ransomware
Latest

US government names North Korea as the source of WannaCry
Donald Trump's homeland security adviser, Tom Bossert, said in a Wall Street Journal op-ed that "after careful investigation, the U.S. today publicly attributes the massive "WannaCry" cyberattack to North Korea." Coming during increasing tensions between the two countries over nuclear threats and Twitter outbursts, Bossert said this attribution is based on evidence and agrees with the findings from the UK and Microsoft.

'Basic IT security' could have prevented UK NHS WannaCry attack
England's National Health Service (NHS) could have avoided the ransomware hack that crippled its systems in May, according to a government report. "Basic IT security" was all that was required to prevent the "unsophisticated" WannaCry attack, which affected more than a third of NHS organizations, said the National Audit Office (NAO). The full scale of the incident saw over 19,000 medical appointments canceled, and computers at 600 surgeries locked down.
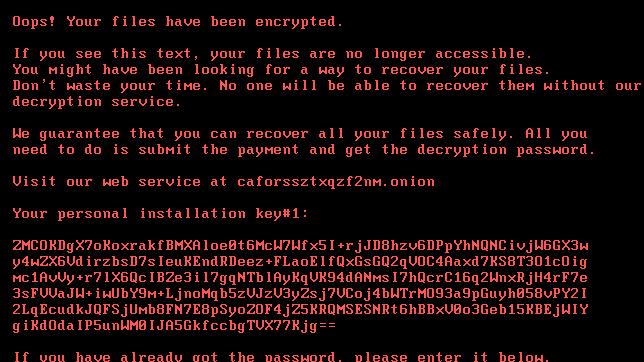
New ransomware is causing major issues across Europe and Russia
There's a new ransomware making the rounds today with confirmed targets in Russia, Ukraine, Turkey and Germany. Kaspersky Labs says that nearly 200 victims have been hit with the ransomware that's been dubbed Bad Rabbit.

FedEx estimates ransomware attack cost $300 million
FedEx acquired Dutch shipper TNT Express last year for $4.8 billion, well before the NotPetya ransomware ran wild on TNT's systems June 27th, disrupting much of its shipping operation. Like the earlier WannaCry outbreak, NotPetya used a Windows exploit stripped from an NSA leak to spread across networks. According to FedEx, even though its services and critical systems have been restored, "TNT Express volume, revenue and profit still remain below previous levels." That adds up to a $300 million hit on its operating results, and the company raised the estimate of integrating TNT's systems with its own by $75 million over previous estimates.

Ransomware attacks hit small businesses the hardest
If it seems like reports of ransomware attacks -- malicious software that holds data hostage unless a ransom is paid to the person or organization behind it -- are increasing, Malwarebytes agrees with you. The company released its Second Annual State of Ransomware Report recently. Among the findings is that 22 percent of small business that were hit with ransomware attacks were crippled to the point they had to cease operations immediately.

The hot new cyberattack that's sweeping the nation
On Tuesday, a powerful and terrifying new cyberattackworm emerged in Ukraine, quickly spreading to the Russian Federation and other countries no one cared enough to report on because they weren't the US. It was hard to tell which infection was worse: The cyberattack itself or the race to write and publish something (anything!) about it, framing it just like the last "massive" cyberattack explosion to hit the whole world.

India wants a discount on Windows to reduce its cyberattack risk
In light of the recent WannaCry and "NotPetya" global ransomware attacks, India is looking to strike a deal with Microsoft that would reduce the cost of its Windows 10 operating system by more than 75 percent. The country's cyber security coordinator, Gulshan Rai, told Reuters that the company has "in principle agreed."

Windows 10 preview build protects your files from ransomware
Microsoft's latest Windows 10 Preview Build for Insiders in the Fast ring introduces what's obviously meant as a response to all the ransomware attacks targeting the platform these days. The build comes with a new feature called "controlled folders" that can protect their files from malicious apps and other threats. Windows closely monitors any changes made to anything in a controlled folder, so if any malware or blacklisted application tries to modify a file, they'll get a notification that something fishy's going on. To activate the feature, Insiders will have to toggle it on in the Windows Defender Security Center under the Virus & threat protection settings section.

Recent 'NotPetya' attacks might not be ransomware at all
The companies and agencies hit by a cyberattack in the Ukraine, Russia, the US, parts of Europe, Asia and Australia might never be able to recover their data. See, some security researchers, including Kaspersky Lab, believe that the malware that invaded those computers was only masquerading as ransomware in order to lure the media into covering it as a follow-up to the WannaCry incidents. While its developers painstakingly tried to make it look like ransomware, the researchers say it's actually what you call a "wiper," since it overwrites parts that a disk needs to run. It doesn't encrypt those parts, so you can regain access to them after you pay -- it just completely erases them.

WannaCry ransomware causes Honda plant to shut down
WannaCry isn't done yet. Honda Motor Co. had to shut down its Sayama plant on Monday after finding the ransomware in its computer network. The plant's production resumed on Tuesday.

