infosec
Latest

Let’s stop pretending Facebook cares
The really great thing to come out of the Cambridge Analytica scandal is that Facebook will now start doing that thing we were previously assured at every turn they were doing all along. And all it took was everyone finding out about the harvesting and sale of everyone's data to right-wing zealots like Steve Bannon for political power. Not Facebook finding out because they already knew. For years. In fact, Facebook knew it so well, the company legally threatened Observer and NYT to prevent their reporting on it, to keep everyone else from finding out.

Twitter is the latest tech giant losing its security chief
A Twitter spokesperson has confirmed that the company's chief information security officer Michael Coates, who joined in 2015, is leaving. As first reported by the The Verge, he announced the move internally three weeks ago and is leaving to start his own company.

No, postcards won’t solve our Russian interference problem
We just learned all the ways Russian propaganda agents fooled American social media companies, thanks to the recent indictments of Russian nationals by Team Mueller. After years of these companies forcing us to adhere to their contrived "community safety" policies and made-up rules to police our identities (which they swore was for our own good), their failures are rather spectacular.
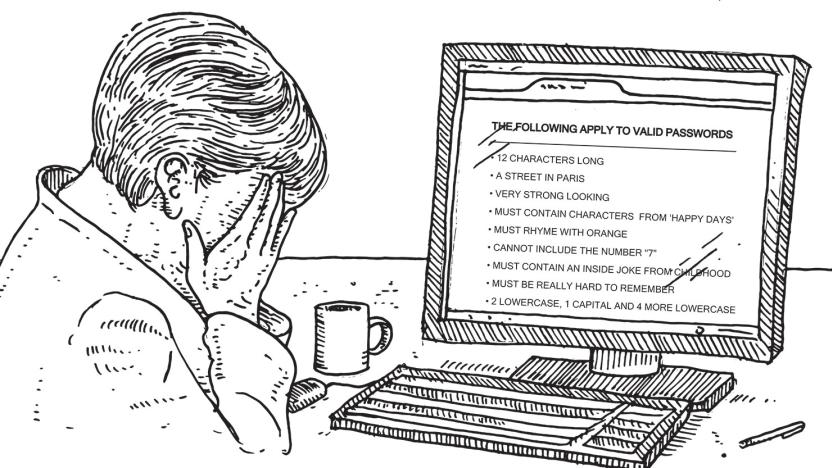
How security became more important than convenience
Since the dawn of infosec, the belief that we users are a group of dullard cattle who blindly trade our own security for convenience at every turn has been trumpeted by the stewards of IT and the infosec-arrogant, while bolstered by old research. Not anymore, says a new in-depth study from IBM on consumers' relationships with biometrics, authentication and the future of identity. If they have a choice, consumers now prefer taking extra security steps over using "123456" as a password.

Facebook patents tech to determine social class
We've got great news this week for nation-state employees tasked with using social media to spark a class war in previously stable democracies! Facebook is patenting technology to decide if its users are upper, middle or working class -- without even using the usual marker for social class: an individual's income (the patent considers this a benefit).

Strava’s fitness heatmaps are a 'potential catastrophe'
The 2018 cybersecurity race to the bottom is off to an exciting start. First out of the gate is Strava — now widely known as the "social network for athletes" -- and its reckless data-visualization "heat map" gimmick that revealed details of secret military bases around the world. It was the kind of incident deserving of a plot line in a ridiculous Hollywood drama. And yet, here we are, with Twitter and the whole world discussing and dissecting fitness routes of soldiers and agents in sensitive locations, such as American bases in Afghanistan and Syria, a possible secret CIA base in Somalia, military facilities in war zones and much more.

Voting-machine makers are already worried about Defcon
Last year, Defcon's Voting Village made headlines for uncovering massive security issues in America's electronic voting machines. Unsurprisingly, voting-machine makers are working to prevent a repeat performance at this year's show. According to Voting Village organizers, they're having a tough time getting their hands on machines for white-hat hackers to test at the next Defcon event in Las Vegas (held in August). That's because voting-machine makers are scrambling to get the machines off eBay and keep them out of the hands of the "good guy" hackers.

Facebook's fake war on fake news
It's hard watching Facebook struggle. Like how for the past two years it's alternated between looking like it's doing something about fake news, and actually doing something about fake news. The company's latest stab at the problem is saying it will change what people see in their News Feeds. The goal is to show users fewer posts from companies or brands, and more shares (or posts) from friends; in particular, ones its algorithm thinks will get you excited.

2017’s biggest cybersecurity facepalms
2017 was a year like no other for cybersecurity. It was the year we found out the horrid truths at Uber and Equifax, and border security took our passwords. A year of WannaCry and Kaspersky, VPNs and blockchains going mainstream, health care hacking, Russian hackers, WikiLeaks playing for Putin's team, and hacking back. In 2017 we learned that cybersecurity is a Lovecraftian game in which you trade sanity for information. Let's review the year that was (and hopefully will never be again).

