KasperskyLabs
Latest

Kaspersky says it briefly possessed classified NSA files
Earlier this month, reports surfaced that classified NSA documents detailing how US agencies defend their cyber networks and how they breach foreign ones were stolen by Russian hackers in 2015. Those reports noted that the files were spotted through Kaspersky security software used by an NSA contractor who had saved the classified documents on a home computer. Well, Kaspersky has now provided some more information about the incident and it has acknowledged that it did in fact have classified NSA materials in its possession, the Associated Press reports.
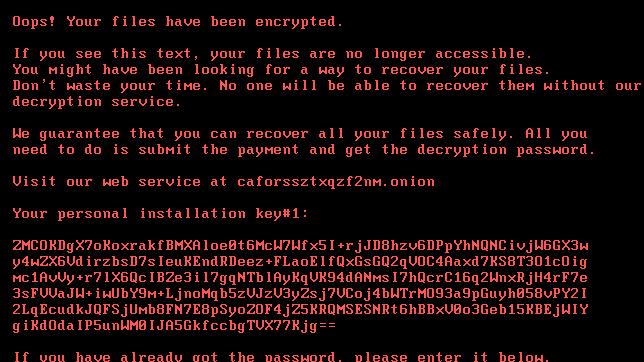
New ransomware is causing major issues across Europe and Russia
There's a new ransomware making the rounds today with confirmed targets in Russia, Ukraine, Turkey and Germany. Kaspersky Labs says that nearly 200 victims have been hit with the ransomware that's been dubbed Bad Rabbit.
Latest Adobe Flash vulnerability allowed hackers to plant malware
Adobe Flash may be on its way out, but apparently, its goodbye tour is going to be marred by security issues just as the software has for most of its existence. Kaspersky Labs reports that a new Adobe Flash vulnerability was exploited by a group called BlackOasis, which used it to plant malware on computers across a number of countries. Kaspersky says the group appears to be interested in Middle Eastern politics, United Nations officials, opposition activists and journalists, and BlackOasis victims have so far been located in Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, the Netherlands, Bahrain, United Kingdom and Angola.

Israel warned the US about Kaspersky after hacking its network
Kaspersky is in hot water...again. The US government recently prohibited federal agencies from using the company's products, and the FBI is reportedly convincing private entities to do the same. Its latest headache is linked to the NSA cyberattacks allegedly carried out by Russian hackers, who made away with official cyber defense material in 2015. The US intelligence agency claimed it noticed the stolen files using Kaspersky software. Little else was revealed about the incident (news of which broke last week) until now. It seems Israeli officials tipped off the US about the Russian intrusion, having hacked into Kaspersky's network, according to The New York Times.

Russian hackers reportedly stole NSA cyber defense material
The Wall Street Journal reports today that Russian hackers stole documents detailing how US agencies defend their networks against cyberattacks, how they breach foreign networks and the computer code they use to do so. Sources told the publication that the stolen files were identified through Kaspersky security software used by an NSA contractor that had taken classified material from the NSA and saved it on his come computer.

FBI reportedly advising companies to ditch Kaspersky apps
Kaspersky Lab's tussle with the US government could have ramifications for its dealings with the private sector. A new report claims the FBI has been meeting with companies to warn them of the threat posed by the cybersecurity firm. The briefings are the latest chapter in an ongoing saga concerning the use of Kaspersky's products by government agencies. Officials claim the company is a Russian stooge that can't be trusted with protecting America's critical infrastructure. The company denies these claims -- its CEO Eugene Kaspersky has even offered up its source code in a bid to clear his firm's name.

Russian authorities arrest Kaspersky researcher for high treason (updated)
Security researcher Ruslan Stoyanov from Russia's Kaspersky Labs was arrested for treason last December. According to Russian newspaper Kommersant (translated), Stoyanov was taken in for breach of Article 275 of the Crimes Against the Fundamentals of the Constitutional System and State Security. The specifics of why aren't exactly clear, however. Kaspersky has issued a statement saying that the arrest had nothing to do with Stoyanov's work at the Lab, and didn't offer any information beyond the following:

Report: Kaspersky developed malware to trip up competition
Reuters reports that a pair of former employees have accused Moscow-based Kaspersky Labs of building malware to trick its competition into flagging and quarantining important, non-viral, files on customers' computers. Basically the malware would inject malicious bits of code into important PC files -- like, say, your printer's .ini files -- which would then be flagged as a false positive and quarantined or deleted.

Kaspersky releases decryption tool that unlocks ransomware
You never should have clicked on the email attachment from that Nairobian prince. Now ransomware's got you locked out of your own computer and is demanding money before you can use it again. But before you reach for you wallet, take a look at this decryption key generator that Kaspersky has built. The Netherland's National High Tech Crime Unit (NHTCU) recently got its hands on a CoinVault command-and-control server (a type of ransomware that has been infecting Windows systems since last November) and, upon examining it, discovered a large database of decryption keys. The NHTCU shared this information with Kaspersky which used it to build the Noransomware decryption tool. Granted, the program isn't 100 percent effective yet -- it's not like the NHTCU got all of the potential keys off of that one server or anything -- but as police forces around the world continue to investigate the CoinVault ransom campaign, Kaspersky expects to grow the key database and further improve the tool's functionality. Plus, it's still better than paying some schmuck hacker to give you back your digital dominion.

