cyberattack
Latest

Atlanta spends more than $2 million to recover from ransomware attack
Last month, Atlanta's city government was hit with a ransomware attack that caused courthouse documents and services like payment processing to become inaccessible. The ransom demand was approximately $51,000 but according to the city's Department of Procurement, Atlanta has spent much more than that on efforts to rectify the situation. It appears that firms Secureworks and Ernst & Young were paid $650,000 and $600,000, respectively, for emergency services while Edelman was paid $50,000 for crisis communication services. Overall, the funds seemingly applied to the ransomware attack response add up to approximately $2.7 million.
TaskRabbit returns following data breach it can't account for
Handyman-for-hire app TaskRabbit was the target of a data breach on Monday, resulting in both the app and website being taken offline while the company investigated the apparently intentional attack. Both are now back up and running, although the company has not said how the breach occurred or what information had been compromised.

UK reportedly preparing for a Russian-backed cyberattack
As tensions between the UK and Russia continue to mount, both sides appear to be bolstering themselves for retaliatory cyberattacks. The Times reports that Prime Minister Theresa May has been receiving intelligence risk assessments regarding a potential Russia-based cyberattack that might result in the release of embarrassing or compromising information about UK ministers, members of parliament and others. Unnamed security sources told The Times that in the case of an attack on UK infrastructure, British officials were prepared to launch their own cyberattack against Russia.

Global cyberattack targets 200,000 network switches (updated)
The past few days haven't been great for the internet's broader security. Iran's Communication and Information Technology Ministry has reported that it was a victim in a global cyberattack that compromised about 200,000 Cisco switches that hadn't yet received patches for exploits in the company's legacy Smart Install protocol. The attackers displayed a US flag on at least some screens, complete with a "don't mess with our elections" warning, but the attack wasn't focused on Iran -- only 3,500 switches fell to the exploit in the country. About 55,000 of the victim devices were in the US, IT Minister Mohammad Javad Azari Jahromi said, while 14,000 were in China. Other victims were located in Europe and India.
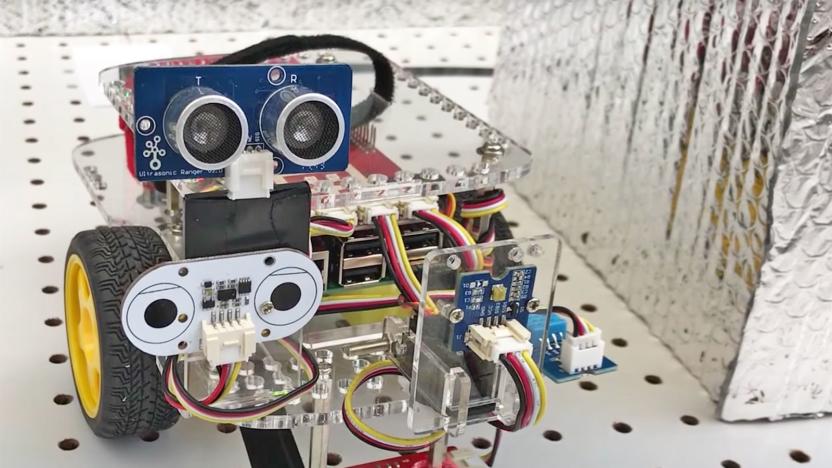
HoneyBot lures hackers to protect its fellow robots
As more and more industrial robots come online, there's an ever greater risk of hackers gaining access to them and taking control of their abilities. In some cases that could mean damage to a product or manufacturing flow, but in other cases, it could result in harm to nearby humans. That's why researchers at the Georgia Institute of Technology are developing a robot that can alert users to an ongoing breach and trick hackers into thinking they have control of their target.

DHS and FBI warn Russia is behind cyberattacks on US infrastructure
The Department of Homeland Security and the FBI released a report today detailing Russian efforts to hack into US government entities and infrastructure sectors, including energy, nuclear, commercial, water, aviation and critical manufacturing sectors. The agencies said the cyberattacks have been ongoing since at least March 2016 and their report described the attacks as "a multi-stage intrusion campaign by Russian government cyber actors."

