worm
Latest

Older Fire TV devices get improved protection against Android malware
It came to light earlier this year that a virus was attacking Fire TV devices because of an Android-based vulnerability relating to ADB (Android Debug Bridge) connections. But part of the newest software update, 5.2.6.6, should make things a lot more secure, no matter how you've been playing around with your device's developer options.
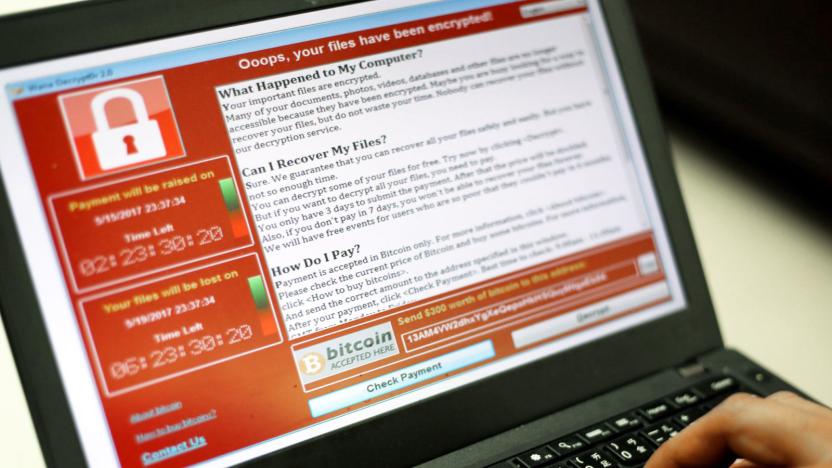
'WannaCry' ransomware evolves despite attempts to kill it
There were predictions that the fast-spreading "WannaCry " (aka "WannaCrypt") ransomware would quickly evolve to get around its domain-based kill switch, and, well... the predictions were right. Security researchers have discovered variants of the Windows malware that either have different kill switches (easy to stop by purchasing the web domain) or don't have a kill switch at all. MalwareTech's initial findings might have stopped the original WannaCry in its tracks, but that was really just a speed bump for malicious coders.

Microsoft just fixed a serious Windows Defender bug
Over the weekend, Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich tweeted about discovering "the worst Windows remote code exec in recent memory." According to Ormandy, it could work against a default installation and even become "wormable" -- able to replicate itself on a targeted machine and then spread to other computers automatically. Now we know more about what the problem is since, in just two days, Microsoft's Security Response Center and Windows Defender developers were able to come up with a fix that is now available via Windows Update for Windows 7, 8.1, RT and 10 (according to Microsoft, the Control Flow Guard security feature lowers the risk of this attack on 8.1 and 10), as well as other versions that IT professionals may be more familiar with.

Hackers hijack Philips Hue lights with a drone
Surprise! The Internet of Things is a security nightmare. Anyone who was online a few weeks ago can attest to that. The massive internet blackout was caused by connected devices, and new research from white-hat hackers expounds upon those types of vulnerabilities. The target? Philips Hue smart lightbulbs. While they've been hacked in the past, Philips was quick to point out that it happening in a real-world situation would be pretty difficult. Digital intruders would need to already be on your home network with a computer of their own -- the company claimed that directly attacking the lightbulbs wasn't exactly feasible. But this new attack doesn't require that sort of access.

Apple bought the company that exposed its flawed firmware
What do you do when researchers create a worm that infects your company's firmware? If you're Apple, you buy the researchers. Last August, news broke of a exploit named "Thunderstrike 2." Delivered by a simple link, the worm could silently modify a Mac's firmware, meaning that even an OS reinstall wouldn't remove it. Thankfully, the researchers responsibly informed Apple of the issue, and the company had mostly solved this particular problem before it went public.

Scientists control a worm's brain cells using sound waves
Forget using clunky headsets and implants to control brain cells... one day, you might only need to use sound waves and some chemicals. Salk Institute scientists have found a way to control the brain cells of a tiny nematode worm through ultrasound. All they need to do to trigger activity is add a membrane ion channel to a neuron cell and blast it with ultrasonic waves -- in this experiment, the researchers changed the worm's direction through sound bursts. The approach is not only relatively unintrusive, but can reach deep into the body. You could trigger neural activity without ever hooking up an electrode, even for much larger animals.

State-backed spyware targets antivirus maker, Iranian nuclear talks
The threat posed by state-sponsored malware might be even larger than first thought. Antivirus developer Kaspersky Lab says it discovered an attack on its network by allegedly government-made spyware that appears to be an upgraded version of Duqu, the Stuxnet-based worm used by Israel and the US to derail Iran's nuclear efforts. This "Duqu 2.0" not only tried to obtain details about Kaspersky's investigations and detection abilities, but remained remarkably stealthy. Pre-release software was necessary to catch it, and there were attempts to throw researchers off the scent by suggesting that China or Eastern Europe was to blame.