High-tech TV: How realistic is the hacking in prime-time shows?
A group of five impeccably dressed high school girls are almost murdered dozens of times by the same, mysterious stalker and the police in their idyllic small town are either corrupt or too incompetent to care. How do the girls fight back? Hacking, of course. At least, that's one way they do it on Pretty Little Liars. "Hacking" is the deus ex machina in plenty of scenarios on Pretty Little Liars and other mainstream programs, allowing people to easily track, harass, defend and stalk each other 30 to 60 minutes at a time. But how real is it? To determine the feasibility of the hacks presented on shows like Pretty Little Liars, Sherlock, Scandal, Arrow, CSI: Cyber and Agents of SHIELD, I spoke to Patrick Nielsen, senior security researcher at Kaspersky Lab.

The NSA hides surveillance software in hard drives
It's been known for a while that the NSA will intercept and bug equipment to spy on its soon-to-be owners, but the intellgency agency's techniques are apparently more clever than first thought. Security researchers at Kaspersky Lab have discovered apparently state-created spyware buried in the firmware of hard drives from big names like Seagate, Toshiba and Western Digital. When present, the code lets snoops collect data and map networks that would otherwise be inaccessible -- all they need to retrieve info is for an unwitting user to insert infected storage (such as a CD or USB drive) into an internet-connected PC. The malware also isn't sitting in regular storage, so you can't easily get rid of it or even detect it.

Stuxnet worm entered Iran's nuclear facilities through hacked suppliers
You may have heard the common story of how Stuxnet spread: the United States and Israel reportedly developed the worm in the mid-2000s to mess with Iran's nuclear program by damaging equipment, and first unleashed it on Iran's Natanz nuclear facility through infected USB drives. It got out of control, however, and escaped into the wild (that is, the internet) sometime later. Relatively straightforward, right? Well, you'll have to toss that version of events aside -- a new book, Countdown to Zero Day, explains that this digital assault played out very differently.

Sophisticated malware finally discovered after 7 years, likely created by a nation-state
Security firm Kaspersky Labs recently released a research paper that uncovers the existence of a piece of highly complex malware that's been in circulation for almost seven years. It's called "The Mask," which is a rough English translation of Careto, a Spanish word for "ugly face" that was found in the malware's code. Aimed at high-level targets such as government institutions, embassies and large energy corporations, Kaspersky says "The Mask" has already claimed nearly 380 unique victims (with more than 1,000 IPs) in 31 countries that include China, France, Germany, the UK and the US. Kaspersky first spotted it in a spear phishing email campaign that entices the recipient over to malicious websites disguised as news sites like The Guardian and the Washington Post. Kaspersky reports that the malware is extremely sophisticated, with a set of tools that include a rootkit, a bootkit, versions that'll affect 32- and 64-bit Windows, Mac OS X, Linux and possibly even mobile operating systems like Android and iOS. Once it gets its hooks into your system, it can be used to hijack all your communication channels and snatch everything from Skype conversations to sensitive encryption keys. It's also very difficult to detect. Due to the level of finesse found in the malware, Kaspersky concludes that "The Mask" was very likely created by a nation-state, much like Stuxnet and Duqu. As to which nation-state that is, the security firm doesn't know, but says it's probably one that is Spanish-speaking based on the code's language. Intrigued? Go on and hit the PDF link here to get the full rundown of what Kaspersky discovered.

Ubisoft working with Kaspersky Lab to make Watch Dogs' hacking more true to life
Upcoming third-person action game Watch Dogs is set in a near-future environment modeled on Chicago, a city that's overseen by computers that can be manipulated. And while the game has some instances of fantastical hacking perpetrated by main character Aiden Pearce, Ubisoft's creative team is also working with security firm Kaspersky Lab to bring an air of realism to the game's hacking themes. "They have really hardcore experts there on hacking. We send them some of our designs and we ask them [for] feedback on it, and it's interesting to see what gets back," Ubisoft Montreal senior producer Dominic Guay told our sister site, Joystiq. "Sometimes they say, 'Yeah, that's possible, but change that word,' or, 'That's not the way it works.'" Check out the full piece right here. Along with a new Assassin's Creed game, Ubisoft is bringing Watch Dogs to next-gen consoles this year (as well as current-gen and PC), leading its next-gen push.

