phishing
Latest

Feds arrest hacker for stealing scripts, celeb identities and sex tapes
The Department of Homeland Security has arrested and charged (PDF) a man from the Bahamas for stealing unreleased movie/TV scripts along with celebrities' files and sensitive information. According to The New York Times, the 23-year-old hacker named Alonzo Knowles contacted a radio host in an effort to sell his loot, which included the scripts for six episodes of a hit drama currently being filmed. When the unnamed host got in touch with Homeland Security, the agency cooked up a sting operation and had him put Knowles in touch with an undercover investigator posing as a buyer. Although the operation has not been publicly linked with any previously known hacking, it immediately calls to mind the stolen celebrity photos and information that were released late last year, as well as private information leaked by the people who hacked Sony Pictures.

Chrome for Android protects you from dangerous websites
Google Chrome already shields you from sketchy websites on the desktop, and now it's doing the same on your smartphone. Grab the latest version of Chrome for Android and you'll get the same Safe Browsing security measures that you've seen on your computer. You'll know if a site is perpetrating a phishing scam or pushing malware. It's not quite as comprehensive as on the desktop (Google saves data by limiting safety info to your region), but it could still prove a lifesaver if it keeps you from falling for a convincing fraud while you're away from your PC.

Vodafone says 1,827 customers' bank details accessed in attack
In what's been a big week for corporate security following the TalkTalk hack, Vodafone has confirmed that it has also been the target of a malicious attack. In a statement today, the company said that between midnight on October 28th and midday on the 29th, it saw an unauthorised party attempt to access customer's details, including bank account numbers. Unlike its telecoms rival, which saw its website compromised via SQL injection, the carrier believes the source of the attack stems from criminals utilising "email addresses and passwords acquired from an unknown source external to Vodafone."

Russia apparently gets the blame for hacking Pentagon email
A couple of weeks ago the Pentagon's Joint Chiefs of Staff suddenly shut down its unclassified email network for all users, but didn't say why beyond citing "suspicious activity." Now, anonymous sources and unnamed government officials have told NBC and The Daily Beast that investigators believe the network was compromised through a spear phishing attacked launched by Russia. The only problem? Even for anonymous sources, they're kinda light on evidence.

Epic Games is the latest hacking victim
Not even a chainsaw bayonette (or the stealthy gent up above) could stop Epic Games from falling prey to hackers. The Unreal Engine-maker sent emails to members of its forums announcing that unauthorized access to usernames, email addresses, passwords and birthdates may have been accessed by an intruder. From the sounds of it, the only channels affected were related to Bulletstorm, Gears of War, Infinity Blade, UDK, and older Unreal Tournament titles.
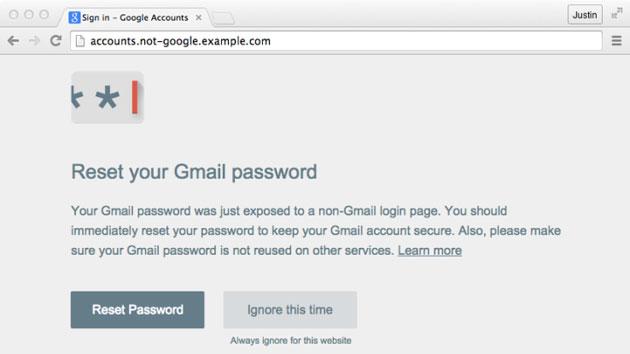
Chrome add-on stops scammers from getting your Google password
No matter how diligent you are about watching for scam sites trying to swipe your password, there's always the chance that a very convincing page will trick you into handing over the goods. Thankfully, Google just gave you a safety net: its new Password Alert extension for Chrome will warn you if you've reused your Google password on another site. You can ignore the warning if you're not worried, but you'll also have an option of resetting your password right away if you realize that you've made a mistake. It's a small add-on, but it might save you in a moment of weakness... or at least, remind you to spice up your password choices now and then.

If you want to chat on Steam, spend at least $5
Earlier this week Valve introduced Steam Guard Mobile Authenticator as a means to keep its users safe from phishing attempts, and now it's taken another step in that direction. From here on out, until you spend a minimum $5 with your account certain features are blocked. What're you going to miss out on? Friend invites, opening group chat, the Steam discussion boards and voting on Greenlight games among other things. But, considering that most people use the service for, you know, buying and playing games, this really should only affect those who're actively using the service for nefarious purposes.