Digitally simulated worm wriggles for the first time (video)
It's relatively easy to simulate life in an abstract sense, but it's tricky to do that cell by cell -- just ask the OpenWorm Project, which has spent months recreating a nematode in software. However, the team recently cleared an important milestone by getting its virtual worm to wiggle for the first time. The project now has an algorithm that triggers the same muscle contractions you'd see in the real organism, getting the 1,000-cell simulation to "swim" in a convincing fashion. There's still a long way to go before OpenWorm has a complete lifeform on its hands, mind you. The group has to introduce code for a nervous system, and performance is a problem -- it takes 72 hours to emulate one-third of a second's worth of activity. If all goes well, though, you'll eventually get to play with the worm through a browser. In the meantime, you can check out the digital critter's motion in a video after the break.

Symantec: work on Stuxnet worm started two years earlier than first thought
Most of us think we know the tale of Stuxnet: it's a possibly government-sponsored worm that played havoc with Iranian centrifuges in 2009, setting back the country's uranium enrichment program without involving any traditional weapons. Researchers at Symantec, however, now claim there's an untold narrative. They've discovered a Stuxnet 0.5 version that may have been in development or active as soon as November 2005, two years before the commonly accepted timeline. It first surfaced on trackers in November 2007, and would have created wider-ranging chaos at Iran's Natanz nuclear facility by closing vital pressure valves instead of using the subtler centrifuge technique. Symantec also noticed that this pre-1.0 malware shares traits with the Flamer code base, putting it in the context of an even larger effort than seen so far. Moreover, it would have required extensive knowledge of the Natanz infrastructure -- this was no casual attack, according to the researchers. While we may never know exactly what prompted the revamp, IAEA evidence suggests that Stuxnet wasn't truly effective until the better-known version came into play. We mostly know that modern cyberwarfare had its fair share of growing pains -- and that it's not as fresh-faced as we assumed.

Alt-week 9.29.12: 3D pictures of the moon, 4D clocks and laser-controlled worms
Alt-week peels back the covers on some of the more curious sci-tech stories from the last seven days. Dimensions, they're like buses. You wait for ages, and then three come along at once. And then another one right after that. While that might be about where the analogy ends, this week sees us off to the moon, where we then leap from the third, right into the fourth. Once there, we'll learn how we could eventually be controlled by lasers, before getting up close and personal with a 300 million-year old bug. Sound like some sort of psychedelic dream? Better than that, this is alt-week.

Researchers create Meshworm robot, beat it up (video)
We've seen a number of options for controlling real worms, but never a worm robot, until now. Enter Meshworm, the latest creation from researchers at MIT, Harvard University and Seoul National University. The bot is made from "artificial muscle" composed of a flexible mesh tube segmented by loops of nickel / titanium wire. The wire contracts and squeezes the tube when heated by a flowing current, but cut the power and it returns to its original shape, creating propulsion in a similar way to its living kin. Taking traditional moving parts out of the equation also makes it pretty hardy, as proven by extensive testing (read: hitting it with a hammer). DARPA is known for getting its fingers in all sorts of strange pies, and it also supported this project. We can't see it being the fastest way of gathering intel, but the potential medical applications, such as next-gen endoscopes, sound plausible enough. Full impact tests in the video after the break.

Kaspersky Lab: Apple is '10 years behind Microsoft' on security
Kaspersky founder and CEO Eugene Kaspersky told Computer Business Review that malware targeting the Mac is beginning to grow and Apple needs to take notice. The CEO said Apple is "ten years behind Microsoft in terms of security," and asserts that Apple must change its approach towards security soon. He said, Apple "will have to make changes in terms of the cycle of updates and so on and will be forced to invest more into their security audits for the software." I don't have any doubt that Apple will be able to plug holes that may be discovered in OS X or third-party software, just like it did with the latest Flashback exploit that targeted a Java vulnerability.

Twenty percent of Macs examined infected with Windows malware
Sophos looked at 100,000 Mac computers and found that one in every five has some form of malware. This might sound alarming, but before you stare at your machine in disgust, you should get some perspective. The survey looked at 100,000 OS X machines that are running Sophos's free Mac anti-virus software. Sophos found that this 20 percent figure is for malware that targets Windows-based computers. Though it can be used as a vector to infect other Windows machines, it won't affect Mac users on OS X. Sophos did find that 1 in 36 Macs (2.7 percent) were infected with OS X malware. Though less than 3 percent may be concerning, it's not as alarming as the 20 percent figure that's making its way into headlines.