Russian technology firms agree to avoid poaching each other, keep salaries in check
American companies that reach no-poaching agreements do so behind closed doors, as it's considered illegal and anti-competitive. No such reservations appear to exist in Russia, as several of the country's top technology giants have openly admitted to reaching an unprecedented verbal deal: Acronis, Epam, Kaspersky Labs, Parallels and Yandex have all promised not to actively recruit each other's staff. They contend to CNews that it's a way to prevent salaries from getting out of control as staff are lured away, and that fear isn't entirely without justification -- there's a well-known salary war between Facebook and Google in Silicon Valley, for example, that makes it tough for smaller companies to attract the same talent. Whether or not the pact stands may be another matter. There's no history of Russian court action versus anti-poaching deals, but concern exists that the truce may not be strictly above-board. [Image credit: Jennifer Boyer, Flickr]

Kaspersky Labs preps its own OS to guard vital industry against cyberwarfare
Kaspersky Labs' namesake Eugene Kaspersky is worried that widely distributed and potentially state-sponsored malware like Flame and Stuxnet pose dire threats to often lightly protected infrastructure like communication and power plants -- whatever your nationality, it's clearly bad for the civilian population of a given country to suffer even collateral damage from cyberattacks. To minimize future chaos and literally keep the trains running, Kaspersky and his company are expanding their ambitions beyond mere antivirus software to build their own, extra-secure operating system just for large-scale industry. The platform depends on a custom, minimalist core that refuses to run any software that isn't baked in and has no code outside of its main purposes: there'll be no water supply shutdowns after the night watch plays Solitaire from an infected drive. Any information shared from one of these systems should be completely trustworthy, Kaspersky says. He doesn't have details as to when the OS will reach behind-the-scenes hardware, but he stresses that this is definitely not an open-source project: some parts of the OS will always remain confidential to keep ne'er-do-well terrorists (and governments) from undermining the technology we often take for granted.

Security researchers dissect Flame's handling program, find three new viruses 'at large'
It seems Stuxnet and Flame aren't the only out-of-control cyber-weapons roaming around the Middle East. Security researchers from Symantec and Kaspersky have found that the Flame malware had the electronic equivalent of a "handler," a program called NEWSFORYOU, which is also in charge of three further viruses that are code-named SP, SPE and IP. The trio have yet to be analyzed, because although a cache of data has been discovered on a command-and-control server, decoding it has proved "virtually impossible." While both security companies have declined to point a finger as to the viruses' origin, Reuters' sources suggest they're from the United States, while The Washington Post has been told that the project was a joint-enterprise with Israel -- in keeping with the existing narrative that this is the pair behind Stuxnet.

Spam-happy iOS trojan slips into App Store, gets pulled in rapid fashion
You could call it technological baptism of sorts... just not the kind Apple would want. A Russian scam app known as Find and Call managed to hit the App Store and create havoc for those who dared a download, making it the first non-experimental malware to hit iOS without first needing a jailbreak. As Kaspersky found out, it wasn't just scamware, but a trojan: the title would swipe the contacts after asking permission, send them to a remote server behind the scenes and text spam the daylights out of any phone number in that list. Thankfully, Apple has already yanked the app quickly and explained to The Loop that the app was pulled for violating App Store policies. We'd still like to know just why the app got there in the first place, but we'd also caution against delighting in any schadenfreude if you're of the Android persuasion. The app snuck through to Google Play as well, and Kaspersky is keen to remind us that Android trojans are "nothing new;" the real solution to malware is to watch out for fishy-looking apps, no matter what platform you're using. [Image credit: C Jones Photography (wallpaper)]

Flame malware extinguishes itself, Microsoft protects against future burns
The folks behind that nasty Flame trojan that burned its way through the Middle East aren't the kind to brag -- the malware's manufacturers apparently started dousing their own fire last week. According to Symantec reports, several compromised machines retrieved a file named browse32.ocx from Flame controlled servers, which promptly removed all traces of the malware from the infected systems. Although the attackers seem spooked, Microsoft isn't taking any chances, and has issued a fix to its Windows Server Update Services to block future attacks. The update hopes to protect networked machines from a similar attack by requiring HTTPS inspection servers to funnel Windows update traffic through an exception rule, bypassing its inspection. The attackers? "They're trying to cover their tracks in any way they can," Victor Thakur, principal security response manager at Symantec told the LA Times, "They know they're being watched." Check out the source link below for the Symantec's run down of the trojan's retreat.

Flame malware snoops on PCs across the Middle East, makes Stuxnet look small-time
Much ado was made when security experts found Stuxnet wreaking havoc, but it's looking as though the malware was just a prelude to a much more elaborate attack that's plaguing the Middle East. Flame, a backdoor Windows trojan, doesn't just sniff and steal nearby network traffic info -- it uses your computer's hardware against you. The rogue code nabs phone data over Bluetooth, spreads over USB drives and records conversations from the PC's microphone. If that isn't enough to set even the slightly paranoid on edge, it's also so complex that it has to infect a PC in stages; Flame may have been attacking computers since 2010 without being spotted, and researchers at Kaspersky think it may be a decade before they know just how much damage the code can wreak. No culprit has been pinpointed yet, but a link to the same printer spool vulnerability used by Stuxnet has led researchers to suspect that it may be another instance of a targeted cyberwar attack given that Iran, Syria and a handful of other countries in the region are almost exclusively marked as targets. Even if you live in a 'safe' region, we'd keep an eye out for any suspicious activity knowing that even a fully updated Windows 7 PC can be compromised.