Fraudster's phoney email tricked prison into releasing him
In the movies, a daring prison escape usually involves a carefully orchestrated plan filled with intricate tunnels, ingenious bribes and chaotic distractions. But for Neil Moore, performing a similar breakout in the real world was so much simpler. With the aid of a smuggled mobile phone, he was able to set up an email address with a domain that closely resembled Her Majesty's Court Service. He then sent a forged letter approving his release to the prison, hoping they wouldn't inspect the document or sender's credentials too closely. Low and behold, the wardens were convinced of its authenticity (despite misspelling "Southwark" Crown Court) and Moore walked free in March 2014.

Police kill money-stealing botnet that infected millions of PCs
Europol and police forces across Europe have shut down Ramnit, a botnet that infected up to three million computers world-wide. The virus, generally installed by email phishing attacks or rogue sites (please stop clicking on attachments, whoever your are) was mostly used by criminal hackers to steal banking info. If you were so foolish to click, the program gives hackers remote access to your Windows PC, letting them steal banking credentials, personal details and other info. The countries hit hardest were the US, India and Bangladesh.

Spyware tries to lure gamers through fake in-game voice apps (updated)
Malware targeting gamers usually tends to revolve around the games themselves, such as fake copies of a hot new shooter or deceptive in-game items. Well, it looks like these attackers are mixing up their strategy: Malwarebytes Labs has found spyware spoofing an in-game voice chat app. At first, it steers you to a fake website offering Razer's Comms software. If you're eager enough to click the Windows download link, you instead get a script that tries to harvest your logins and other sensitive info. A cursory glance suggests that it's (poorly) written by Russian cybercriminals renting their services.

The internet's governing body was hacked, too
The Sony Pictures hack is getting all of the attention right about now, but it turns out that another prominent organization recently was victim to a security breach as well. Last month, ICANN, the outfit that regulates the internet's domain names and IP addresses, fell prey to a phishing attack that tricked employees into giving out email login info. What'd the ne'er-do-wells get a hold of? Administrative access to all the files in the Centralized Zone Data System. Which, as The Register points out, granted the hackers access to unalterable generic zone files (what're needed to resolve domain names to IP addresses), and gifted them with contact information for, among others, some of the world's registry administrators. Passwords were stored as "salted cryptographic hashes," but ICANN deactivated them as a precaution anyway. The firm's wiki was breached too, but aside from public information, a members-only index page and one user's profile, no other private data was viewed.

Google says the best phishing scams have a 45-percent success rate
Conceptually, phishing scams sound easy to see through: a fake webpage with the wrong URL that doesn't look quite right -- who's going to fall for that? Quite a few people, apparently. According to a new Google study, the most successful phishing websites will capture data from 45-percent of its visitors. The least successful scams only scored information from three percent of its visitors, but when crooks are sending out phishing emails by the millions, that still adds up. The study found that the majority of the hijackers operate out of China, the Ivory Coast, Malaysia, Nigeria and South Africa, and that they work quick: 20-percent of accounts were compromised within 30 minutes of having information phished.

The FBI faked a news website to catch a bomb threat suspect
The DEA isn't the only US law enforcement agency using impersonation on the web to catch suspects, it seems. The American Civil Liberties Union's Christopher Soghoian has noticed documents showing that the FBI created a fake, spyware-laden version of the Seattle Times' website to catch a teen bomb threat suspect in 2007. When the teen clicked the link to check out an equally fake Associated Press story, the hidden software installed itself and sent both the target computer's location and its internet address to officers. As you might gather, both civil liberty advocates and media outlets are furious -- the FBI effectively conducted a phishing attack, and neither the AP nor the Times appreciate having their names and likenesses used without permission.
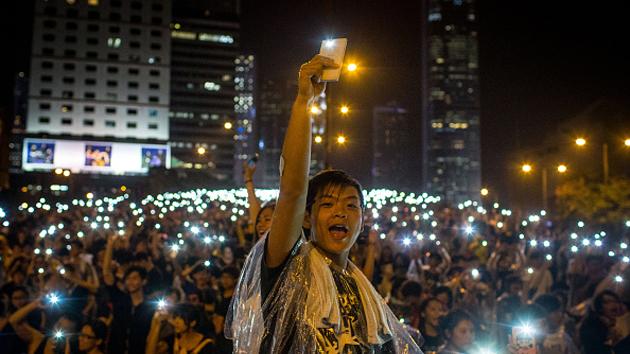
New spyware targets Hong Kong protesters' phones
Hong Kong's pro-democracy protesters have more to worry about than they thought -- someone is gunning after their phones, too. Lacoon Mobile Security says it has detected new spyware, Xsser, that tries to trick WhatsApp users on Android and iOS by posing as a coordination tool for the Occupy Central movement. Anyone who falls for the ploy grants access to virtually all of their sensitive info, including contacts, call logs and instant messaging archives. The code is unusually sophisticated, to boot; it's a rare instance of a cross-platform mobile attack, and it updates itself over time.