US: North Korea's been hacking everyone since 2009
US authorities believe the North Korean government has been using an army of hackers called "Hidden Cobra" to deploy cyber attacks over the past eight years. That's according to the Technical Alert formally issued by the Homeland Security and the FBI, which contains the details and tools NK's cyber army has been using to infiltrate the media, financial, aerospace and critical infrastructure sectors in the US and around the globe. The government agencies issued the alert after tracing the IP addresses of a malware variant used to manage NK's DDoS attacks to North Korean computers. While other players can spoof their IPs to frame NK, the US is encouraging cyber analysts to be on the lookout, warning them that the Asian country will continue to use cyber operations to advance its government's military and strategic objectives.
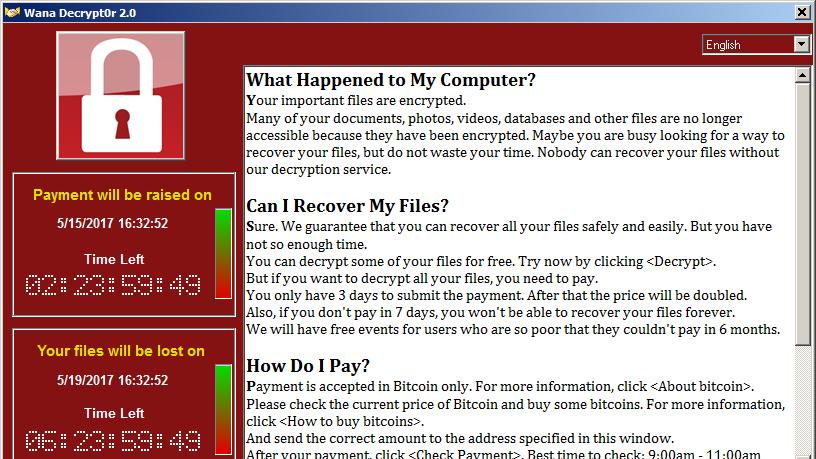
There's an easy fix for WannaCry, if you haven't rebooted yet
There's a glimmer of hope for a specific subset of victims in the WannaCry hack. Security researchers have released a fix that gets rid of the ransomware and restores a device's files, though it only works on Windows XP to Windows 7, and only on computers that have not been rebooted since the infection.
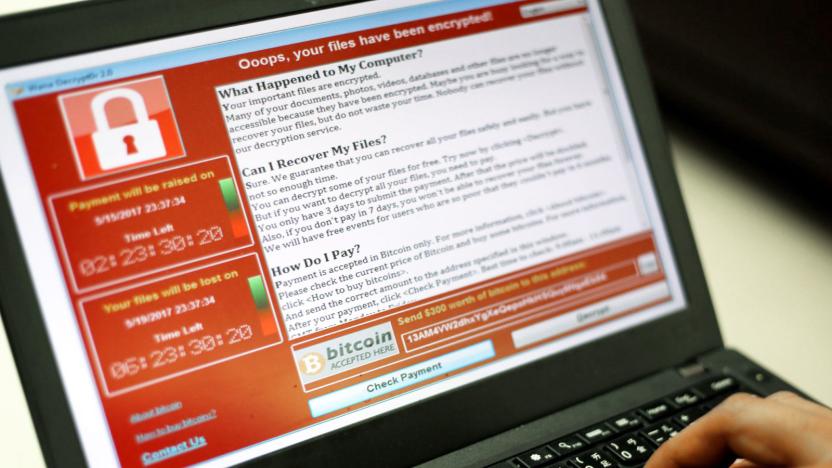
NSA would have to disclose its cyber exploit policies under new bill
It wasn't long after last week's devastating international ransomware attack before details surfaced about how the hackers found the exploit to target: It was stolen from the NSA, which stockpiles the digital vulnerabilities. Now, Democratic Senator Brian Schatz (HI) has introduced a bill that would create policy regulating how and when federal agencies would disclose known attack vectors.
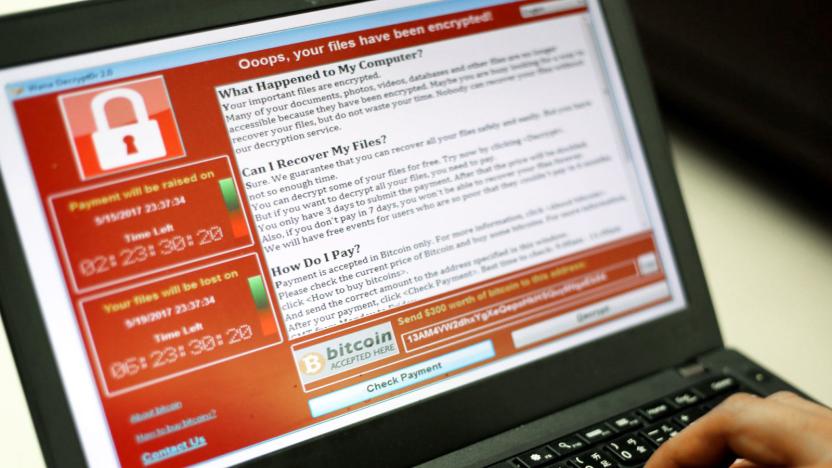
Pirated Windows led to WannaCry's spread in China and Russia
WannaCry, the notorious ransomware demanding up to $300 worth of Bitcoins to unlock victims' computers, hit systems all around the globe over the weekend. According to Finnish cybersecurity company F-Secure, though, Russia and China were affected the most, and it could be due to the rampant use of pirated software in those countries. Microsoft issued a patch for the vulnerability the attackers used as an entry point back in March and even fixed it for XP, which it long stopped supporting. However, pirated systems can't install those patches, so computers running illegal software remained vulnerable.

