lawenforcement
Latest

Judge orders woman to unlock iPhone with her fingerprint
It's still not perfectly clear whether or not law enforcement can force you to unlock your phone with your fingerprint, but an LA court isn't waiting to find out: for the first time in a federal case, a judge has ordered a person to unlock her smartphone using her digits. The FBI obtained a warrant requiring that identity theft suspect Paytsar Bkhchadzhyan unlock her iPhone through Touch ID just 45 minutes after her arrest. While it's not certain what the FBI was looking for, Bkhchadzhyan eventually pleaded no contest to the charge.

Paris police want drones to watch over crowds
Paris' police force is understandably anxious about crowd security as of late, and it's turning to technology in a bid to track threats hiding in those groups. It's planning to buy hexacopter drones that would be used for close crowd surveillance. The machines will have to meet very specific criteria: they'll have to clearly spot a license plate from 50m (164ft) away, fly at altitudes of 100m (328ft), require no more than 5 days of training and use encrypted connections to avoid hacks. In essence, they have to serve as an extra set of eyes that law enforcement can use without a moment's hesitation.

FBI leans on forensic software maker to crack terrorist iPhone
When the Department of Justice and FBI said they'd found another way to infiltrate San Bernardino terrorist Syed Rizwan Farook's iPhone 5c without asking Apple to weaken its security, they raised a big question: just who was this "third party" they were talking about? We might have a good idea after today. Israel's Yedioth Ahronoth claims that the FBI is getting help from CelleBrite, an Israeli firm that specializes in phone-oriented forensic software, to extract data from Farook's phone. If the company manages to crack the contents of the device, it won't have any reason to pester Apple... about this particular iPhone, anyway.
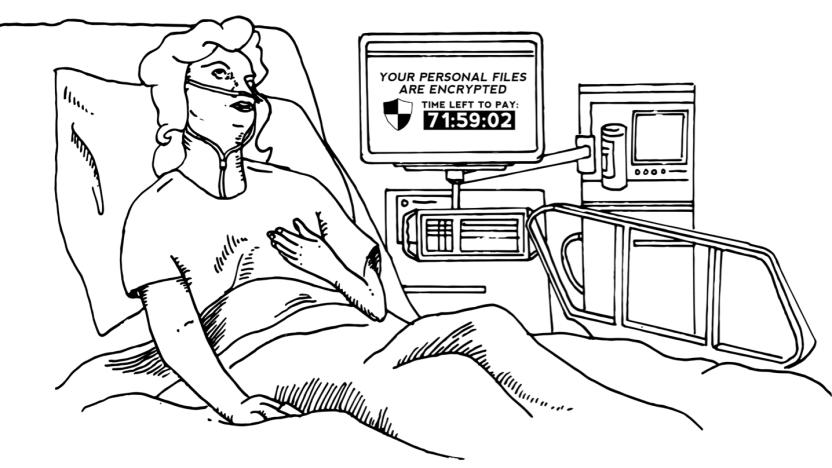
Hospital ransomware: A chilling wake-up call
If you had a loved one in the Hollywood Presbyterian Medical Center during its recent ransomware siege, would you be mad at the digital extortionists or the hospital? For me, the answer would be both. Hollywood Presbyterian declared a state of emergency over the ransomware on February 5th. The hospital issued a statement to press Wednesday evening on the 17th saying, "HPMC has restored its electronic medical record system ("EMR") on Monday, February 15th." The hospital isn't saying exactly when it paid the ransom, but it looks like they waited at least a week to end the file-hostage situation. Hollywood Presbyterian said its payment was 40 bitcoin, around $17K (not the 9K in bitcoin / $3.6 million initially reported).

FBI Dark Web hacks were a part of a global child porn bust
That FBI hacking initiative that caught 1,500 pedophiles on the Dark Web? It was just the tip of the iceberg. Motherboard has discovered that the operation was just one part of Operation Pacifier, a global campaign to fight child porn hidden through anonymity networks like Tor. The effort had the FBI hacking systems as far afield as Chile, Denmark and Greece -- there are also hints of possible operations in Colombia and Turkey. The US agency wasn't working alone, either, as it teamed up with Europol to collect information and pass it along to local law enforcement.