Uber, but for toxic techbro culture
Some companies are just born with an infinite number of chances to keep doing everything wrong and yet somehow seem immune to the consequences. Uber is one of those companies. Uber's latest scandal -- a fat hack and its dirty coverup -- is just one in a long line of Uber-riffic examples on just how far a certain kind of privilege gets you.

Intel's latest Core processors have serious security flaws
Intel has confirmed previous reports that its recent PC, internet of things and server chips are vulnerable to remote hacking. The problem is with the onboard "Management Engine," which has multiple holes that could let remote attackers run malicious software, get privileged access and take over computers. The vulnerability affects sixth, seventh and eighth generation Core chips (Skylake, Kaby Lake and Kaby Lake R), along with Pentium, Celeron, Atom and multiple Xeon chips.

The naked truth about Facebook’s revenge porn tool
Facebook has announced it's trialling a tool in Australia to fight revenge porn on its platform, one that requires victims to send the company a copy of the violating images. Amazingly, this is true, and not a Clickhole story. It's the kind of thing that makes you wonder if there are human people at Facebook, and do they even understand what words mean? Because as we unravel the details of this tool -- totally not conceived by actual robots or a company with a zero percent trust rating among users -- we realize it's a very confusing tool indeed.

Why Equifax’s error wasn’t hiring someone with a music degree
In the wake of the Equifax breach, a significant number of people lost their minds this week upon discovering that one of its newly deposed security executives has a degree in music composition. Despite 14 years of experience as a security professional in other companies, Susan Mauldin was mocked and dragged online for being a "diversity hire" who is "unqualified" for the job.

How hateful alt-right trolls hijacked your timeline
You don't need to get attacked by a pro-Trump troll-bot horde to know that social media is a battleground for propaganda farms. It's pretty obvious, and miles of speculative digital ink has been spilled saying as much. An Oxford study this week is getting more of that ink spilled, confirming what we already knew. But no one's spelled out what it actually means. The Computational Propaganda Research Project at the Oxford Internet Institute, University of Oxford, certainly tried. That's the paper everyone's talking about this week, by the way. It looked at case studies from researchers in nine countries, interviewed 65 experts, and analyzed tens of millions of posts across seven different social media platforms during moments of heightened government propaganda activity: elections, political crises and national-security incidents.

Hacking Team is back
When you call yourself "Hacking Team," you're borrowing a legacy of persecution and suffering at the hands of legal authorities. The same kind that drove Aaron Swartz to become the most famous hacker suicide of our era. You're effectively wrapping yourself in a mantle bled into by the skins of coders and crackers who are considered criminals by wider society -- regardless of innocence. You've grafted your brandished title -- "Hacking Team" -- onto the backs of those living under the oppressive fear of being rounded up, stripped of rights, and imprisoned for vague, state-defined crimes.

The hot new cyberattack that's sweeping the nation
On Tuesday, a powerful and terrifying new cyberattackworm emerged in Ukraine, quickly spreading to the Russian Federation and other countries no one cared enough to report on because they weren't the US. It was hard to tell which infection was worse: The cyberattack itself or the race to write and publish something (anything!) about it, framing it just like the last "massive" cyberattack explosion to hit the whole world.
Oliver Stone's unhealthy treatment of hacking in Hollywood
What's so compelling about Oliver Stone's recent four-part interview series with Vladimir Putin is probably not what the multi-Oscar-winning director intended. It's the same thing that makes his Edward Snowden biopic its own sort of cipher after the fact. Both have inadvertently — and strangely, by their own design — upset the already shaky foundations of toxic hero worship in the era of hackers, hacktivism and cyber-espionage.

Now doctors need to be hackers, too
As far as anyone knows, there hasn't been a real-life hack attack on someone's pacemaker. Which is surprising. Security researchers have shown us that it's a very real possibility. Even the FTC has been urging connected-medical-device makers to adopt security best practices, with multiple 2017 reports stressing the issue.

Trump’s cybersecurity order delivers nothing but more surveillance
Remember that cybersecurity executive order we anticipated from the Trump administration, which seemed to quietly disappear in January? The already-delayed deadline for Trump's EO on "the cyber" and his promise to create a cyber-review team passed last month. Many were wondering if it would fade off into oblivion like a tyrant's hairline -- or show up suddenly to drop cyber-bombs on someone's vacant cyber-tarmac.

The enduring myth of the hacker boy-band
Last week, Wired magazine published a sprawling feature on a group of young hackers the magazine claimed would "make us or break us" with their "exceptional talent." The article fawningly profiled each member of a group of Northeastern University college students who would "soon dominate technology -- and shape our future."