Watch out: eBay vulnerability leads to phishing log-in page
Thinking about picking up a used iPhone on eBay? Shop carefully, friends: it's apparently phishing season. The BBC is reporting some auction listings are redirecting to counterfeit eBay login pages -- fronts for phishing scams designed to steal customer usernames and credit card information. The good news is that eBay isn't technically hacked. The online marketplace allows sellers to use scripting to gussy up item listings. Cross-site scripting is generally not allowed, but these scammers are doing it anyway.

PSA: Twitch chat links are phishing for Steam logins
Some Twitch users are experiencing a number of phishing attempts within the video game broadcast service's chat windows. Twitch's support team on Twitter advised that viewers avoid clicking the "csgoprize" link that may appear in stream chats, as it is "a phishing attempt to install malware and compromise your Steam account." Twitch did not disclose how widespread the issue is. The support team said it will "work to block that link," but that variants of the phishing attempt may sprout up in the future. It added that "in general, you should be wary of any links in chat." As for ways broadcasters can prevent further issues, they can enable a "Block Hyperlinks" option within Twitch's Channels and Videos settings to prevent viewers from adding their corrupt links to their stream's chat. [Image: Twitch]

5 million Gmail passwords published, but don't panic
You might need to change your email password in the very near future. A member at a Russian Bitcoin forum has posted almost 5 million Gmail passwords, around 60 percent of which are reportedly still working. It's not clear how the poster managed to scoop up all this account info, but Google tells Cnews that it comes from a long stretch of hacking and phishing attempts that stole data from individual users. Gmail's servers weren't breached, the search giant says, and much of what's there is old. That's somewhat comforting, but you may want to check if your account is one of the unfortunate targets -- you don't want to give thieves easy access to your most sensitive info.

Google now rejects scam email that tricks you using non-Latin characters
Google did a favor for Gmail users worldwide when it added support for non-Latin characters in email addresses. However, it also opened up a can of worms -- scammers can write from addresses that seem legitimate, but are really using non-native letters to (potentially) fool you into trusting a message's contents. Thankfully, the crew in Mountain View is already aware of the threat. Gmail now tosses out email with odd combinations of letters that are likely to represent phishing attempts, reducing the chances that you'll hand your account details to a "bɑnk" instead of your actual bank. The filtering relies on a Unicode standard, too, so you'll know the exact criteria Google is using. Other email providers will have to follow suit for the measure to really hit data thieves where it hurts, but this represents an important first step.

Spying malware leaves countries' energy grids open to attack
Cyberwarfare campaigns against Western energy grids aren't just the stuff of action movies these days -- they're very, very real. Symantec has discovered a likely state-sponsored hacking group, nicknamed Dragonfly, that has been using phishing sites and trojans to compromise energy suppliers in the US and several other countries. Unlike targeted, destruction-focused malware like Stuxnet, this appears to be a broader spying effort bent on collecting information about national infrastructure. However, it still creates a back door that leaves companies vulnerable to full-fledged attacks if they don't spot the intrusions; it wouldn't take much to create real problems.

PSA: Fake EA Sports Instagram account phishing for Xbox, Origin logins
It's World Cup season; reigning champions Spain lost in spectacular fashion and FIFA soccer fans may be interested in rectifying that loss to Chile in FIFA 14's Ultimate Team World Cup mode. Unfortunately, Instagram accounts posing as official EA Sports channels are popping up during this period of piqued interest, posting tempting offers for free in-game currency in order to obtain players' Xbox Live and Origin account details.