US sanctions Russians for cyberattacks and election meddling
The US Department of the Treasury has instituted sanctions against five Russian entities and 19 individuals for their involvement in a number of cyberattacks and online efforts to interfere with the US presidential election. The sanctions prohibit US companies and individuals from conducting business with those named by the Treasury Department. "The Administration is confronting and countering malign Russian cyber activity, including their attempted interference in US elections, destructive cyberattacks and intrusions targeting critical infrastructure," Treasury Secretary Steve Mnuchin said in a statement. "These targeted sanctions are a part of a broader effort to address the ongoing nefarious attacks emanating from Russia. Treasury intends to impose additional CAATSA sanctions, informed by our intelligence community, to hold Russian government officials and oligarchs accountable for their destabilizing activities by severing their access to the US financial system."

Equifax finds another 2.4 million people affected by its data breach
Last month, reports surfaced that more information than previously thought may have been exposed in Equifax's massive data breach and today, Reuters reports, the has company confirmed it. Along with the 145.5 million individuals already reported to have been affected by the breach, Equifax says another 2.4 million were as well. However, their exposed data was limited to names and partial driver's license information. The company said that in most cases, home addresses as well as driver's license states, issue dates and expiration dates weren't included in the stolen data.

Russia hacked the Olympics and tried to pin it on North Korea
Now that the 2018 Winter Olympics are over, we're now learning who was responsible for hacking the games' systems... and the culprit won't surprise you at all. US intelligence officials speaking anonymously to the Washington Post claimed that spies at Russia's GRU agency had compromised up to 300 Olympics-related PCs as of early February, hacked South Korean routers in January and launched new malware on February 9th, the day the Olympics began. They even tried to make it look like North Korea was responsible by using North Korean internet addresses and "other tactics," according to the American sources.
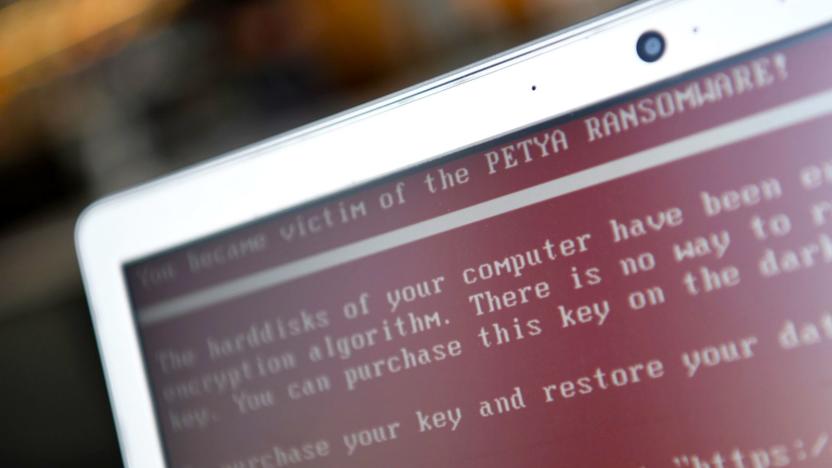
Russia denies UK claim it was behind NotPetya cyberattack
The UK government says that Russia is to blame for the destructive NotPetya cyberattack that scrambled major infrastructure around the world in June 2017, costing firms millions. Foreign Office minister Lord Ahmad said that while the attack masqueraded as a criminal enterprise, its purpose was "principally to disrupt" Russia's primary target, Ukraine, and that Russian military was "almost certainly" behind the attack.

Olympics officials confirm cyberattack during opening ceremony
Officials saw suspicious activity on Olympics systems during the 2018 winter games' opening ceremony, and now it's confirmed: it was a cyberattack. PyeongChang organizers have revealed that someone compromised services (including internet and TV) while athletes were on parade. Everything had been "resolved and recovered" by the 9th, spokesman Sung Baik-you said. He added that they knew the cause of the attack, but were "not going to reveal the source" after talking to the International Olympics Committee.

