spyware
Latest

Hacking Team's clients are a who's who of despotic regimes
We now know that Hacking Team, a company responsible for building some of the more notorious surveillance software in the world, was also doing business with some of the most notorious regimes in the world. How do we know this? Well a treasure trove of leaked documents found their way online. Thanks internet! Wondering just what actors the company was working with and how bad they were? Well check we've got a handy breakdown for you below.

Now you can explore Hacking Team's world of selling spyware
Plenty of ink has already been spilled about the Hacking Team's spectacular security meltdown, but why should the press have all the fun? WikiLeaks posted a searchable archive of over a million emails from the Italian IT firm last night, which means armchair sleuths can take a peek into the cloak-and-dagger world of selling spyware to governments with just a few clicks. Now obviously not everything contained in this hefty database is damning; lots of it just chronicles the day-to-day operations of a lucrative business. Every once in a while, you'll find something almost shocking in its mundanity, like this corporate email blast about restaurants in London that wound up in Hacking Team COO Giancarlo Russo's inbox. Still, there are plenty of juicier tidbits waiting for you if you keep a few keywords in mind.

Malware used Foxconn digital certificate to spy on Iran nuclear talks
Russian security firm Kaspersky Lab has looked deeper into the malware that attacked its network and found that it used a digital certificate stolen from Foxconn. That's the same Taiwanese company frequently associated with big names in electronics, since its factories manufacture everything from iPhones and iPads to PS4s and Xbox Ones. The malware, known as Duqu 2.0 due to its shared programming with an older spyware called Duqu, also infected the networks of hotels where the UN Security Council held meetings about Iran's nuclear development. Duqu 1.0 and its predecessor, the Stuxnet worm, also redirected traffic through digital certificates stolen from Taiwanese companies, presumably to make it appear like the attacks came from China.

State-backed spyware targets antivirus maker, Iranian nuclear talks
The threat posed by state-sponsored malware might be even larger than first thought. Antivirus developer Kaspersky Lab says it discovered an attack on its network by allegedly government-made spyware that appears to be an upgraded version of Duqu, the Stuxnet-based worm used by Israel and the US to derail Iran's nuclear efforts. This "Duqu 2.0" not only tried to obtain details about Kaspersky's investigations and detection abilities, but remained remarkably stealthy. Pre-release software was necessary to catch it, and there were attempts to throw researchers off the scent by suggesting that China or Eastern Europe was to blame.

The NSA tried to use app stores to send malware to targets
It shouldn't come as a surprise to hear that the NSA worked on iOS and Android malware meant to capture information from a target's phone, but actually getting the software onto phones? That's tricky. To help solve that problem, the NSA (and the rest of the Five Eyes intelligence community) attempted to hijack data being sent to and from app stores like those run by Samsung and Google. According to a document leaked by Edward Snowden, obtained by The Intercept and published by the CBC, it was mostly in search of a way to implant secret surveillance payloads into those data connections in hopes of identifying an Arab Spring in action in other countries.

The DEA's using powerful spyware for surveillance too
The war on drugs has a surprising soldier amongst its ranks: Italian spying software. As Motherboard's sources tell it, the Drug Enforcement Administration's dropped $2.4 million on surveillance tools that are capable of intercepting phone calls, texts, social media messages, and can even take hold of someone's webcam and microphone. Oh, Remote Control System (as its officially called) can grab passwords, too. Almost sounds like a video game, right? The Hacking Team-developed software (the outfit behind Ethiopian cyberattacks on US journalists), can be installed on the sly and grants access to data that may very well be encrypted or otherwise inaccessible by other means. It comes hot on the heels of news that the DEA's been collecting phonecall metadata for an awfully lot longer than the NSA, too. Naturally, no one on either side of the story has been eager to open up to Motherboard, and presumably journalists in general.

Cops gave a malware-laden drive to a lawyer for whistleblowers
Arkansas' Fort Smith Police Department may be responsible for some particularly sinister digital tricks, if you ask one lawyer. An attorney representing whistleblowers in a police corruption scandal says that the Department sent him a hard drive laden with trojans when he requested documents. Given that the rogue files were found in a folder specific to the court order (that is, they were added after the court order was issued), it looks as if someone in the FSPD wanted to hijack the lawyer's computer and sabotage his case. And that's not the only suspicious behavior, either -- the city reportedly deleted email accounts and messages that it knew it was supposed to keep.