Visualized: preconceived notions about personal computer security
See that chart up there? That's a beautiful visualization of a dozen folk models surrounding the idea of home computer security, devised by Michigan State's own Rick Wash. To construct it (as well pen the textual explanations to back it), he interviewed a number of computer users with varying levels of sophistication, with the goal being to find out how normal Earthlings interpreted potential threats to their PC. His findings? A vast amount of home PCs are frequently insecure because "they are administered by untrained, unskilled users." He also found that PCs remain largely at risk despite a blossoming network of preventative software and advice, and almost certainly received an A for his efforts. Hit the source link for more, but only after you've spiffed up, thrown on a pair of spectacles and kicked one foot up on the coffee table that sits in front of you.

Harvard University controls worm with laser, we wait for choreographed dance moves (video)
Researchers at Harvard University's Center For Brain Science have successful manipulated nematode C. elegans worms by genetically modifying a select few of their 302 neurons. Not to be confused with magnetically controlled invertebrate, these creepy-crawlies are controlled by the CoLBeRT system (a nod to the comedian but no other relation), controlling locomotion and behavior in real time. The scientists can manipulate movement of the worms, induce paralysis, and even cause them to lay eggs all by shining a laser that turns on and off the modified cells at will. The laser hits the worm and causes it to react as if it were being touched. According to the researchers, the reaction is similar to when light is shined in a human eye -- the protein found in the worm and eyes are sensitive to different variations of rays and will respond based on the color shined. Peep past the break for some squiggly mind- er, light-controlled action.

AT&T, Verizon, RIM get serious about security for mobile devices
As commonplace as smartphones have become, it's about time that carriers and manufacturers start getting serious about mobile security (and no, we don't mean iPhone tethers). According to a recent Wall Street Journal article, Verizon is currently working with Lookout, a San Francisco-based company known for remote backup and geolocation apps for BlackBerry, Android, and Windows Mobile devices, while RIM has recently announced a little something called BlackBerry Protect, which promises to lock or even wipe a misplaced phone, pinpoint the thing on a map, and make regularly-scheduled wireless backups. By far the most ambitious plans in the article, however, belong to AT&T, which -- aside from recent deals with MobileIron and McAfee -- is currently opening a new mobile security lab in New York City. From here, the company will research malware, worms, viruses, and other threats as they develop in the mobile sphere. "Everyone is realizing that this is an uncontrolled environment," said AT&T chief security officer Edward G. Amoroso. "We don't want to have the same problems that we had with PCs."

Cambridge scientists develop lower-than-low power WORM memory
Researchers at Cambridge University have recently published a paper on their new type of WORM (write once read many) memory which is even more low powered than the ones that came before it. The new electron-only design of the memory is solution processed, making it low cost as well as it requires no lithography. The device, using ZnO semiconductor nanoparticles to inject electrons into a polymer which is capable of conducting. The electrons are then used to program the memory by permanently lowering the conductivity of the polymer, producing insulation. This result is far lower power densities than previously recorded, by orders of magnitude. The research team believes that it can make further improvements to the device as they continue to work.

Researchers remotely control worms using magnetic nanoparticles, tomorrow: people?
Researchers at the University at Buffalo have announced they've found a way to remotely control worms using magnetic nanoparticles attached to cell membranes, and say they can cause the worms to stop moving simply by exposing the particles to a magnetic field and heating them up. This, they say, could lead to a host of medical benefits -- but if The X-Files has taught us anything, it's that remote-controlled nanotechnology can also fall into the wrong hands, and make people stop moving.

SanDisk's 1GB WORM SD card stores evidence longer than your prison sentence (video)
You can think of SanDisk's latest WORM SD card like a mini time capsule... for criminals. As the name implies, these write-once-read-many cards are tamperproof slivers of flash storage that can only be written to once by an SD WORM-compatible device like, say, those security cameras, witness voice recorders, and photo cameras used by the police. SanDisk claims that the data will still be readable after 100 years, long after you and your crimes have been forgotten. Why the fuss after not hearing about SanDisk's SD WORM ambitions since 2008? Well, Sandisk just announced that Japan's police force will use the SanDisk SD WORM card "as the storage media of choice for tamper-proof forensic image archiving." We suspect that the Yakuza will be getting right on that "tamper-proof" claim just as soon as they finish viewing the video embedded after the break.

New jailbroken iPhone worm is malicious
Last month a Dutch iPhone user demonstrated how careless jailbreaking can cause trouble. Namely, after finding users who enabled SSH with the phone's default password intact, he sent those phones a message that read, "Your iPhone's been hacked because it's really insecure! Please visit doiop.com/iHacked and secure your iPhone right now! Right now, I can access all your files." A similar worm caused phones to rickroll their owners. They could have done worse. This week, someone has. Again from the Netherlands and again finding jailbroken iPhones with SSH enabled, F-secure reports that this infraction puts up an ING Direct login page that lets the hacker gather login credentials and, we assume, move funds to wherever they please. This version also changes the 'alpine' password to block users from getting to the phone via SSH. We'll have more on this as the story develops, but the moral is this: If you jailbreak your iPhone, you should know what you're doing -- and you should change your SSH password. [via Engadget & ZDnet Asia]