What Trump means when he talks nukes at the State of the Union
President Donald Trump is expected to cover five main topics in his first State of the Union address tonight, including the economy, immigration, infrastructure and trade. The fifth topic, national security, will put the spotlight on North Korea and the erratic, ad hominem nuclear standoff between North Korean leader Kim Jong-un and Trump himself. The tension of this relationship has spilled over to Twitter, where Trump has lobbed insults and threats at Kim over the past year. Trump called Kim "little Rocket Man" and declared the US' "nuclear button" was "much bigger and more powerful" than Kim's. In August, Trump promised "fire and fury" if North Korea didn't stop testing nuclear weapons, and Kim later called Trump a "mentally deranged dotard." Meanwhile, North Korea carried out more than a dozen nuclear tests throughout 2017, including launching intercontinental ballistic missiles theoretically capable of striking the US mainland. Its most recent ICBM test was in November.

Alphabet enters the cybersecurity business with Chronicle
Google parent company Alphabet has a new business and it's all about cybersecurity. Chronicle is an independent business under the Alphabet umbrella and it's aimed at helping companies find, track and stop cyber attacks. With two branches -- a cybersecurity and analytics platform, as well as a malware intelligence service called VirusTotal -- Chronicle will use its massive processing power and data storage capabilities to assist businesses in retrieving information more quickly than they can on their own as well as spot patterns based on years of data. "Add in some machine learning and better search capabilities, and we think we'll be able to help organizations see their full security picture in much higher fidelity than they currently can," said Chronicle CEO Stephen Gillett in a blog post.

Obama-era plans to ‘zap’ Russian trolls collapsed under Trump
Before departing office, Barack Obama ordered US spy agencies to plan operations to combat Russian cyberthreats, according to the The Washington Post. But, more than a year into Trump's tenure, his administration remains reluctant to pursue those counter-measures, claims the report.

Facebook and Microsoft disabled slew of North Korean cyber threats
If you ask the White House, North Korea's WannaCry attack was just the tip of the iceberg. Homeland security adviser Tom Bossert reported that Facebook and Microsoft disabled a range of North Korean online threats in the past week. Facebook removed accounts and "stopped the operational execution" of ongoing attacks, while Microsoft patched existing attacks that went beyond WannaCry. Details of just what those attacks were aren't available.

US government names North Korea as the source of WannaCry
Donald Trump's homeland security adviser, Tom Bossert, said in a Wall Street Journal op-ed that "after careful investigation, the U.S. today publicly attributes the massive "WannaCry" cyberattack to North Korea." Coming during increasing tensions between the two countries over nuclear threats and Twitter outbursts, Bossert said this attribution is based on evidence and agrees with the findings from the UK and Microsoft.

Mirai botnet creators plead guilty to charges over 2016 attack
The individuals behind the Mirai botnet that caused nationwide internet outages in October of last year have pleaded guilty to federal charges, ZDNet reports. Paras Jha, Josiah White and Dalton Norman were indicted by a court in Alaska earlier this month and have pleaded guilty to charges that carry a sentence of up to five years in prison.

Uber paid off a 20-year-old Florida man to destroy hacked data
More details are coming to light about Uber's huge data breach. Reuters is reporting that a 20-year-old Florida man was behind the 2016 extortion-oriented cyberattack and was paid through the firm's bug bounty program. We know that the individual, whose identity Uber refuses to disclose, received $100,000 for destroying the info, which exposed the personal data of roughly 57 million customers and drivers. The ride-hailing firm then kept quiet about the breach for more than a year. You can bet Congress and the five states investigating Uber will be paying close attention to any new nuggets of info.

Uber hid data breach that exposed info for 57 million users
Uber's new CEO Dara Khosrowshahi has inherited yet another scandal from Travis Kalanick. The ridesharing firm has revealed to Bloomberg that it hid an extortion-oriented cyberattack which exposed the personal info for roughly 57 million customers and drivers in October 2016, including names, email addresses and phone numbers. Instead of reporting the hack to the government and users, it paid hackers $100,000 to delete the info and keep quiet for more than a year.

Kaspersky says it briefly possessed classified NSA files
Earlier this month, reports surfaced that classified NSA documents detailing how US agencies defend their cyber networks and how they breach foreign ones were stolen by Russian hackers in 2015. Those reports noted that the files were spotted through Kaspersky security software used by an NSA contractor who had saved the classified documents on a home computer. Well, Kaspersky has now provided some more information about the incident and it has acknowledged that it did in fact have classified NSA materials in its possession, the Associated Press reports.