Watchdog says spyware violates human rights guidelines
If you think that commercial software designed to spy on computers is problematic, you're not alone. The Organization for Economic Cooperation and Development's UK contact has determined that Gamma International's approach to selling its FinFisher spyware violates human rights guidelines. The developer not only doesn't have a human rights policy, but doesn't investigate clients for the possibility of abuse -- there's little stopping it from selling FinFisher to an oppressive government. The contact couldn't confirm that Gamma sold its software to Bahrain, which used the surveillance tool to target the political activists who prompted the investigation (shown here). However, the OECD isn't shy about pressing for change. It wants Gamma to take evidence of abuse and government advice into account whenever it sells software, and to cooperate when there are signs that someone is using FinFisher for nefarious purposes.

Chrome adds more warnings to prevent you downloading malware
Google's already making sure you don't download malware, and now it's expanding its Safe Browsing initiative. In addition to preventative warnings prior to downloading, the Chrome browser will now throw a red flag (pictured after the break) before visiting a site that may encourage you to install any malicious software. Search listings are getting marks for sites that might contain nefarious programs as well, and Mountain View says that it's actively disabling Google Ads that "lead to sites with unwanted software." The search giant is urging site owners to install its Webmaster Tools to help keep on top of any possible issues with a site pushing bad software to visitors, and says this'll aid with the resolution process should that happen. Again, it's Google working to keep its "don't be evil" reputation in line and making the internet a safer place for everyone. After all, even the most web savvy among us have probably downloaded malware before at some point. [Image credit: Associated Press]

New Lenovo PCs shipped with factory-installed adware
Buy a new Lenovo computer recently? Well, it looks like it could be infected with some factory-installed adware. Users on the official Lenovo forums started noticing that search results were being injected with sponsored links (like what happens when a machine is infected with typical adware or spyware) as far back as last September, and some even report that sites including Kelley Blue Book and JetBlue wouldn't render properly at all. This apparently isn't the only problem, however. As Facebook engineer Mike Shaver recently discovered, the program at fault, Superfish, appears to install a man-in-the-middle certificate that allows outside parties to take a peek at secure websites you might be visiting, too. Like your bank's, for example.

Spyware tries to lure gamers through fake in-game voice apps (updated)
Malware targeting gamers usually tends to revolve around the games themselves, such as fake copies of a hot new shooter or deceptive in-game items. Well, it looks like these attackers are mixing up their strategy: Malwarebytes Labs has found spyware spoofing an in-game voice chat app. At first, it steers you to a fake website offering Razer's Comms software. If you're eager enough to click the Windows download link, you instead get a script that tries to harvest your logins and other sensitive info. A cursory glance suggests that it's (poorly) written by Russian cybercriminals renting their services.

Seller of StealthGenie spyware app gets fined $500,000
A US District Judge in Virginia has ordered the man responsible for selling and distributing StealthGenie, an application used to spy on people, to pay a $500,000 fine and hand over the software's source code to the authorities. Hammad Akbar, who is originally from Denmark, last week pleaded guilty to the charges of a "sale of an interception device and the advertising of a known interception device," in what the Department of Justice is calling the first-ever criminal conviction of its kind. Akbar admitted that StealthGenie could take on many spying tasks once installed on an iOS, Android or BlackBerry smartphone, such as providing access to email, text messages and pictures, as well as intercepting any incoming and outgoing phone calls.

US warns about spyware that many believe it wrote
Want to see a classic example of irony? Head to the US Computer Emergency Readiness Team (CERT) website. The government security group has issued a public warning about Regin... you know, the extra-sophisticated malware that many suspect the US wrote to spy on telecom networks. It's more than a little amusing to see one agency warn about a problem the other may have created, although it raises a few questions when there haven't been similarly direct warnings for (allegedly) state-created attacks like Stuxnet and Duqu. Is it evidence that the US wasn't involved, or that Regin is out of control? An attempt to throw people off the scent? Or something else?

Researchers link carrier-focused malware to US and UK spy agencies
Symantec said that the recently detailed Regin spyware looked like it was created for government surveillance, and there's now some strong support for that claim. Both Kaspersky Lab and Wired understand that the super-sophisticated malware was used to infiltrate both Belgian carrier Belgacom and cryptographer Jean-Jacques Quisquater. Given that the NSA and Britain's GCHQ have been linked to these malware attacks, it's easy to connect the dots -- from all indications, one or both spy agencies used Regin to snoop on these targets. There are also hints that it may have been used to hack into the European Commission back in 2011. The Commission's director of security couldn't tell Wired if the malware in that incident was the same, but the code involved was built from a "series of elements" that worked together, like Regin does.