Police claim to have cracked extra-secure BlackBerry phones
BlackBerry smartphones have secure messaging as a matter of course, but for some that isn't enough: there are custom models that are even more secure thanks to PGP-encrypted mail. However, it seems that these locked down models aren't quite as safe as you'd think. The Netherlands Forensic Institute has confirmed a recent report that it's capable of scooping up encrypted data from PGP-equipped BlackBerry devices. It's not discussing the exact techniques involved, but it's relying on a tool from CelleBrite to get the job done. One possibility is that investigators are guessing the password based on a memory dump, although that normally requires yanking a memory chip off the phone's motherboard.

Social media led police straight to movie pirates
How can law enforcement agencies track down some of the world's most (in)famous pirates? The same way that we find out how our school frenemies are doing: stalking them on social media. TorrentFreak has investigated the recent convictions of three of the UK's biggest file-sharers to learn how exactly they were caught. It turns out that copyright enforcement officials are doing the same sort of armchair-sleuthing that we all do, only that they've got a hotline straight to the police.

The Silk Road bust almost didn't happen
Officials like to boast about taking down Silk Road creator Ross Ulbricht (aka Dread Pirate Roberts), but it turns out that they almost didn't get him at all. The New York Times has learned that the Internal Revenue Service's Greg Alford spent months sifting through chat logs and other details to link Ulbricht to the online black market, but the DEA and FBI didn't take the tax investigator's work seriously. If it weren't for his insistence on pursuing the case and reviewing evidence, Ulbricht might still be running the Dark Web service today.

Here are the devices law enforcement use to spy on you
The Intercept obtained the catalog of devices used by federal and local law enforcement to collect and monitor cell phone data. The tracking hardware -- including the infamous Stingray -- in the catalog is accompanied by its capabilities including, limitations, "planning factors," price and manufacturer. From handheld pieces of electronics that can track a few phones to boxes that can target as many as 10,000 unique cellphones the list is chilling reminder that even if you're not under investigation, you're being tracked if you're in the wrong place at the wrong time.

UK police try to scare teen hackers by visiting them at home
As you might have noticed, many teen hackers aren't easily deterred. Why would they be when they have a lot to prove, loads of peer pressure and little sense of the damage they're doing? British police think they have a way to scare those hackers straight, though. They've been visiting teens in person when the kids are near committing a crime that involves jail time, such as when they get access to a tool for denial of service attacks. Naturally, the hope is that they'll realize the police (and soon afterward, their parents) are watching and back off before they face charges.

FBI: Yes, we exploit unpatched security holes
It's no secret that the FBI uses tech tools like Stingray phone trackers to investigate suspects, but it's now clear that the bureau is willing to go even further than that. Operational Technology Division lead Amy Hess (above) tells the Washington Post that the FBI uses zero-day (that is, unknown by vendors) security software exploits for investigations -- the first time any official has admitted this on the record. The outfit doesn't prefer to use these hacks given how short-lived they are, Hess says, but they're still on the table.

California police use these biometric scanners
Police are increasingly turning to biometric tech in the field. It's supposed to help cops verify the identity of suspects, but there's a real concern that they could abuse this to get personal details on record -- and the Electronic Frontier Foundation wants you to know when this hardware might come into play. The rights group has published a report detailing the biometric scanners in use by California law enforcement, and they're in more widespread use than you might think. Mobile fingerprint readers are in use at several departments, and face recognition is getting traction. The Los Angeles County Sheriff's Department is using tattoo recognition, and some police departments are looking into iris scanning.

Hacking Team offers encryption breaking tools to law enforcement
Mere months after having more than 400 GB of confidential information stolen from its servers, spyware vendor Hacking Team has announced that it has resumed operations with a suite of digital tools to help law enforcement agencies get around pesky device encryption technology. In an email pitch sent to existing and potential new customers earlier this month, Hacking Team CEO David Vincenzetti, touted the company's "brand new and totally unprecedented cyber investigation solutions." The company has also been reportedly working on a revamped 10th edition of its proprietary Remote Control System, which constitutes the core of its software suite. There is no word, however, as to when RCS 10 will be made available. It also remains to be seen as to which, if any, law enforcement agencies will take Hacking Team up on its offer, given the company's recent security debacle. [Image Credit: Moment Editorial/Getty Images]