'WannaCry' ransomware showed traces of North Korean code
For all the damage the "WannaCry" ransomware has done, there's still one looming, unanswered question: who's behind it? At last, there might be a clue. Google researcher Neel Mehta has noticed that an early version of WannaCry's code shares similarities with a February 2015 sample from the Lazarus Group, a North Korea-linked outfit blamed for both the Sony Pictures hack as well as the Bangladesh Bank heist. The code changed between then and now, but it at least raises the possibility that North Korea was involved.

The 'WannaCry' ransomware is a stark reminder of a broken system
In April, a hacking group called The Shadow Brokers dumped a cache of Windows' exploits it pilfered from the NSA. The group had decided to start leaking exploits it stole from the agency after it was unable to find a buyer for the government's hacking tools. Inside that April drop was a remote code execution vulnerability called "EternalBlue" (aka MS17-010). Fortunately, Microsoft issued a security patch that fixed EternalBlue in March. What's not so fortunate is that not everyone had applied it to their machines.

NHS Trusts ignored patch that would’ve averted malware disaster
The ransomware attack that crippled crucial NHS systems across the UK and continues to cause disruption could have easily been contained, according to NHS Digital. The body, which oversees data and IT infrastructure across the NHS, said hospitals and other arms of the service had ample time to upgrade their systems. The 'WannaCry' malware variant used a Windows exploit Microsoft patched in mid-March this year. At the end of April, NHS Digital notified staff and "more than 10,000 security and IT professionals," pointing them to a patch that would "protect their systems." It seems this advisory fell on some deaf ears, which explains why only certain NHS Trusts were affected.

Engadget Podcast Ep 39: Rip Off
On this episode hosts Dana Wollman and Terrence O'Brien talk about the massive WannaCry ransomware attack spreading across the globe and Caddyshack. Edgar Alvarez stops by to fill everyone in on all the drama around Fyre Festival, Instagram influencers and the FTC. Then Cherlynn Low and Devindra Hardawar check in from Build to give us the low down on Microsoft's plans for the future.

Microsoft blasts spy agencies for hoarding security exploits
Microsoft is hopping mad that leaked NSA exploits led to the "WannaCry" (aka "WannaCrypt") ransomware wreaking havoc on computers worldwide. Company President Brad Smith has posted a response to the attack that roasts the NSA, CIA and other intelligence agencies for hogging security vulnerabilities instead of disclosing them to be fixed. There's an "emerging pattern" of these stockpiles leaking out, he says, and they cause "widespread damage" when that happens. He goes so far as to liken it to a physical weapons leak -- it's as if the US military had "some of its Tomahawk missiles stolen."
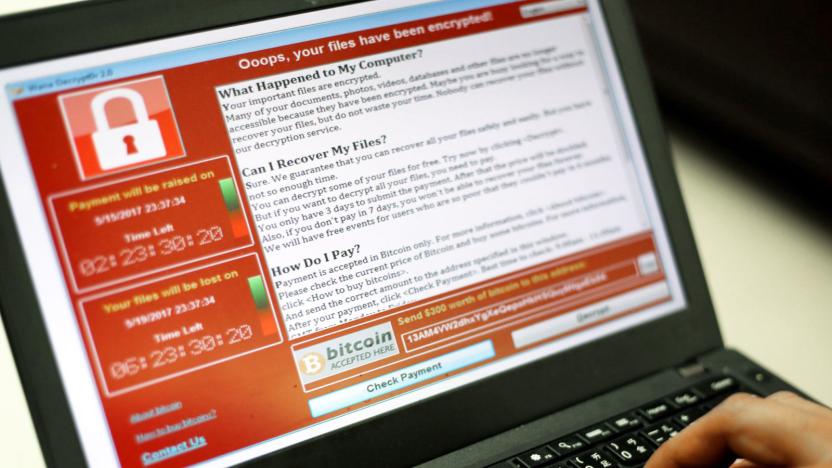
'WannaCry' ransomware evolves despite attempts to kill it
There were predictions that the fast-spreading "WannaCry " (aka "WannaCrypt") ransomware would quickly evolve to get around its domain-based kill switch, and, well... the predictions were right. Security researchers have discovered variants of the Windows malware that either have different kill switches (easy to stop by purchasing the web domain) or don't have a kill switch at all. MalwareTech's initial findings might have stopped the original WannaCry in its tracks, but that was really just a speed bump for malicious coders.











