attack
Latest

iPhone users in 92 countries received a spyware attack warning from Apple
Apple notified individuals in 92 countries of possible mercenary spyware attacks on their systems.

Xfinity breach may have affected as many as 35.8 million customers
Xfinity says it suffered a data breach in October with attackers likely obtaining usernames, hashed passwords and potentially other sensitive information.

Vevo says an 'unauthorized source' vandalized Drake, Lil Nas X and other YouTube channels
If you were trying to watch Taylor Swift, Drake, The Weeknd and other artists on YouTube this morning, you may not have seen what you expected.

CD Projekt Red says it was hacked but won't pay the ransom
CD Projekt Red tweeted that it has been hacked and must pay a ransom or code from games like Cyberpunk 2077 and an “unreleased version of Witcher 3” will be revealed.

A ransomware attack has shut down Baltimore County public schools
The city's government was affected by a similar attack last year.

Tesla worked with the FBI to block a million dollar ransomware attack
Tesla avoided a ransomware attack with the help of an honest employee and the FBI.

Intel's Tiger Lake processors will feature on-chip malware protections
Intel has a new way to defend against malware threats.
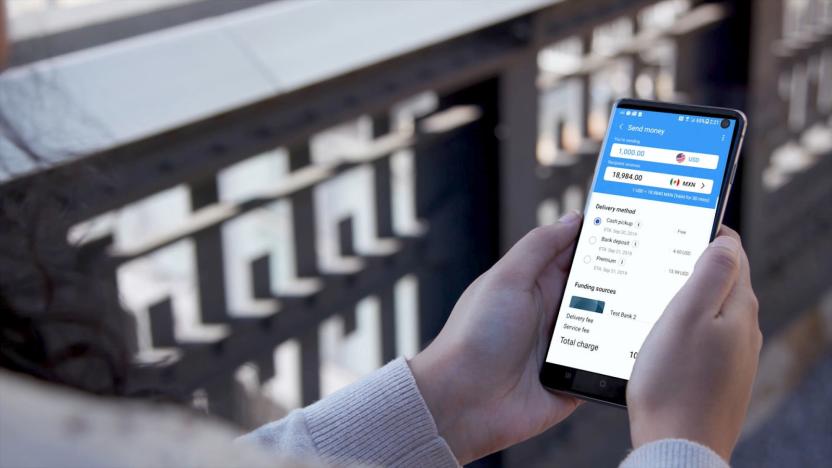
US Samsung Pay users can't send money internationally after Travelex hack (update)
Travelex's ransomware attack continues to affect people and businesses around the globe -- including those that might not consider themselves affiliated with the company in any way. Engadget can reveal that Samsung Pay's international money transfer service -- which relies on the Travelex platform -- has been suspended as a result of the issues faced by its partner.

The first in-the-wild BlueKeep cyberattack isn't as dangerous as feared
When word broke of the BlueKeep vulnerability in Windows, many feared a repeat of NotPetya and other widespread worms that have wreaked havoc. They might not have to worry quite so much, though. Kryptos Logic has discovered the first known in-the-wild BlueKeep exploit, and it isn't as vicious as feared. The initial attack from a "low-level actor" appears to have scanned the internet and infected vulnerable systems with a cryptocurrency miner, but little else. There are no data wipes, no automatic spreading or other signs of a worm in action.

Chrome for Android update protects against Spectre-like chip hacks
Last year, Chrome 67 for desktop introduced Site Isolation to protect users from Spectre-style security threats by making it harder for attackers to steal data from other websites. Now, Chrome 77 is bringing Site Isolation to Chrome on Android.

Apple tries to clear up Google's claims about iOS vulnerabilities
Apple has taken issue with Google's findings about exploit-laden websites injecting malicious code into iPhones. Last week, Google published a blog post describing how a handful of hacked websites had taken advantage of an iOS vulnerability. Today, Apple shared a rebuttal.

UN claims North Korea hacks stole $2 billion to fund its nuclear program
United Nations experts say they are formally investigating at least 35 instances of cyberattacks by North Korea in 17 countries, believed to be carried out in a bid to fund its nuclear program. According to a report seen by Associated Press, North Korea has acquired as much as $2 billion from increasingly sophisticated cyber activities against financial institutions and cryptocurrency exchanges.

Facebook unveils a 'one-strike' policy for live streaming violations
Facebook has unveiled a one-strike policy for live streaming violations in the wake of an extreme right terrorist attack in New Zealand, the company announced. It said users who violate community standards just a single time on Facebook Live could be banned from streaming for a set time, depending on the nature of the violation. "Our goal is to minimize risk of abuse on Live while enabling people to use Live in a positive way every day," wrote Integrity VP Guy Rosen.