New DHS policy demands warrants before deploying Stingrays
The Department of Homeland Security announced a substantial policy change Wednesday regarding how it employs cellphone-tracking tools like the Stingray system. These cell-site simulators have been in use for more than a decade. They allow law enforcement to find cell phones either by directly searching for a known device or find an unknown device by sniffing for signaling information from the simulator's immediate vicinity and triangulating that data. The new policy explicitly demands that DHS personnel acquire a warrant before deploying the devices unless an exception, such as the imminent loss of human life, destruction of evidence, or to prevent the escape of a fugitive felon. Wednesday's announcement follows a similar decision by the Department of Justice last month. [Image Credit: Getty]

White House group considered four ways to unlock encrypted info
A group of law enforcement officials, intelligence agents and diplomats conjured up ways to access encrypted data over the summer, according to The Washington Post. The publication got its hands on a draft paper that details four techniques to bypass encryption that tech companies could use under court order. Among the four, the most alarming one is perhaps the proposal that suggests the use of software upgrades to introduce spyware into the target's device, because that sounds like it could be easily abused. Another idea is to add physical keys to phones that law enforcement can use to unlock them. The group also listed splitting encryption keys that can only be combined with the court's permission and having companies back up data to an unsecured location for access by authorities as other possible approaches.

DoJ shells out $23 million for the President's body camera pilot program
The Department of Justice announced last May that it would fund a national pilot program for law enforcement body cameras, a plan first put forth by President Obama. On Monday, the DoJ made good on that promise by awarding $23 million in grants to 32 states for the purchase of these devices. Of that total, $19.3 million will go towards actually purchasing the necessary 50,000 cameras, another $2 million is earmarked for training and the remaining $1.9 million will be used to conduct impact studies in Miami, Milwaukee and Phoenix.

Microsoft takes on the US government over data held overseas
Do you think that America's law enforcement agencies should have free access to the emails of your friends over in Ireland? It's the question that an appeals court is being asked to consider in a matter that has serious consequences for everyone in the world. The issue began when drug enforcement officials wanted to access to messages that were stored on a Microsoft server in Dublin. As far as Microsoft was concerned, that was a matter for the Irish government, but the g-people tried to hold the company's US arm accountable. Disturbingly, the US won the first two legal challenges, and now New York's 2nd circuit is about to hear to the appeal on behalf of Microsoft, with some cheering on from the rest of the technology industry.

LAPD's body cameras roll out Monday, but footage won't be public
Come Monday the Los Angeles Police Department begins its deployment of body cameras for officers. The initial rollout is limited -- only 860 of the proposed 7,000 cameras will hit the streets at first -- and the SWAT team won't get them until sometime after mid-September, according to The Los Angeles Times. The LAPD "doesn't plan on" making the recordings public unless a criminal or civil court case attached to them, though. The American Civil Liberties Union says that this blanket refusal to make all captured video public means that police departments can cherrypick what footage they do choose to distribute and essentially use it as PR for good deeds while keeping less-than-applause-worthy footage out of the limelight. Of course, one way around that would be setting up a YouTube channel like Seattle did, but that brings about its own set of critics. [Image credit: Associated Press]

North Dakota cops will be first in nation to use weaponized drones
North Dakota's Bill 1328 was supposed to be cut and dry. "In my opinion there should be a nice, red line: drones should not be weaponized. Period," Rep. Rick Becker (R-Bismarck), the bill's original sponsor, told a committee hearing back in March, per The Daily Beast. That was going to happen too, at least until an industry lobbying firm got involved. Now, law enforcement agencies in North Dakota are legally allowed to arm their UAVs with any manner of weapons, so long as they aren't "lethal".

Fitbit tracking data comes up in another court case
When you wear Fitbit or any other fitness tracker and smartwatch, you not only monitor your physical activities, you also collect data about yourself -- data that can apparently be used against you in investigations. In Lancaster, Pennsylvania cops responded to a 911 call by a woman who claimed she was raped by a home invader. The woman told the police she woke up around midnight with the stranger on top of her, and that she lost her tracker while struggling against her assailant. However, authorities found her Fitbit, which recorded her as active, awake and walking around all night. Combined with the evidence that was missing (tracks outside in the snow from boots she said the attacker was wearing, or any sign of them inside), an investigation led to her facing misdemeanor charges.






