say that it reveals "profound limitations of existing bot detection methods" and shows the potential risks that hidden networks pose to the Twitter ecosystem.

Krebs pinpoints the likely author of the Mirai botnet
The Mirai botnet caused serious trouble last fall, first hijacking numerous IoT devices to make a historically massive Distributed Denial-Of-Service (DDoS) attack on KrebsOnSecurity's site in September before taking down a big chunk of the internet a month later. But who's responsible for making the malware? After his site went dark, security researcher Brian Krebs went on a mission to identify its creator, and he thinks he has the answer: Several sources and corroborating evidence point to Paras Jha, a Rutgers University student and owner of DDoS protection provider Protraf Solutions.
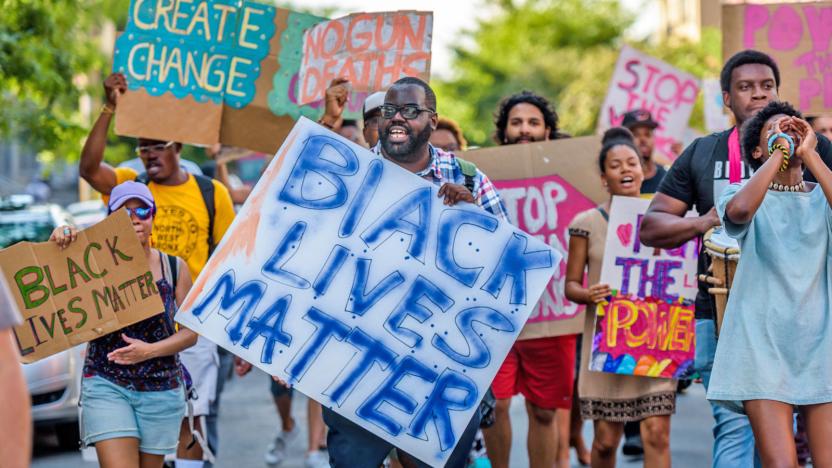
Black Lives Matter site faced over 100 attacks in half a year
When you launch protests in the modern era, you don't just have to worry about aggressive responses on the streets... you have to worry about your online presence, too. Deflect Labs has determined that Black Lives Matter's official website was subject to over 100 botnet-based denial of service attacks between April 29th and October 15th, a large part of it coming from members of a Ghost Squad hacking collective that had vocally denounced BLM's campaign. And it didn't require many people, either. Just two culprits (who may be the same person) launched nearly a fifth of the attacks, one of which tried to flood the site with traffic using nearly 1 million bots.

2016 claims another victim: Your privacy
In a blow to privacy on par with the Patriot Act, changes to the rules around warrants grant the US government unprecedented hacking powers in any jurisdiction, and on as many devices as it wants. The changes to a measure known as Rule 41 were made earlier this year but went into effect Thursday after lots of opposition. Basically, they let any judge issue a warrant to remotely access an unlimited number of computers and devices located in any jurisdiction. There was plenty of objection from senators and congresspeople, groups like the Center for Democracy and Technology and companies such as Google, who said it's unconstitutional and invades citizens' rights to privacy.

Cybercrime network 'Avalanche' shut down in global sting
A mammoth cybercrime network known as Avalanche has been shut down, following a four-year investigation by German police and a coordinated strike by Europol, the FBI and agencies in many other countries. With a name like a Bond movie title, Avalanche was a sprawling cloud-based network that cybercriminals could rent, using it to distribute malware, ransomware, run phishing campaigns and launder extorted or stolen money.

How an obscure rule lets law enforcement search any computer
With today's amendments to Rule 41, the statute that regulates legal search and seizure, the US Department of Justice has a new weapon to fight cyber crime -- but it's a double-edged sword. The changes expand the FBI's ability to search multiple computers, phones and other devices across the country, and even overseas, on a single warrant. In an increasingly connected world, amending the rules is both necessary for law enforcement agencies and deeply concerning for digital privacy advocates. And for everyday citizens, it's a little bit of both.

Mirai botnet targets Deutsche Telekom routers in global cyberattack
The German Office for Information Security confirmed on Tuesday that not only had nearly a million routers on the Deutsche Telekom (DT) network been recently attacked but that the assault was part of a larger campaign stretching across the world.
That time your smart toaster broke the internet
Where were you the day the internet died? Last Friday the internet had its biggest hiccup to date when a whole bunch of major websites were maliciously knocked offline. Harnessing the weak security of internet-connected devices, like DVRs and cameras, the attackers used botnets implanted on the devices to traffic-overload the one business keeping those sites' domain names functional.

Blame the Internet of Things for today's web blackout
Today's nation-wide internet outage was enabled thanks to a Mirai botnet that hacked into connected home devices, according to security intelligence company Flashpoint. The distributed denial of service attack targeted Dyn, a large domain name server, and took down Twitter, Spotify, Reddit, The New York Times, Pinterest, PayPal and other major websites.

Recommended Reading: The role of hip-hop in 'Luke Cage'
The Unexpected Hip-Hop Crossover in New Netflix Series 'Luke Cage' Adelle Platon, Billboard Based on the trailers Netflix released ahead of this week's Luke Cage debut, you might've guessed that hip-hop plays a big role in the new series. Thanks to Billboard, we have a full rundown of the score, cameos and background on the director for some added information ahead of the upcoming binge session.
Security writer recovers from massive revenge cyberattack
Journalists are no stranger to making enemies bent on retaliation. However, it's becoming increasingly difficult to survive that retaliation in the internet era... just ask security writer Brian Krebs. An unknown party knocked his website offline last week with a massive distributed denial of service attack (620Gbps of non-stop data) as revenge for exposing two major cyberattack sellers who've since been arrested. He's only back online after taking advantage of Alphabet's Project Shield, which protects journalists against censorship-oriented denial of service campaigns. His previous anti-DDoS provider, Akamai, had little choice but to drop him -- the company tells the Boston Globe that a sustained attack on that level would have cost the company "millions."