The FBI faked a news website to catch a bomb threat suspect
The DEA isn't the only US law enforcement agency using impersonation on the web to catch suspects, it seems. The American Civil Liberties Union's Christopher Soghoian has noticed documents showing that the FBI created a fake, spyware-laden version of the Seattle Times' website to catch a teen bomb threat suspect in 2007. When the teen clicked the link to check out an equally fake Associated Press story, the hidden software installed itself and sent both the target computer's location and its internet address to officers. As you might gather, both civil liberty advocates and media outlets are furious -- the FBI effectively conducted a phishing attack, and neither the AP nor the Times appreciate having their names and likenesses used without permission.

EFF: Security software distributed by cops is actually spyware in disguise
Various schools, libraries and ordinary American families might have been using a "security" software called ComputerCOP for years. After all, they probably got their copy from cops, attorney's offices or other branches of law enforcement, which tout it as a way to protect children online. Unfortunately, ComputerCOP isn't the digital protector children need -- according to tests conducted by the Electronic Frontier Foundation, it's actually a key-logging spyware that uploads unencrypted data to the software's servers. In other words, it uploads bank and email log-ins, social security numbers, among other sensitive data that can be easily intercepted and read by identity thieves, credit card hackers or even child predators.
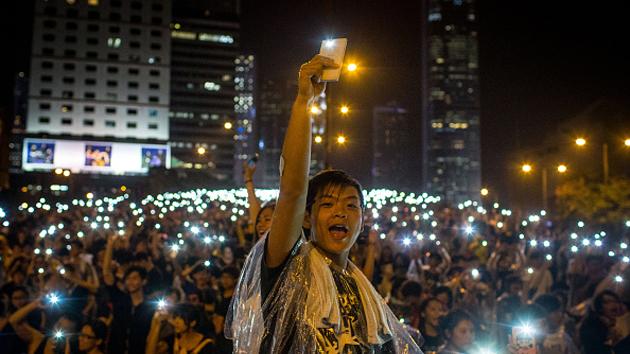
New spyware targets Hong Kong protesters' phones
Hong Kong's pro-democracy protesters have more to worry about than they thought -- someone is gunning after their phones, too. Lacoon Mobile Security says it has detected new spyware, Xsser, that tries to trick WhatsApp users on Android and iOS by posing as a coordination tool for the Occupy Central movement. Anyone who falls for the ploy grants access to virtually all of their sensitive info, including contacts, call logs and instant messaging archives. The code is unusually sophisticated, to boot; it's a rare instance of a cross-platform mobile attack, and it updates itself over time.

Crackdown on spying apps leads to StealthGenie CEO's arrest
Apparently, the US government is now on a mission to bring down mobile applications offering spyware services -- which, for a variety of well-documented reasons, simply seems kind of ironic. Controversy aside though, the Department of Justice revealed today that Hammad Akbar, CEO of StealthGenie, had been arrested in Los Angeles and charged with conspiracy, advertisement of a known interception device, advertising a device as a surreptitious interception device and sale of such a device. StealthGenie, which had been available on iOS, Android and BlackBerry, was known for providing an app capable of monitoring someone's calls, texts and photos, as well as tracking their location and more. StealthGenie wasn't shy about doing that either; a quick glance at a StealthGenie promotional video, found after the break, sums up the ideals behind the application and the consumers it targeted.

Powerful spyware apps let the government control everything on your phone
There's been a lot written over the past year about government spying, but not so much about how governments spy. It's easy to forget that there's an industry thriving underneath that controversy. In 2011 WikiLeaks founder Julian Assange released a series of documents it called the Spy Files -- a comprehensive database of surveillance products and companies who market their services specifically to government agencies. Companies like Hacking Team specialize in advanced spyware, gifting their customers with the ability to exercise total control over a target's device while remaining completely invisible. A group of researchers recently tracked down and reverse engineered Hacking Team's RCS (Remote Control System) tool to see just what these corporate spyware firms are capable of. The answer, is quite a lot.

Russia denies it slipped world leaders bugged USB disks and cables
After becoming embroiled in the NSA brouhaha by giving Edward Snowden sanctuary, Russia is again on the defensive after reports suggested it may have slipped G20 leaders compromised devices. A pair of Italian newspapers said that German security experts discovered "USB sticks and recharge cables (that) are suitable for undercover detection of computer data and mobile phones," after being alerted by the head of the European council. The Kremlin denied the allegations, calling them "an attempt to switch attention from the (spying) problems that really exist." Further tests are underway, and if the results are confirmed, may show that Russia has a ways to go to catch up to the NSA's more sophisticated eavesdropping.