Evidence mounts that Russian hackers are trying to disrupt the EU elections
Russian hackers are targeting government systems ahead of the EU parliament election, according to cybersecurity company FireEye. The firm says that two state-sponsored hacking groups -- APT28 (aka Fancy Bear) and Sandworm -- have been sending out authentic-looking phishing emails to officials in a bid to get hold of government information.

Google Photos flaw let attackers grab users' location data
Researchers have revealed a now-patched flaw that would allow hackers to track your location history using Google Photos. Ron Masas, from security company Imperva, explains in a blog post that Google Photos -- which was recently subject to an Android TV bug -- was vulnerable to browser-based timing attacks, which could leverage a photo's image data to approximate the time of a visit to a specific place or country.

A single ransomware creator made almost $6 million
The SamSam ransomware, which throttled the city government of Atlanta earlier this year, netted its creators more than $5.9 million in ransom payments, according to a comprehensive report by UK cybersecurity firm Sophos. The report, which details SamSam's activity since its launch in 2015, also reveals that a lone black hat hacker could've raked in the entire haul by themselves.
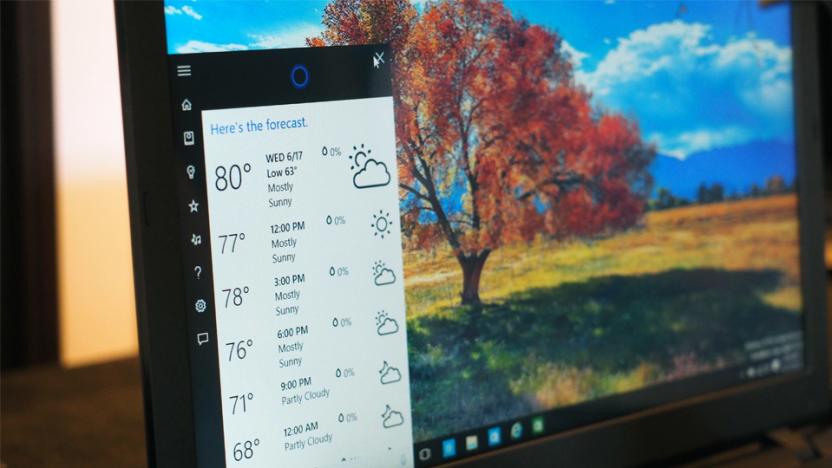
Cortana can be used to hack Windows 10 PCs
Cortana might be super helpful at keeping track of your shopping lists, but it turns out it's not so great at keeping your PC secure. Researchers from McAfee have discovered that by activating Cortana on a locked Windows 10 machine, you can trick it into opening up a contextual menu which can then be used for code execution. This could deploy malicious software, or even reset a Windows account password.

Major UK electrical retailer Dixons Carphone confirms it was hacked
One of Europe's largest electrical retailers has been the subject of a cyber attack that's compromised more than 5.9 million card records and as many as 1.2 million personal accounts. Dixons Carphone, the owner of Currys PC World and Dixons Travel stores, says that most of these cards have chip and pin protection and noted that the data accessed doesn't include PIN numbers, card verification values (CVV) or any authentication data "enabling cardholder identification or a purchase to be made." However, some 105,000 cards were from non-EU countries and do not have the chip and pin feature.

GitHub survives massive DDoS attack relatively unscathed
GitHub, a web-based code distribution and version control service, survived a massive denial of service attack on Wednesday. According to a report at Wired, a staggering 1.35 terabits per second (Tbps) of traffic hit the site at once. Within 10 minutes the company called for help from a DDoS mitigation service similar to Google's Project Shield, Akamai's Prolexic, which took over to filter and weed out malicious traffic packets. The attack, says Wired, ended after eight minutes. This may have been the largest DDoS attack ever; Wired notes the attack on domain name server Dyn in late 2016 reached 1.2 Tbps of traffic.

Nastier version of IoT botnet could brick your smart toaster
Two new versions of a nasty botnet called BrickerBot were spotted in the wild by researcher Pascal Geenens, who reported the latest attack for security firm Radware. Permanent denial-of-service botnets like these can infect poorly-protected IoT devices like smart toasters and web-enabled vibrators to bring down various connected web servers. These new BrickerBot iterations use scripts with even more commands and almost four times as many actual attacks as previous iterations to completely overwhelm their targets.