Major cyberattack seller knocked offline as it faces arrests
One of the more popular cyberattack peddlers just came crashing down. Israeli law enforcement has arrested Yarden Bidani and Itay Huri as part of an FBI investigation into their alleged control of vDOS, one of the most popular paid attack platforms. According to information unearthed by security guru Brian Krebs from a third-party hack targeting vDOS, the two teens raked in at least $618,000 launching "a majority" of the distributed denial of service campaigns you've seen in recent years. The platform itself is also offline, although that's due to one of vDOS' victims (BackConnect Security) using a bogus internet address claim to stem the flood of traffic hitting its servers.

FBI, Microsoft help take down massive global botnet
At long last, a global task force consisting of the FBI, Microsoft and various law enforcement agencies, have finally cracked down on a botnet with a ring of over 100,000 computers worldwide. Known as Dorkbot (not to be confused with the electronic art collective of the same name), the botnet is created by infecting computers with malware which then lets hackers use them for a variety of nefarious activities like sending spam or stealing personal info -- login info for sites like Facebook, Netflix, Gmail, Paypal and Twitter were particularly targeted. Researchers discovered that the Dorkbot botnet, which has eluded enforcement since April 2011, has affected well over a million Windows PCs in around 190 countries in the last year alone.[Image credit: Getty Images]

Malware turns hundreds of security cameras into a botnet
Closed-circuit security cameras are supposed to make you safer, but some malware is turning them into weapons. Researchers at Incapsula have discovered code that turned about 900 Linux-based CCTV cameras into a botnet, which promptly bombarded an unnamed "large cloud service" that serves millions of people. The intruders compromised cameras from multiple brands, all of which had lax out-of-the-box security -- in some cases, they'd been hacked by more than one person.

Darkode cybercrime forum seized as police arrest 28 members
In a coordinated takedown, law enforcement agents around the world have teamed up to shut down the well-known cybercrime forum Darkode, pursuing 70 of its members and associates resulting in 28 arrests so far. In the US, the Department of Justice and the FBI have announced criminal charges against 12 individuals including the site's alleged admin, Johan Anders Gudmunds, aka Mafi aka Crim aka Synthet!c, and the seizure of the site's servers. Dubbed Operation Shrouded Horizon, the effort by police in 20 countries took on a forum known as a place for cyber criminals to swap tips and tools (botnets, spamming services, you name it) of the trade. Brian Krebs has been reporting on Darkode's community for quite some time, including a profile published after its administrators tricked him into publishing details on a fake Java exploit.

Police kill money-stealing botnet that infected millions of PCs
Europol and police forces across Europe have shut down Ramnit, a botnet that infected up to three million computers world-wide. The virus, generally installed by email phishing attacks or rogue sites (please stop clicking on attachments, whoever your are) was mostly used by criminal hackers to steal banking info. If you were so foolish to click, the program gives hackers remote access to your Windows PC, letting them steal banking credentials, personal details and other info. The countries hit hardest were the US, India and Bangladesh.

Google fights rule that would let the US hack devices worldwide
The US is already snooping on computers around the world, but Google is worried that it might be sneaking in a rule change that would sanction more nosy behavior. The search firm has filed comments protesting an advisory committee proposal that would let the government get warrants for "remote access" to phones and PCs when their locations are hidden "through technological means." While the change is ostensibly targeted at American suspects masking their connections or running botnets, Google is worried that the proposal is worded such that it would allow law enforcement to hack into devices worldwide without any real political debate on the subject. After all, someone on a virtual private network could easily be in another country -- you might not know until you've broken in.

Facebook helps online services warn each other about security threats
Malware frequently strikes multiple targets, but online services rarely do a great job of warning each other about related threats; your data could be at risk simply because your favorite social network didn't get a heads-up in time. Facebook is clearly sick and tired of this problem, as it just launched a hub that's designed to mount a coordinated defense. Its new ThreatExchange web platform lets services both look up existing threat info and share their discoveries with as many sites as they see fit. If Facebook reels under a botnet attack, it can let others know what to do to protect themselves.

Apple updates Xprotect malware definitions to shut down 'iWorm' Mac botnet
Apple this weekend updated its XProtect malware blacklisting system in OS X to address the recent iWorm attack that allegedly infected more than 18,000 Macs. As noted by MacRumors and Business Insider, a change to the XProtect.plist file released on October 4 contained definitions to protect users from three variants of the iWorm malware, including OSX.iWorm.A, OSX.iWorm.B, and OSX.iWorm.C. Discovered by security researchers at Russian anti-virus company Dr Web, the iWorm malware targeted OS X machines, forming a botnet that was organized using a server list posted on Reddit. It is not known how the malware was spread, but an anonymous tip provided to The Safe Mac suggests the malware was bundled with pirated Mac software downloads available on The Pirate Bay. In addition to Apple's anti-malware actions, Reddit also shut down a fake Minecraft subreddit and banned the account that was posting the iWorm botnet server list to the subreddit's forums. Without these posts, iWorm-controlled Macs are unable to connect to the botnet servers that are used by hackers to send instructions to the infected machines.











